Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
What is Autonomous System
An autonomous system (AS) consists of several connected Internet Protocol routing prefixes. One or more network operators manage all these routing prefixes in place of a single administrative entity or organization. These IP prefixes have a clearly defined routing policy that states how the autonomous system will exchange the routing data with other nodes and similar systems. Each autonomous system is provided with a unique autonomous system number (ASN) to implement in the Border Gateway Protocol (BGP) routing.
Their regional internet registries provide the ASN to the Local Internet Registries (LIRs) and end-user organizations. It will receive blocks of autonomous system numbers from the reassignment from the Internet Assigned Number authority. The IANA is also responsible for maintaining a registry of the ASNs. This registry is only used for private use, and therefore they cannot be revealed on the internet.
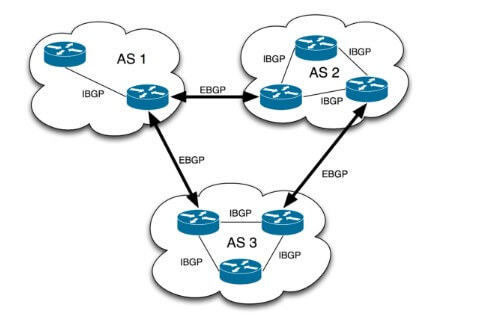
In simpler language, the as can be represented as a group of interconnected IP networks managed by only one organization, such as a college, university, or government. This entity performs control and management of these interconnected networks.
Autonomous System Routing Policy
An autonomous system is a collection of several IP routing prefixes linked to each other. Each autonomous system has its routing policy. The routing policy comprises the list of IP address space the system manages. It also compromises a list of other autonomous systems to which the system is directly linked. This information is shared on the internet by implementing the Border Gateway Protocol (BGP).
IP Address Space
An IP Address space refers to a specific group or range of IP addresses. Each autonomous system manages a certain number of IP address spaces. The collection of IP addresses can also be referred to as an IP address block.
Consider that all the mobile numbers worldwide were ordered sequentially, and each mobile service provider is given a range of mobile numbers. Let's consider a company Mobile Co. A that manages mobile numbers between 00-00000 to 49-99999, and another company manages the numbers from 50-00000 to 99-99999. Suppose Person A makes a call to Person B on his mobile number, which is 44-47859, then the call will be routed to Person A via Mobile Co. A, but if the call is made to a different number, such as 88-37939, then it will be routed via Mobile Co. B.
This is similar to the working of the IP address space. Consider a company AS Co. That runs an autonomous system and manages a range of IP addresses. The IP address 192.0.0.211 lies within the range managed by the AS Co. Thus, if any node in the network transmits a data packet to 192.0.0.211 then the data packet will be transmitted to the autonomous system managed by AS Co. If the node transmits to an IP address that is not included in this range then the data packet will be transmitted to a different autonomous system. It may pass through the system of AS Co. as an intermediary node.
IP Address Prefixes
When the network engineers want to determine which IP Address is managed by which autonomous system, they determine it by discussing the IP address prefixes managed by each autonomous system. IP address prefix constitutes a range of IP addresses. The IP address prefixes are represented differently than the IP address. The IP address prefixes are represented as follows: 192.0.1.1/15. This means that the range of the IP address maintained by the AS is 192.0.1.1.0 to 192.0.1.1.225 and not from 192.0.1.1.0- 192.0.1.1.15.
How is an AS different from Other Network Groups?
The difference between an AS and other network groups is that the AS is represented as a single entity to any other external autonomous system. It means that each AS has only one coherent routing plan. The routing plan should be independent of how the communication is performed within the autonomous system.
An autonomous system consists of several routers handled by only one administrative body. The AS is presented with a unified interior routing plan to any other external autonomous system in the network. It provides a consistent image of the networks present in the AS.
These systems are built around IP prefixes that can be implemented in class A, B, or C networks. When the networks are implemented with an autonomous system, the term prefix is equivalent to the CIDR block. CIDR stands for Classless Inter-Domain Routing, a group of IP addresses with the same IP prefix and constitutes the same number of bits. Therefore, autonomous systems are also referred to as the routing domain.
An autonomous system can be divided into three categories. These categories are as follows:
- Multihomed Autonomous System:An autonomous system with two or more external autonomous systems.
- Transit Autonomous System:It acts as a connection between the autonomous system. It links the AS with the external AS.
- Single Homed System:This autonomous system connects the AS with a single external AS.
The Tier 1 ISPs, or the ISPs with big networks, manage the largest autonomous system. Each tier 1 ISP has its autonomous system. These ISPs create the backbone of the internet. They are responsible for managing the traffic flow in the network. They own and maintain the network infrastructure. The autonomous system of the ISPs is interconnected, allowing the transmission of worldwide packet exchanges through the network.
All connections between the tier 1 autonomous systems are non-commercial. This allows the nodes to transmit the data between different tier-1 systems freely.
ISPs also help fund internet exchange points -- physical locations that facilitate packet exchange between ISPs and other entities. Tier 2 ISPs typically contract with Tier 1 ISPs to access the internet backbone, and Tier 3 ISP's contract with Tier 2 ISPs, which, in turn, contract with Tier 1 ISPs.
Autonomous System Number (ASN)
The unique number assigned to every autonomous system in the network is called the autonomous system number. It is used as an identifier for the system in the network. It is used when the autonomous system exchanges the routing data with the other system.
An ASN supports both 16-bit and 32-bit formats. The 32-bit format was recently provided; all the ASNs provided till 2007 were in the 16-bit format. They can either be publicly visible to other nodes or private if the ASN wishes to exchange the routing information with the other autonomous system on the network. Then the AS must have an autonomous public system number. It enables other ASes to identify the other AS.if an autonomous system has a public ASN, all the routing paths that begin from the autonomous system are visible on the internet.
If the autonomous system has a private ASN, it can facilitate communication with only one network provider. AS with private ASN needs a Border Gateway Protocol to communicate using the network. In this scenario, the routing paths originate from the AS, and the routing policy is unavailable on the internet.
The internet-assigned numbers authority controls the autonomous system number system. It is also responsible for distributing the ASNs in the five global regions. It coordinates with all the regions to efficiently assign the ASNs.
Each region has its regional internet registry that records the Autonomous system numbers assigned to the different AS in the particular region. The five regions and the area maintained by each region is as follows:
- African Network Information Center: It manages the ASNs distributed all over the African continent.
- Asia-Pacific Network Information Centre: It manages the ASNs assigned in the Asian and Pacific region.
- American Registry for Internet Numbers manages the ASNs distributed in Canada and the United States. It includes some Caribbean Islands as well.
- Latin America and Caribbean Network Information Centre: It manages the ASNs assigned to the autonomous network in Latin America and some Caribbean islands.
- Réseaux IP Européens Network Coordination Centre: It manages the ASNs in Europe, the Middle East, and Central Asia.
The public Technical Identifiers organization performs several functions of the IANA. These organizations are affiliated with the Internet Corporation Names and Numbers that manage the functions of IANA.
Border Gateway Protocol
There are several networks present in an autonomous system. The transmission of data within the network is performed using the routing data to each other using one or more interior gateway protocols. In contrast, communication between the AS depends upon a single exterior gateway protocol: Border Gateway Protocol. The protocol allows the AS to transmit the routing information and efficiently transmits the data packets among different AS. The BGP plays a crucial role in transmitting data over the internet. Therefore, it is also called the protocol that runs the internet.
BGP is a routing protocol implemented between AS; it exchanges network reachability data between the different BGP nodes. The BGP uses this information to transmit the data packets via the most efficient routes to the receiver's autonomous node.
For performing the above function border gateway protocol implements Transmission Control Protocol (TCP) as its transport protocol. It makes Border Gateway Protocol compatible with the entire internet network. The protocol does not need to perform explicit sequencing or retransmission functions. When the two nodes establish a TCP connection by performing the three-way handshake, they send data to ensure they meet the connection requirement. It is done by checking the requisitive parameters of both nodes.
The autonomous system implements BGP to tell the other autonomous systems that it is ready to establish a connection and for which IP address the AS manages is responsible. The routers that are used in the BGP communicate with each other throughout the connection. They update the routers and share the current routing information. The routing paths are updated continuously in the network. Each router that implements BGP also maintains a routing table that stores all the paths connecting different nodes in the network.
BGP then utilizes this information and the autonomous system numbers forwarding the network topology that transmits the data packets via the most optimal routes. It prevents the sending of the data into network loops. The protocol depends upon a destination-based forward mechanism. In this mechanism, the data packet is transferred based on the destination address attached by the IP in the header. The routing policies must comply with this mechanism to deliver the packet to the destination node.
Is BGP Routing Necessary?
It is the function of the internet protocol to route the transmitting data packet in the network. Internet protocol inserts an IP header in the data packets that store information such as the destination node address that determines the packet's final destination. BGP is used to direct the data packets to the most efficient path to this node. If the BGP protocol is not implemented, the data packet will reach the packets, which may take a long time. The IP packet would travel form different ASes on the internet to search the AS with the destination node. There will be no defined path for the data packet in the network.
Connection Between the Autonomous System
Autonomous Systems are linked with each other they transmit network traffic (data packets) to other AS. The process of transmitting packets from one AS to another is termed peering. One method the ASes use to connect directly with other AS is linking at physical locations known as Internet Exchange Points (IXPs). An IXP is a large local network with numerous routers, switches, and cable connections.


