Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Mesh Topology Advantages and Disadvantages
To understand the advantages and disadvantages, first we have to know what is Mesh Topology? So, let's begin with introduction.
What is Mesh Topology?
It is a type of network setup in which all the devices and computers are interconnected. We have been able to achieve a full or partial connection with the help of mesh topology.
We needed to find out the structure of mesh topology. For some reason, we can connect most of the transmission as the distributed system if one connection fails. This topology is an example of how the wireless network works currently.
When a connection is completed, and all the computers are connected, we can calculate the number of connections with a specific type of formula. But when a parcel connection exists, we have to connect at least two computers to multiple devices. It is an excellent way to implement primary connections without thinking about any computer failing to operate and disrupting the connection.
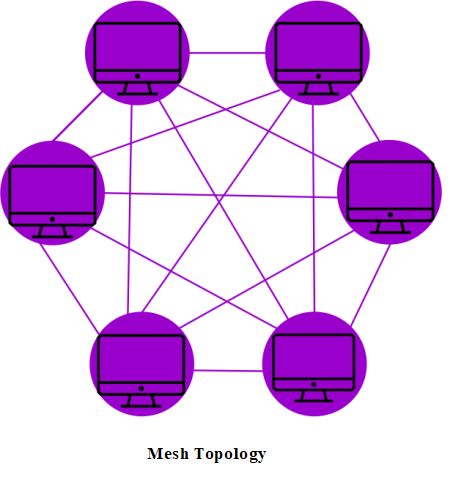
There are two types of Mesh topologies which are mentioned below:
- Fully-connected Mesh Topology
- Partially-connected Mesh Topology
1. Full Mesh Topology:
All the nodes within the network are connected with every other. If there are n number of nodes are connected during a network transmission, each node will have an n-1 number of connections.
2. Partial Mesh Topology:
The partial mesh is more practical as compared to the full mesh. In a partially connected mesh, all the nodes aren't necessary to be connected with one another during a network.
Some of the advantages and disadvantages of mesh topology connection are given below:
Advantages of mesh topology:
There are some advantages or benefits of mesh topology which are described below:
1. High-level traffic management of mesh topology:
There is no hierarchical relationship exists between mesh topology. For instance, let us consider a device that is connected to it and attempts to contact any other one by directly taking advantage of the routing ability of the device. In this case, it will be able to do it.
2. Failure of one single device does not affect the network:
When the mesh topology is resistant to problems, it is exceptional. All the notes after the network translate and receive the information within it. With sufficient redundancy, the structure provides its users that they can keep it in running condition even if some malfunction occurs. If one of the nodes malfunctions, then the network has the strength to use other nodes and complete the mesh.
3. Data transmission consistency:
In a mesh topology, there are multiple paths available for data transmission. Creating a successful set of ways to operate this topology requires each node to be connected to all the other ones for completion. as a result, the overall data transmission is more consistent. Moreover, multiple node failures do not affect the pathway and can still send a message.
4. New devices addition does not affect the data transmission:
Mesh topology structure gives permission to the users to add new widgets for the connection of new devices without disrupting the messages. These are the messages which occur at that time. Since every node is connected, a breakdown in one of the equipment would not disrupt the information flow.
5. Simple scalability:
Since each node works like an individual router, in Mesh topology, it does not require an additional router that allows one to change the size of the network comfortably. Hence, temporarily one user can easily add a new connection to any room in a corporate at the current speed-up operation.
6. Easy to add mesh topology:
Topology addition within the mesh is easy and goes about without any problem. One user needs to connect the nodes to the gateways to pass the messages to the remaining network for it to work. It allows the technology to become self-optimized.
7. Takedown of the network is nearly impossible:
Unless there is a global disaster, in the modern structure of mesh topology in the world, it is almost impossible to take it down where all the devices we use around the globe get wiped out.
8. No need for centralized authority:
There is no need of is centralized control within the mist apology to incorporate for sending the data. Hence, if desired, one setup an individual-based secure method of communication that lets them have the option to be anonymous. They don't need to run a firewall or other software solutions to maintain their privacy.
9. Flexible:
Due to the partial shortfall option of mesh topology, it has an immense flexibility option in it. Therefore, for each node in this topology, one user is not forced to complete a set of connections, but the network can be built with a partial wave to take advantage of the enhanced communication.
10. Management of massive volume of data:
A tremendous volume of data can be handled with mesh topology, which is compared to traditional systems since it is possible to connect multiple devices simultaneously to transmit data simultaneously.
Disadvantages of mesh topology:
For better understand the mesh topology, we should know the disadvantages or limitations of it:
1. High cost:
The implementing cost in this topology is very high compared to others. This is due to the requirement of various parts of very extensive equipment. To operate correctly, we need to have all the hardware, Internet bandwidth, cabling, etc., connected properly.
2. Time-consuming to build and maintain:
When it gets operational, then the addition of a new node is very simple, but the initial process is very complex and time-consuming.
3. High risk of redundant connection:
Due to a large number of networks can be handled by miss topology, it is a chance of setting redundant connections.
4. Increased workload in each node:
Every node has more than one responsibility, and each one must act as a router. Hence the system is very complex.
5. Latency issues:
What a handling data transfer in a timely manner, low power mesh topology does not have the processing capacity for it. Hence there are plenty of latency issues.
Comparison between advantages and disadvantages of Mesh Topology:
| Advantages | Disadvantages |
|---|---|
| 1. The addition of a new device is very easy. | 1. Initial setup is very difficult. |
| 2. High level of traffic is manageable by it after the completion of the setup. | 2. Implementing post for mesh topology comparatively higher |
| 4. Scalability is simple. | 3. Compared to other, it is very costly |
| 5. Addition of new devices does not affect the network. | 4. There is high risk of redundant connection |
| 5. Data transmission is consistent. | 5. The additional cost is required for each node |
| 6. A malfunction in one device does not disturb the connection. | 6. In these, latency issues are very common |
| 7. There is no need for a central hierarchy. | 7. It has complex structure. |
| 8. Without a complete set of web, it can operate simply | 8. Power consumption of Mesh Topolgy is more than the other topologies. |


