Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Fundamentals of Computer Networking
|
This tutorial will discover the definition of computer networking, its types, computer networks work, networking concepts, commonly used terms, networking and internet, how it works, and network topologies. What is a Computer Network?"A Computer Network is defined as a set of two or more computers that are linked together?either via wired cables or wireless networks i.e., WiFi?with the purpose of communicating, exchanging, sharing or distributing data, files and resources." 
Computer Networks are built using a collection of hardware (such as routers, switches, hubs, and so forth) and networking software (such as operating systems, firewalls, or corporate applications). Though one can also define the computer networks based on their geographic location, a LAN (local area network) connects computers in a definite physical dimension, such as home or within an office. In contrast, a MAN (Metropolitan area network) connects computers ranging between multiple buildings in a city. The Internet is the most significant example of WAN (Wide Area Network), connecting billions of networking devices across the world. One can also describe the concept of computer networking by its communicating protocols, the physical arrangement of its networking elements, how it manages network traffic, and it's functioning. Computer networks are globally used by businesses, the entertainment industry, education in the research field for communication and transferring their data from source to destination node. All the other technologies, including the internet, Google search, instant messaging apps, online video streaming, social media, email, cloud kitchen, cloud data storage, etc., all exist because of computer networks. Computer Network TypesBelow are the most common computer network types that are frequently used these days:
1. LAN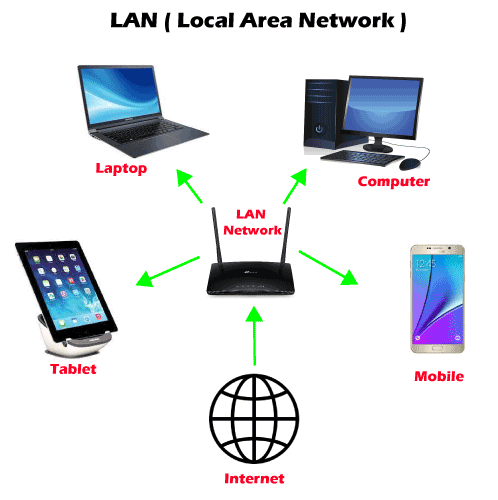
LAN or Local Area Network is a group of devices connecting the computers and other devices such as switches, servers, printers, etc., over a short distance such as office, home. The commonly used LAN is Ethernet LAN. This network is used as it allows the user to transfer or share data, files, and resources. 2. WLAN
WLAN or Wireless local area network is similar to LAN with the difference that it uses wireless communication between devices instead of wired connections. WLAN typically involves a Wi-Fi router or wireless access point for devices, unlike smartphones, laptops, desktops, etc. 3. CAN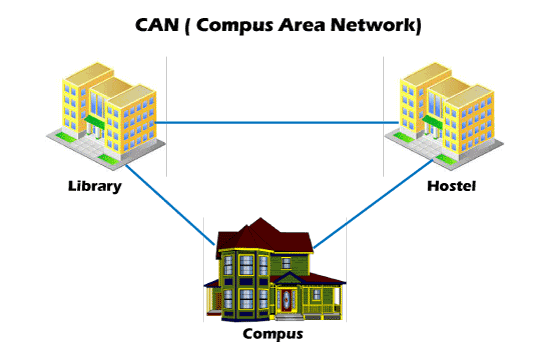
CAN or Campus Area Network is a closed corporate communication network. A CAN is a mobile network that may contain a private or public part. CANs are widely used colleges, academies, and corporate sites. 4. MAN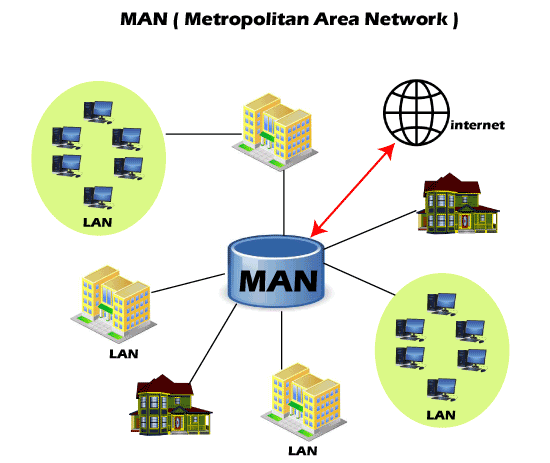
MAN or Metropolitan Area Network is typically a more extensive network when compared to LANs but is smaller than WANs. This network ranges between several buildings in the same city. Man networks are connected via fiber optic cable (usually high-speed connection). Cities and government bodies usually manage MANs. 5. PAN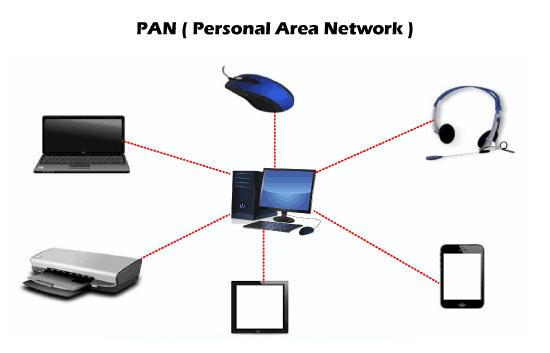
PAN or Personal Area Network is a type of network used personally and usually serves one person. This network usually connects devices unlike your smartphones, laptop, or desktop to sync content and share small files, unlike songs, photos, videos, calendars, etc. These devices connect via wireless networks such as Wi-Fi, Bluetooth, Infrared, etc. 6. SAN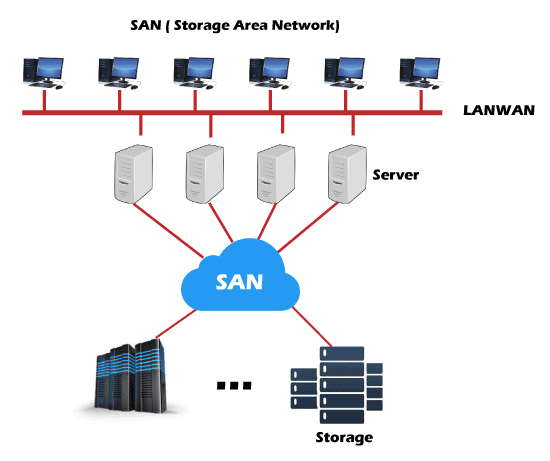
SAN or Storage Area Network is a specialized high-speed network that stores and provides access to block-level storage. It is a dedicated shared network that is used for cloud data storage that appears and works like a storage drive. SAN consists of various switches, servers, and disks array. One of the advantages of SAN is that it is fault-tolerant, which means if any switch or server goes down, the data can still be accessed. 7. VPN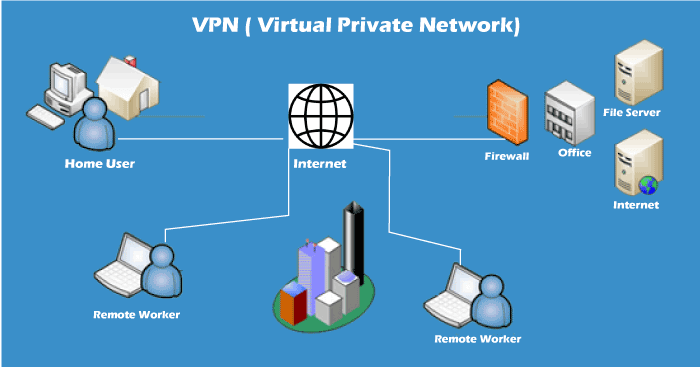
VPN or Virtual Private Network is a secure tool that encrypts point-to-point Internet connection and hides the user's IP address and virtual location. It determines an encrypted network to boost user's online privacy so as their identity and data are inaccessible to hackers. 8. WAN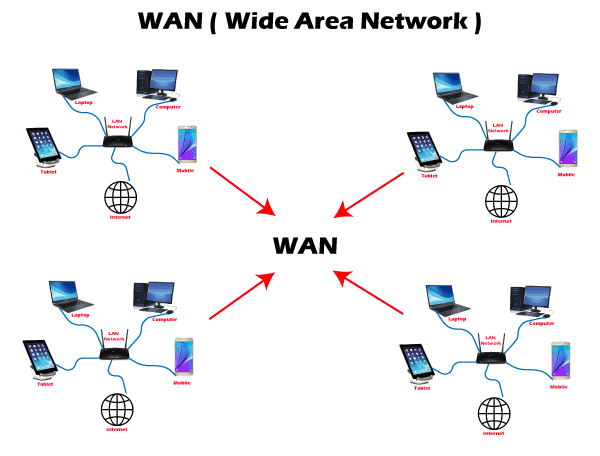
WAN or Wide Area Network is the most significant network type connecting computers over a wide geographical area, such as a country, continent. WAN includes several LANs, MANs, and CANs. An example of WAN is the Internet, which connects billions of computers globally. Networking terms and conceptsSome of the most commonly used terms in day-to-day networking life are as discussed below: 1. IP addressAn IP address or Internet Protocol is a unique number that represents the address where you live on the Internet. Every device that is connected to the network has a string of numbers or IP addresses unlike house addresses. You won't find two devices connected to a network with an identical IP address. When your computer sends data to another different, the sent data contains a 'header' that further contains the devices' IP address, i.e., the source computer and the destination device. 2. NodesA node refers to a networking connection point where a connection occurs inside a network that further helps in receiving, transmitting, creating, or storing files or data. Multiple devices could be connected to the Internet or network using wired or wireless nodes. To form a network connection, one requires two or more nodes where each node carries its unique identification to obtain access, such as an IP address. Some examples of nodes are computers, printers, modems, switches, etc. 3. RoutersA router is a physical networking device, which forwards data packets between networks. Routers do the data analysis, perform the traffic directing functions on the network, and define the top route for the data packets to reach their destination node. A data packet may have to surpass multiple routers present within the network until it reaches its destination. 4. SwitchesIn a computer network, a switch is a device that connects other devices and helps in node-to-node communication by deciding the best way of transmitting data within a network (usually if there are multiple routes in a more extensive network). Though a router also transmits information, it forwards the information only between networks, whereas a switches forwards data between nodes present in a single network. Switching is further classified into three types, which are as follows:
5. PortsA port allows the user to access multiple applications by identifying a connection between network devices. Each port is allocated a set of string numbers. If you relate the IP address to a hotel's address, you can refer to ports as the hotel room number. Network devices use port numbers to decide which application, service, or method is used to forward the detailed information or the data. 6. Network cable typesNetwork cables are used as a connection medium between different computers and other network devices. Typical examples of network cable types are Ethernet cables, coaxial, and fiber optic. Though the selection of cable type usually depends on the size of the network, the organization of network components, and the distance between the network devices. Computer Networks and the InternetThe Internet is the major example of a WAN, which connects billions of computers globally. Internet follows standard protocols that facilitate communication between these network devices. Those protocols include:
ISPs (Internet Service Providers) NSPs (Network Service Providers) effectively support the internet infrastructure. The infrastructure allows the transportation of data packets to the recipient device over the Internet. Internet is a giant hub of information, but this information is not sent to every computer connected to the Internet. The protocols and infrastructure are responsible for managing to share the precise information the user has requested. How do they work?
Network Topology"Network topology is defined as the arrangement of computers or nodes of a computer network to establish communication among all." A node refers to a device that can transmit, receive, create, or store information. The nodes are connected via a network link that could be either wired (cables, Ethernet) or wireless (Bluetooth, Wi-Fi). To help build a successful network in different situations, topologies are further classified into several types. 1. Bus Topology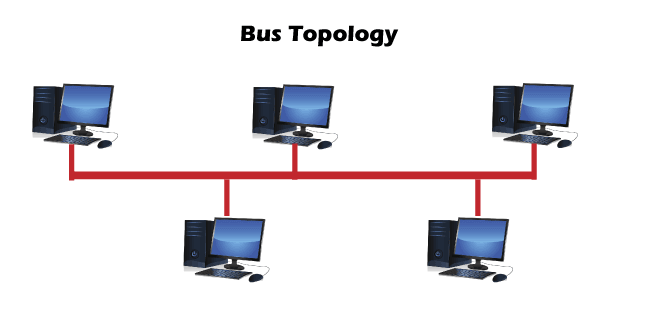
2. Ring Topology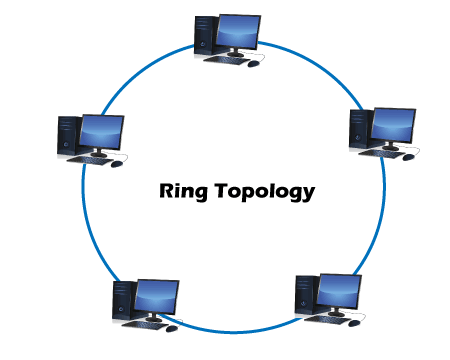
3. Star Topology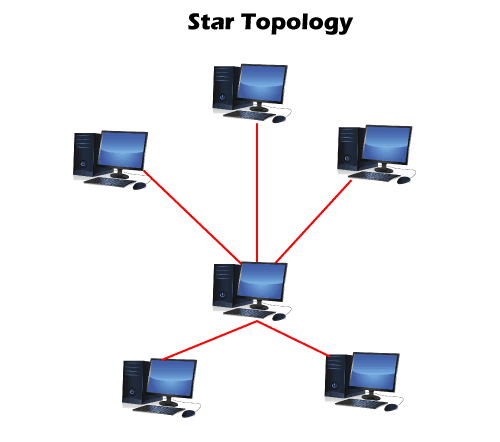
4. Mesh Topology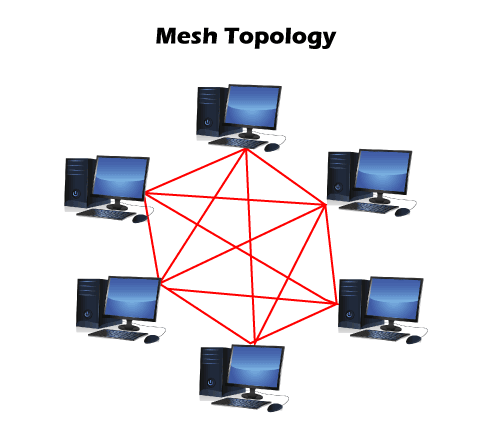
|


