Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
What is MAC Address
- MAC address is the physical address, which uniquely identifies each device on a given network. To make communication between two networked devices, we need two addresses: IP address and MAC address. It is assigned to the NIC (Network Interface card) of each device that can be connected to the internet.
- It stands for Media Access Control, and also known as Physical address, hardware address, or BIA (Burned In Address).
- It is globally unique; it means two devices cannot have the same MAC address. It is represented in a hexadecimal format on each device, such as 00:0a:95:9d:67:16.
- It is 12-digit, and 48 bits long, out of which the first 24 bits are used for OUI(Organization Unique Identifier), and 24 bits are for NIC/vendor-specific.
- It works on the data link layer of the OSI model.
- It is provided by the device's vendor at the time of manufacturing and embedded in its NIC, which is ideally cannot be changed.
- The ARP protocol is used to associate a logical address with a physical or MAC address.
Reason to have both IP and MAC addresses.
As we already had the IP address to communicate a computer to the internet, why we need the MAC address. The answer to this question is that every mac address is assigned to the NIC of a hardware device that helps to identify a device over a network.
When we request a page to load on the internet, the request is responded and sent to our IP address.
Both MAC and IP addresses are operated on different layers of the internet protocol suite. The MAC address works on layer 2 and helps identify the devices within the same broadcast network (such as the router). On the other hand, the IP addresses are used on layer 3 and help identify the devices on different networks.
We have the IP address to identify the device through different networks, we still need a MAC address to find the devices on the same network.
Why should the MAC address be unique in the LAN network?
If a LAN network has two or more devices with the same MAC address, that network will not work.
Suppose three devices A, B, and C are connected to a network through a switch. The MAC addresses of these devices are 11000ABB28FC, 00000ABB28FC, and 00000ABB28FC, respectively. The NIC of devices B and C have the same MAC address. If device A sends a data frame to the address 00000ABB28FC, the switch will fail to deliver this frame to the destination, as it has two recipients of this data frame.
We can understand this example with the below image:
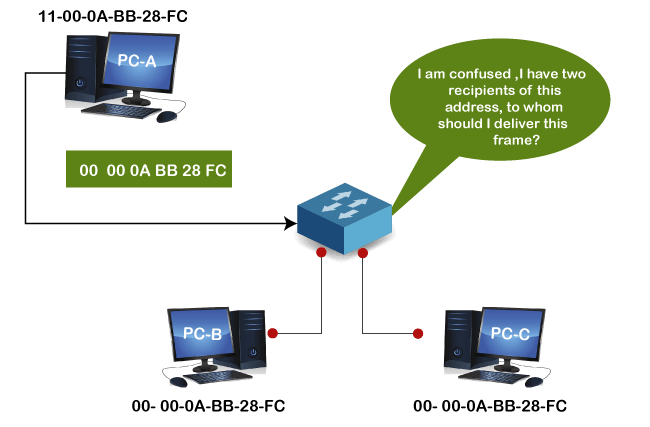
Format of MAC address
As we have already discussed in the above section, we cannot assign the MAC address to the device's NIC; it is preconfigured by the manufacturers. So, let's understand how it is configured and what format is selected.
- It is 12 digits or 6-byte hexadecimal number, which is represented in colon-hexadecimal notation format. It is divided into six octets, and each octet contains 8 bits.
- The first three octets are used as the OUI or Organisationally Unique Identifier. These MAC prefixes are assigned to each organization or vendor by the IEEE Registration Authority Committee.
- Some example of OUI of known vendors are:
CC:46:D6 - Cisco
3C:5A:B4 - Google, Inc.
3C:D9:2B - Hewlett Packard
00:9A:CD - HUAWEI TECHNOLOGIES CO.,LTD
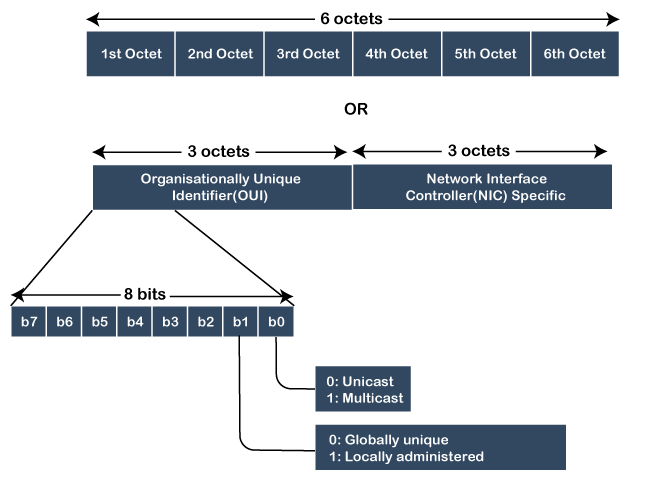
- The last three octets are NIC specific and used by the manufacturer to each NIC card. Vendors or manufacturers can use any sequence of digits to the NIC specific digits, but the prefix should be the same as provided by the IEEE.
- The MAC address can be represented in below three formats:
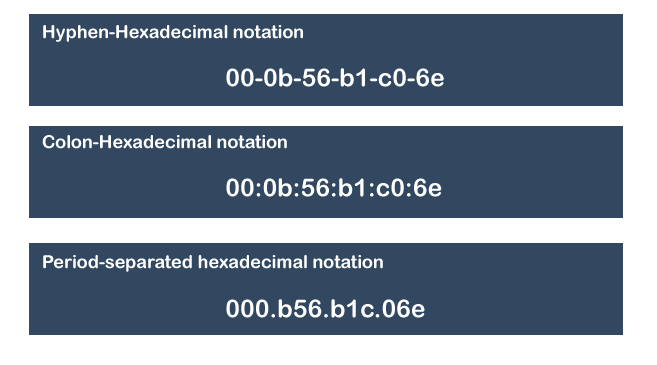
Types of MAC address
There are three types of MAC addresses, which are:
- Unicast MAC Address
- Multicast MAC address
- Broadcast MAC address
Unicast MAC address:
The Unicast MAC address represents the specific NIC on the network. A Unicast MAC address frame is only sent out to the interface which is assigned to a specific NIC and hence transmitted to the single destination device. If the LSB (least significant bit) of the first octet of an address is set to zero, the frame is meant to reach only one destination NIC.
Multicast MAC Address:
Multicast addresses enables the source device to transmit a data frame to multiple devices or NICs. In Layer-2 (Ethernet) Multicast address, LSB (least significant bit) or first 3 bytes of the first octet of an address is set to one and reserved for the multicast addresses. The rest 24 bits are used by the device that wants to send the data in a group. The multicast address always starts with the prefix 01-00-5E.
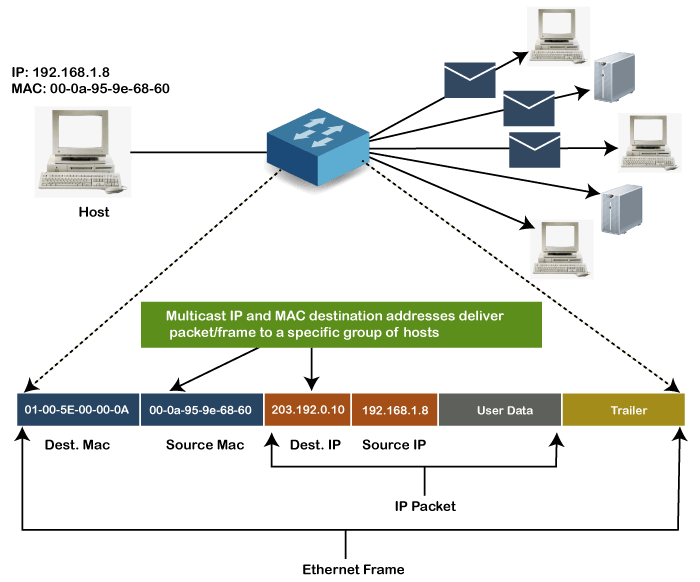
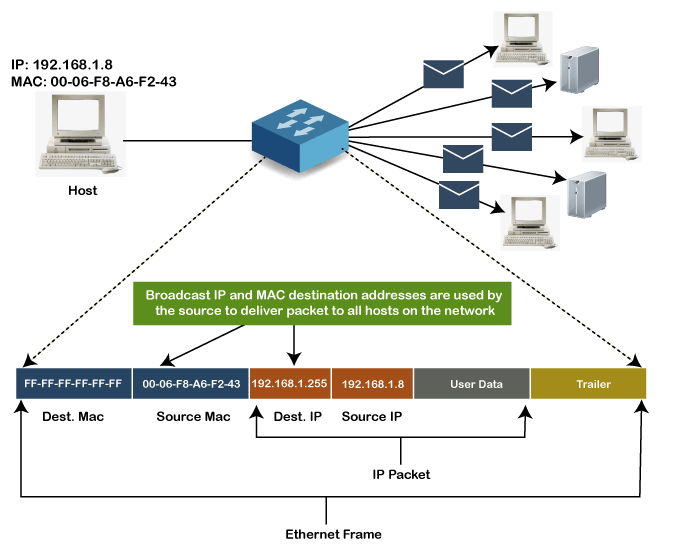
Broadcast MAC address
It represents all devices within a Network. In broadcast MAC address, Ethernet frames with ones in all bits of the destination address (FF-FF-FF-FF-FF-FF) are known as a broadcast address. All these bits are the reserved addresses for the broadcast. Frames that are destined with MAC address FF-FF-FF-FF-FF-FF will reach every computer belong to that LAN segment. Hence if a source device wants to send the data to all the devices within a network, that can use the broadcast address as the destination MAC address.
How to find the MAC address of a device
We can easily find or check the address of our computer device with any operating device. Every device connected to the home network contains a unique MAC address, but if your system has multiple network adapters, such as an Ethernet adapter or wireless adapter, each adapter or NIC has its own MAC address or physical address.
Follow the below steps to find the MAC addresses of a device on a different OS.
MAC address on Windows:
1. Click Window Start or Press the Windows Key.
2. In the given search box, type cmd to open the command prompt.
3. Press the Enter key, and the command prompt window will display, as shown below image:
4. Type ipconfig/all command and press enter.
5. It will show different information, scroll down and look for the physical address. Each physical address is the MAC address of your device.
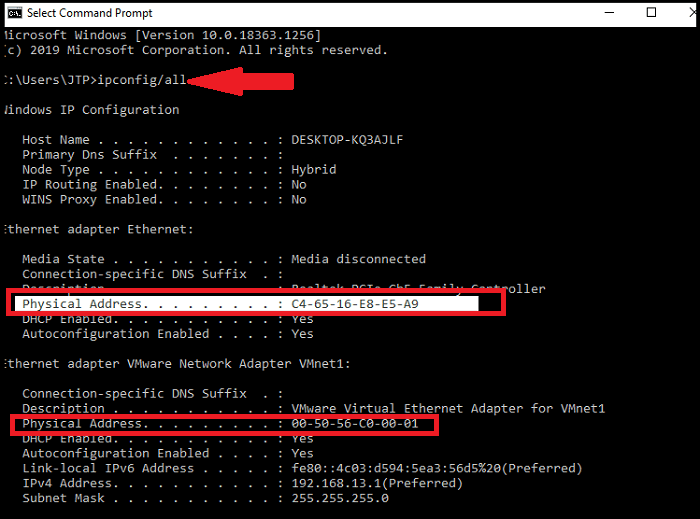
As we can see in the above image, there are two physical addresses shown with different values, one is for the Ethernet adapter, and the other one is for the VMware network adapter.
MAC address on Macintosh OS:
Follow the below steps to find the MAC address on the Macintosh OS:
- Select the Apple icon or open the Apple Menu, and click on System Preferences.
- Under system preferences → Select Network →
- The above path will open a network box.
- Select the Wi-Fi option from here. It will show the Wi-Fi address or Airport Address displays; it is the MAC address of your device.
Cloning of MAC address
MAC cloning is a way to fix the connectivity issues of the device with ISP. In this method, we need to set the MAC address of a device WAN port to be the similar MAC address of your PC or another device.
The connectivity issue arises mainly when we add new MAC address to a network, and this issue can be fixed with the help of MAC cloning.
For example, Some ISPs use the MAC address of your device when the service is installed. Now, if we place a router behind the cable modem or DSL modem, the ISP will not recognize the MAC address from the device's WAN port. For such a case, either you can call to ISP provider to register the MAC of your device, or you can clone the MAC address of the WAN port to the same as the computer MAC address.
Difference between MAC address and IP address
Both the MAC address and IP address are the way to identify the device on the network. Following are some important differences between both:
| MAC address | IP address |
|---|---|
| It stands for Media Access Control. | It stands for Internet Protocol. |
| It is the unique address provided by the manufacturer. | It is the logical address provided by the ISP or Internet Service Provider. |
| It is the physical address of the device's NIC that is used to identify a device within a network. | It is the logical address that identifies a network or device on the internet. |
| It operates on the data link layer. | It operates on a network Layer. |
| It is the 6 -bytes hexadecimal address. | It is of 4 bytes for IPv4 and 8 bytes for IPv6 addresses. |


