Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Types of Server Virtualization in Computer Network
The division of a physical server into a number of tiny virtual servers, each running a different operating system, is known as server virtualization. They are referred to as "guest operating systems." These are operating on a different OS, referred to as the host OS. In this setup, no other guests on the same host are aware of the existence of the other guests. To achieve this transparency, various virtualization techniques are used.
Types of Server virtualization :
1. The hypervisor
Between the operating system and the hardware, there is a layer known as a hypervisor or VMM (virtual machine monitor). It offers the features and services required for the efficient operation of several operating systems.
In addition to handling the queuing, dispatching, and returning of the hardware requests, it recognises traps and responds to privileged CPU instructions. The hypervisor is topped by a host operating system that controls and manages the virtual machines.
2. Virtualization in Para
The foundation is Hypervisor. This model takes care of a large portion of the emulation and trapping overhead in software implemented virtualization. Earlier than being installed into the virtual machine, the guest operating system is modified and recompiled.
Performance is improved as a result of the modified guest operating system's direct communication with the hypervisor and the elimination of emulation overhead.
Example: To support the administrative environment known as domain 0, which is used by Xen primarily, a tailored Linux environment is used.
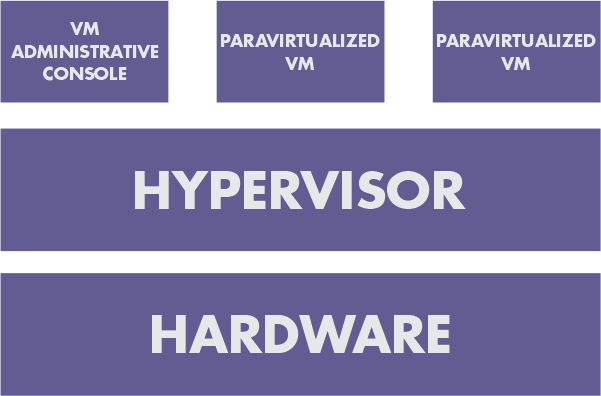
Advantages:
- Simpler, Better Performance
- Emulation is not necessary
Limitations:
- calls for changing a guest operating system
3. Complete virtualization
It and paravirtualization are very similar. When necessary, it can simulate the underlying hardware. The operating system's machine operations for I/O and changing the status of the system are captured by the hypervisor. After trapping, these operations are software-emulated, and the status codes that are returned are remarkably similar to what real hardware would produce. Because of this, an unaltered operating system can function on top of the hypervisor.
This approach is used, for instance, by VMWare ESX server. As the administrative operating system, Service Console is a modified version of Linux. Compared to Paravirtualization, it is slower.
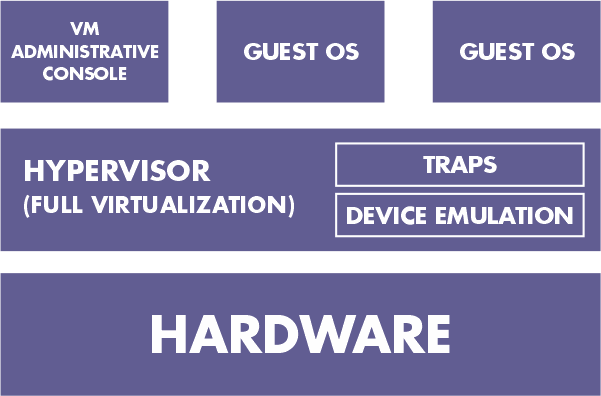
Advantages:
- The Guest operating system doesn't need to be changed.
Limitations:
- Emulation makes complex slower
- The new device driver installation is challenging.
4. Virtualization with Hardware Assist
In terms of functionality, it is comparable to Full Virtualization and Paravirtualization, with the exception that it needs hardware support. By relying on the hardware extensions of the x86 architecture, a large portion of the hypervisor overhead caused by trapping and simulating I/O operations and status instructions executed within a guest OS is dealt with.
Unmodified OS can be used to handle hardware access requests, privileged and protected operations, and communication with the virtual machine as the hardware support for virtualization would be used.
Examples of hardware that supports virtualization include AMD's V Pacifica and Intel's VT Vanderpool.
Advantages:
- A guest operating system doesn't need to be changed.
- very low overhead for hypervisor
Limitations:
- Hardware support is necessary
5. Virtualization at the kernel level
It runs a different Linux kernel and sees the associated virtual machine as a user-space process on the physical host rather than using a hypervisor. As a result, managing multiple virtual machines on a single host is simple. For communication between the virtual machine and the main Linux kernel, a device driver is utilised.
Virtualization requires processor support (Intel VT or AMD - v). The display and execution containers for the virtual machines are modified versions of the QEMU process. Kernel-level virtualization resembles server virtualization in many ways.
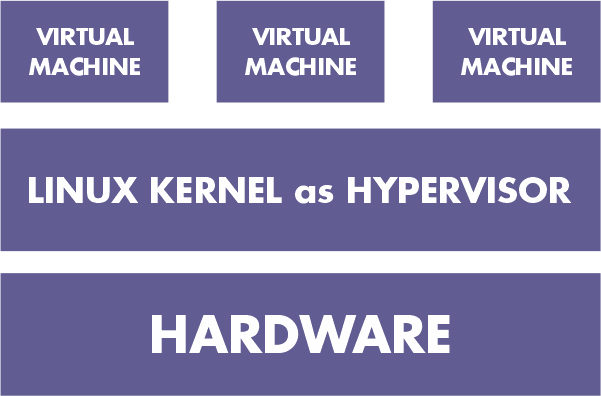
Examples include Kernel Virtual Machine and User-Mode Linux (UML) ( KVM )
Advantages:
- There is no need for specialised administrative software.
- hardly any overhead
Limitations:
- Hardware Support Is Necessary
6. System-level or operating system virtualization
utilises a single instance of the operating system kernel to run multiple, logically separate environments. Also known as the "shared kernel approach" because the host operating system kernel is shared by all virtual machines. based on the "chroot" change root concept.
During boot, chroot begins. Root filesystems are used by the kernel to load drivers and carry out other early system initialization tasks. The system continues system initialization and configuration within that file system after switching to a different root filesystem using the chroot command to mount an on-disk file system as its final root filesystem.
This idea is expanded upon by the chroot mechanism of system-level virtualization. By doing so, the system is able to launch virtual servers with independent sets of processes that run in relation to their own filesystem root directories.
The ability to run different operating systems on different virtual systems is the primary distinction between system-level and server virtualization. Server virtualization is when different servers can have different operating systems, including different versions of the same operating system, as opposed to system-level virtualization, which requires all virtual servers to share the same copy of the operating system.
Examples include FreeVPS, Linux Vserver, and OpenVZ.
Advantages:
- a great deal lighter than full machines (including a kernel)
- can accommodate a lot more virtual servers
- Enhanced Safety and seclusion
- An operating system virtualization typically involves little to no overhead.
- OS Virtualization enables live migration.
- Additionally, it can make use of dynamic load balancing of containers between nodes and clusters.
- The file-level copy-on-write (CoW) technique is possible with OS virtualization, and it is more space-efficient, easier to cache, and easier to back up data than block-level copy-on-write schemes.
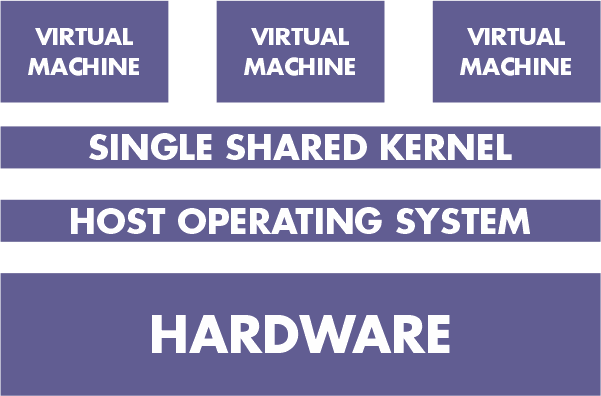
Limitations:
- All virtual servers could be brought to a halt by kernel or driver issues.


