Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
Transport Layer Security
The application layer, which makes use of TCP (or SCTP) as a connection-oriented protocol, is actually secured by the transport layer, which also offers security for that layer. These apps' messages are first enclosed in security protocol packets before being contained in TCP. Due to the nature of security, which necessitates connection formation between the two entities, apps that employ UDP cannot take advantage of these security services. The transport-layer security does not apply to electronic mail (e-mail), which is another application. We need a particular security provision for this application because it only allows one-way communication between the sender and the receiver. This is covered in the below section.
The Secure Sockets Layer (SSL) and the Transport Layer Security (TLS) protocols are currently the two most used ones for delivering security at the transport layer. Actually, the latter is a modified version of the former by the IETF. TLS is extremely similar to SSL, which is covered in this section. The location of TLS and SSL in the Internet paradigm is depicted in the image below:
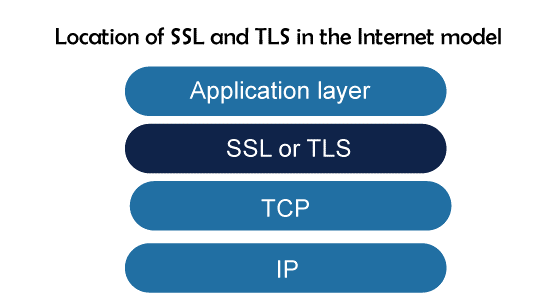
These protocols aim to guarantee data secrecy, data integrity, and server and client authentication, among other things. Applications-layer client/server programs that employ TCP services, like HTTP, can encapsulate their data in SSL packets (HTTPS). In order to allow HTTP messages to be encased in SSL (or TLS) packets, the client can use the URL https://... rather than http://... if the server and client are both capable of executing SSL (or TLS) programs. For example, banking information can be safely exchanged over the Internet for online buyers.
Socket Security Layer (SSL) Architecture
In order to secure and compress data produced at the application layer, SSL was created. Any application-layer protocol can send data via SSL in most cases; however, HTTP is the most used one. The program sends back data that has been signed, encrypted, and compressed (optional). A trustworthy transport-layer protocol, such as TCP, receives the data at this point. In 1994, SSL was created by Netscape. In 1995, versions 2 and 3 were made available. SSLv3 is discussed in this section.
Services Offered by SSL:
On data that has been received from the application layer, SSL offers a number of services:
- Fragmentation - The data is first divided into blocks by SSL that are 214 bytes or shorter.
- Compression - One of the lossless compression techniques agreed upon by the client and server is used to compress every data fragment. This service is not required.
- Message Integrity - A keyed-hash function is used by SSL to generate a MAC in order to protect the integrity of the data.
- Confidentiality - Strictly speaking, symmetric-key cryptography is used to encrypt both the original data and the MAC in order to maintain confidentiality.
- Framing - The encrypted payload receives a header. After that, a dependable transport-layer protocol receives the payload.
Key Exchange Algorithm - Each of the clients and servers must have a unique set of cryptographic secrets in order to exchange an authorized and confidential communication. One pre-master secret must first be created between the two parties in order to produce these secrets, though. This pre-master secret is established using one of the key-exchange protocols specified by SSL.
Encryption/Decryption Algorithm - A set of encryption and decryption techniques must also be agreed upon by both the client and the server.
Hash Algorithm - Hash algorithms are used by SSL to ensure message integrity (message authentication). For this reason, a number of hash algorithms have been defined.
Cipher Suite - Each SSL session has a unique cypher suite that is defined by the interaction of the key exchange, hashing, and encryption algorithms.
Compression Algorithm - In SSL, compression is not required. There is no defined compression algorithm. Consequently, a system is free to employ any compression strategy it chooses.
Cryptographic Parameter Generation - SSL requires six cryptographic secrets: two IVs (initialization vectors) and four keys, ensuring message integrity and confidentiality. For message authentication, encryption, and use as the initial block in calculations, the client needs one key for each. The server also requires it. A requirement of SSL is that the keys used in one direction and the other direction be distinct. The opposite way is unaffected by an attack coming from one direction. The process used to produce the parameters is as follows:
- Two random numbers, one generated by the client and the other by the server, are exchanged between the client and server.
- One pre-master secret is exchanged between the client and server using one of the established key exchange techniques.
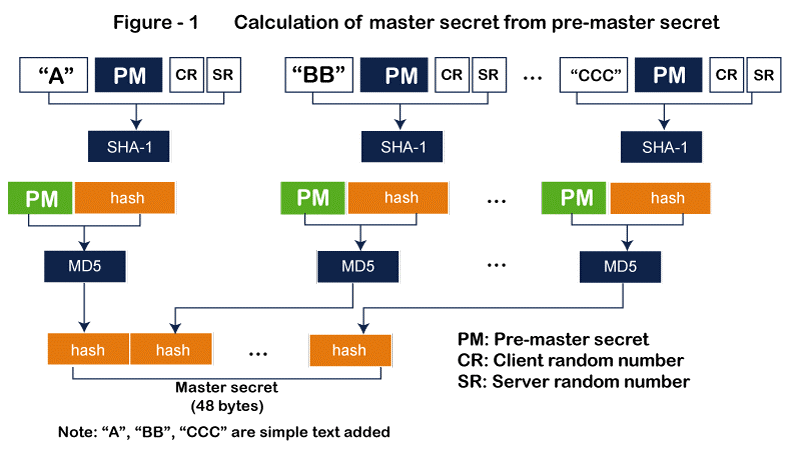
- Figure 1 illustrates how two hash algorithms (SHA-1 and MD5) are used to convert the pre-master secret into a 48-byte master secret.
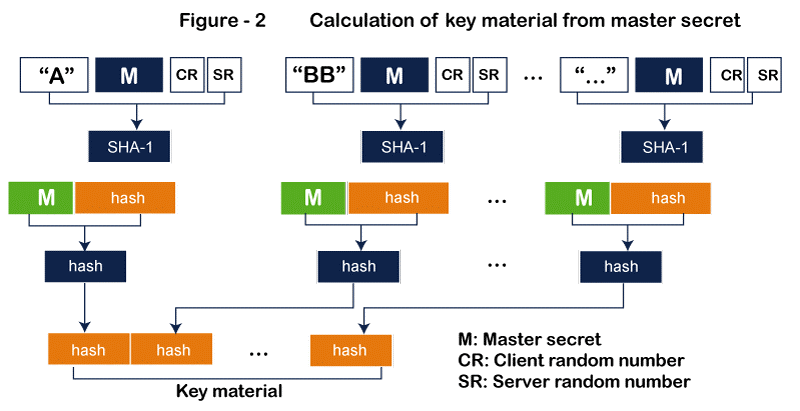
- Figure 2 illustrates how the same set of hash functions is utilized to generate variable-length key material before being prepended with various constants. Up till sufficient key material is produced, the module is repeated. Keep in mind that the cypher suite chosen and the quantity of keys required for this suite determine the length of the key material block.
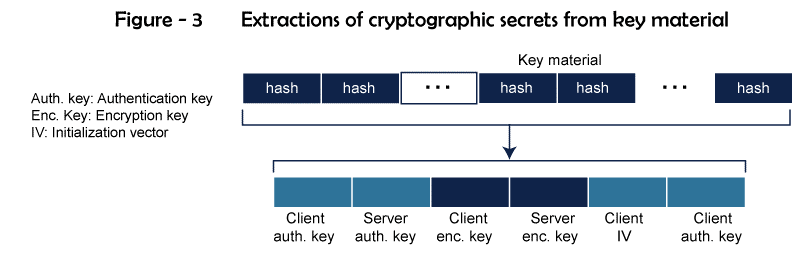
- Figure 3 illustrates how six distinct secrets were taken from the main material.
Sessions and Connections - A connection and a session are distinguished by SSL. A client and server are connected through a session. Following the establishment of a session, the two parties share data such the session identification, the certificate validating each of them (if necessary), the compression technique, the cypher suite, and a master secret that is used to generate keys for message authentication encryption.
The creation of a session is required, but not sufficient for two entities to communicate with one another and exchange data. The two parties exchange two random integers while generating the keys and parameters required for transmitting messages including authentication and privacy using the master secret.
There may be numerous connections inside a session. Within the same session, a link between two participants can be broken and then repaired. The two parties can choose to end the session when the connection is cut off, although it is not required. A session may be stopped and started again.