Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
URI vs URL
While surfing the internet or checking any website, you may have encountered the words "URI" and "URL" multiple times. These are the two important concepts of web and are mostly used interchangeably. But they are not the same as each other; the main difference between URI and URL is that URI can represent both URL and URN of a resource simultaneously, whereas URL can only specify the address of the resource on the internet. In this topic, we will see URI and URL individually and how both can be differentiated from each other.
What is URI?
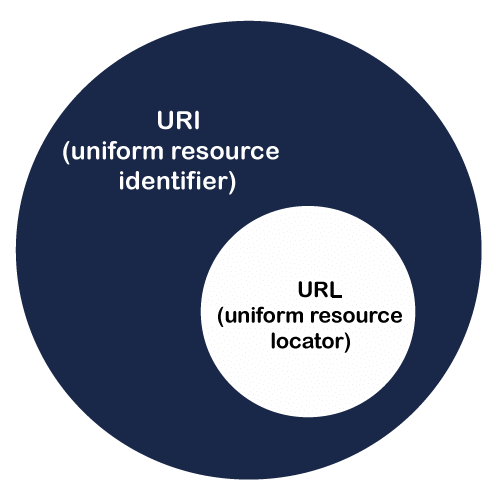
A URI or Uniform Resource Identifier is a string identifier that refers to a resource on the internet. It is a string of characters that is used to identify any resource on the internet using location, name, or both.
A URI has two subsets; URL (Uniform Resource Locator) and URN (Uniform Resource Number). If it contains only a name, it means it is not a URL. Instead of directly URI, we mostly see the URL and URN in the real world.
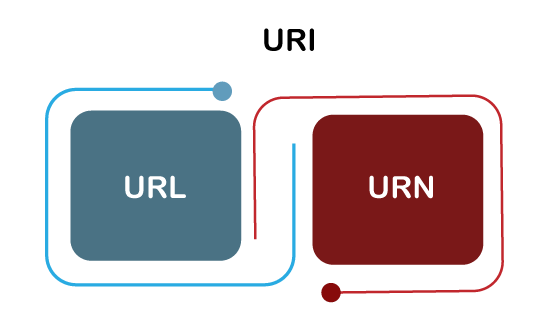
A URI contains scheme, authority, path, query, and a fragment. Some most common URI schemes are HTTP, HTTPs, ftp, Idap, telnet, etc.
Syntax of URI
The Syntax of URI is given below:
- scheme:[//authority]path[?query][#fragment]
- Scheme: The first component of URI is scheme that contain a sequence of characters that can be any combination of letter, digit, plus sign, or hyphen (_), which is followed by a colon (:). The popular schemes are http, file, ftp, data, and irc. The schemes should be registered with IANA.
- Authority: The authority component is optional and preceded by two slashes (//). It contains three sub-components:
- userinfo: It may contain a username and an optional password separated by a colon. The sub-component is followed by the @ symbol.
- host: It contains either a registered name or an IP address. The IP address must be enclosed within [] brackets.
- Port: Optional
- Path: It consists of a sequence of path segments separated by a slash(/). The URI always specifies it; however, the specified path may be empty or of 0 lengths.
- Query: It is an optional component, which is preceded by a question mark(?). It contains a query string of non-hierarchical data.
- Fragment: It is also an optional component, preceded by a hash(#) symbol. It consists of a fragment identifier that provides direction to a secondary resource.
Some examples of URI
- mailto:hey.Doe@example.com
- news:comp.infosystems.www.servers.unix
- urn:oasis:names:specification:docbook:dtd:xml:4.1.2
What is the URL?
A URL or Uniform Resource Locator is used to find the location of the resource on the web. It is a reference for a resource and a way to access that resource. A URL always shows a unique resource, and it can be an HTML page, a CSS document, an image, etc.
A URL uses a protocol for accessing the resource, which can be HTTP, HTTPS, FTP, etc.
It is mainly referred to as the address of the website, which a user can find in their address bars. An example of an URL is given below:

Note: All URLs can be URIs, but all URIs cannot be URLs. It is because a URI contains both URL and URN and represent URL or URN, or both.
Syntax of URL
Each HTTP URL follow the syntax of its generic URI. Hence the syntax of the URL is also similar to the syntax of URI. It is given below:
- scheme:[//authority]path[?query][#fragment]
The above URL is made up of the following components:
- Scheme: The URL's first component is a scheme, which represents a protocol that a browser must need to use to request the resource. The commonly used protocols for websites are HTTP or HTTPS.
- Authority: The authority includes two sub-components, domain name and Port, separated by a colon. The domain name can be anything, the registered name of the resource like javatpoint.com, and port is the technical gate to access the resource on a webserver. The port number 80 is used for HTTP and 443 is used for HTTPS.
- Path: The path indicates the complete path to the resource on the webserver. It can be like /software/htp/index.html.
- Query String: It is the string that contains the name and value pair. If it is used in a URL, it follows the path component and gives the information. Such as "?key1=value1&key2=value2".
- Fragment: It is also an optional component, preceded by a hash(#) symbol. It consists of a fragment identifier that provides direction to a secondary resource.
Key differences between URI and URL
- URI contains both URL and URN to identify the name and location or both of a resource; in contrast, URL is a subset of URI and only identifies the location of the resource.
- The example of URI is urn:isbn:0-476-27557-4, whereas the example of URL, is https://google.com.
- The URI can be used to find resources in HTML, XML, and other files also, whereas, URL can only be used to locate a web page.
- Each URL can be a URI, whereas all URIs cannot always be URLs.
Difference chart between URI and URL
| URI | URL |
|---|---|
| URI is an acronym for Uniform Resource Identifier. | URL is an acronym for Uniform Resource Locator. |
| URI contains two subsets, URN, which tell the name, and URL, which tells the location. | URL is the subset of URI, which tells the only location of the resource. |
| All URIs cannot be URLs, as they can tell either name or location. | All URLs are URIs, as every URL can only contain the location. |
| A URI aims to identify a resource and differentiate it from other resources by using the name of the resource or location of the resource. | A URL aims to find the location or address of a resource on the web. |
| An example of a URI can be ISBN 0-486-35557-4. | An example of an URL is https://www.javatpoint.com. |
| It is commonly used in XML and tag library files such as JSTL and XSTL to identify the resources and binaries. | It is mainly used to search the webpages on the internet. |
| The URI scheme can be protocol, designation, specification, or anything. | The scheme of URL is usually a protocol such as HTTP, HTTPS, FTP, etc. |
Conclusion
As per the above discussion, we can now differentiate between URI and URL. A URI is a sequence of characters that identifies a web resource by location, name, or both available on the internet. Whereas, URL is a sequence of characters that only identifies the location of a resource available on the internet.


