Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Virtual Circuits vs Datagram Networks
Virtual Circuits are computer networks that offer connection-oriented services, whereas Datagram networks offer connection-less services. The Internet that we use is actually built on a Datagram network (connection-less) at the network level since not all packets that travel from a source to a destination use the same route.
Virtual Circuits
Connection-oriented switching is another name for virtual circuits. Before messages are sent, a virtual circuit switching sets a predetermined routing. This route is referred to as a virtual circuit since it gives the user the impression that a passionate physical circuit exists. The call request and call accept packets are used to establish the connection between the sender and the recipient.
The term "virtual circuit" refers to a logical link between two network nodes, typically in a communications network. The path consists of many network parts that are connected by switches.
To better comprehend the virtual circuits, let's look at the diagram shown below:
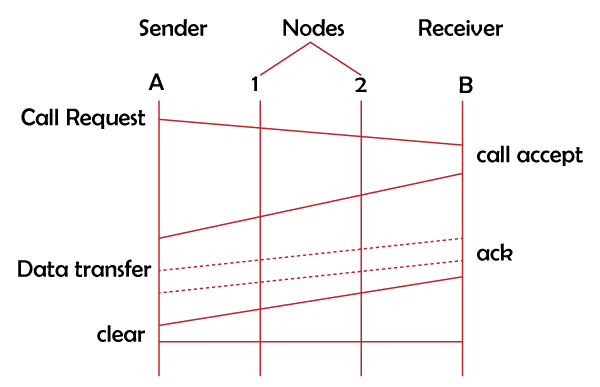
The transmitter and receiver in the aforementioned diagram are A and B. The sender and receiver are linked together using the call request and call accept packets. Once a path has been established, data will be transferred.
The receiver transmits an acknowledgementsignal after receiving the data to confirm receipt of the message. If a user wants to break the connection, a clear signal is sent.
Datagram Networks
It is a method of switching packets in which every packet, or "datagram," is seen as a distinct entity. The switch uses the destination information contained in each packet to direct it to the intended location. Since no specific channel is classified for a connection session, there is no need to reserve resources. As a result, packets have a header with all of the information about the destination. A packet's header is examined by the intermediate nodes, which then select an appropriate link to another node that is closer to the destination.
Datagram networks assign resources according to the First-Come-First-Serve (FCFS) principle. Regardless of its source or destination, if another packet is being processed when a packet arrives at a router, it must wait.
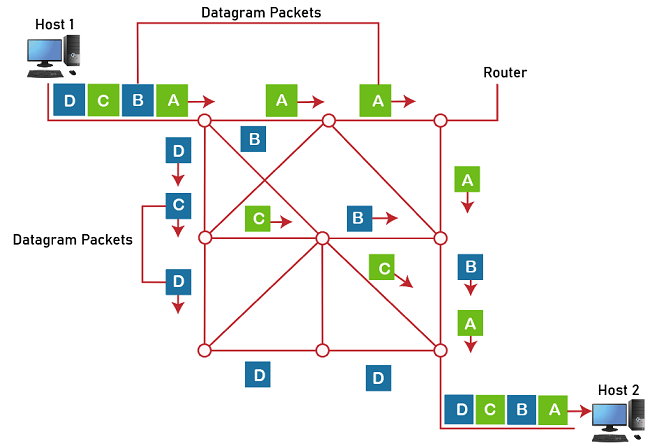
Datagram packets transmitted between hosts H1 and H2 are shown in the diagram above. The same message is being carried by the four datagram packets bearing the labels A, B, C, and D, each of which is being sent by a separate path. The packets of the message reach their destination out of order. It is H2's responsibility to rearrange the packets in order to recover the original message.
Difference between Virtual Circuits and Datagram Networks
Let's look at the key distinctions between these two highly contested topics now:
| S. no. | Comparison Criteria | Virtual Circuits | Datagram Networks |
|---|---|---|---|
| 1. | Definition | It is connection-oriented, which means that resources like buffers, CPU, bandwidth, etc., are reserved for the period of time that a data transfer session will use the newly established VC. | The service isconnection-less. Since there isn't a path specifically designated for a connection session, no resource reservations are required. |
| 2. | Path | Each server along the path has resources reserved when the first packet is sent. For the duration of the connection, subsequent packets will take the same route as the first one transmitted. | Every packet is permitted to follow any accessible path. Because routing tables on routers change continuously, intermediary routers must constantly calculate routes. |
| 3. | Header | A global header is needed because every packet will take the same route. The remaining packets often do not need global headers; just the first packet of the connection does. | All packets must be linked to a header that has the correct information about the source and the upper layer data since every packet has the freedom to select any path. |
| 4. | Data Flow | All packets follow a precise path, so when they arrive at their destination, they are all received in sequence. | The connection-less attribute allows data packets to arrive at their destination in any sequence, which raises the possibility that they will not be received in the correct order at the receiver's end. |
| 5. | Resource Requirements & Utilization | By using virtual circuit switching, all packets are guaranteed to reach their destination. No packet will be discarded because there are no resources available. | That a packet can only be transmitted if resources like the buffer, CPU, and bandwidth are available is a key disadvantage of datagram packet switching. If not, the packet will be thrown away. |
| 6. | Phases | Setup, data transfer, and teardown are the threephases of the transmission process. | Any type of communication phase does not exist in Datagram Networks. |
| 7. | Addressing | The routing and addressing are chosen during setup. The VC number is the only thing each packet contains as a result. | Each datagram packet contains a complete list of the source and destination addresses. |
| 8. | Reliability | The aforementioned information leads to the conclusion that Virtual Circuits are a very dependable means of data transport. | Datagram networks are less reliable than virtual circuits. |
| 9. | Implementation and Cost | Virtual circuits have the drawback that every time a new connection is established, resources and additional data must be allocated at every router along the line. This can be a problem if numerous customers are attempting to reserve a router's resources at the same time. | However, implementing datagram networks is usually simple and inexpensive because there isn't the added hassle of building a dedicated channelevery time an application needs to interact. |
| 10. | Applications | Specifically for phone conversations, it is utilized by the ATM (Asynchronous Transfer Mode) Network. | It is commonly employed by the IP network, which is utilized for data services such as the Internet. |
Conclusion
- Connection-oriented switching is another name for virtual circuits. Prior to message transmission, virtual circuit switching creates a predetermined path.
- Since it seems to the user to be a devoted physical circuit, the path in virtual circuits is referred to as a virtual circuit.
- Each packet, referred to as a datagram, is considered as an independent entity in datagram networks(known as a packet-switching technology). Each packet contains destination information, which the switch makes use of to direct the packet to the desired location.
- Because there is no designated channel for a connection session in Datagram Networks, no resource reservations are required. The effect is that packets have a header with all of the destination's data.
- First-come, first-serve (FCFS) scheduling governs resource distribution in datagram networks.
- A virtual circuit is easier to understand than a network of datagrams.
- Datagram-based networks require substantially less setup and upkeep.


