Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
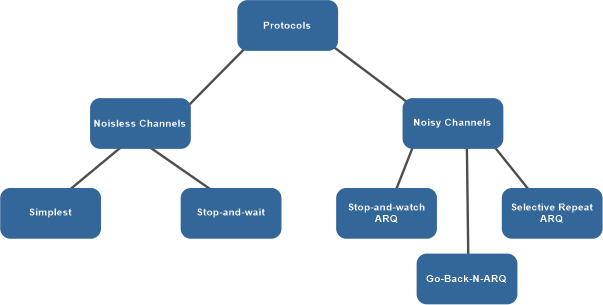
Protocols in Noiseless and Noisy Channel
The study of protocols is divided into two categories: those that can be applied to channels with no noise or errors and those that can be applied to channels with noise or errors. Although the first group of protocols cannot be applied in real-world situations, they provide a foundation for protocols for noisy channels.
What is meant by a protocol?
A protocol refers to a defined set of guidelines and regulations that control the communication between different devices in a network. These guidelines specify the way in which data is formatted, timed, sequenced, and checked for errors during transmission.
Protocols play a crucial role in ensuring accurate, efficient, and clear communication between devices. They make it possible for devices of different types and brands to communicate with each other, and they provide a consistent method for transmitting data across a network.
Headers are responsible for selecting protocols, which are rules governing communication between devices in a network. These headers contain information describing the message's nature and the handling it will receive. To detect any issues, the headers must include information such as the message's checksum, destination, and source addresses, and other necessary header addresses.
The noiseless channel has the following two protocols:
1. SIMPLEST Protocol - A simple protocol for a noiseless channel would be one that involves the direct transfer of data from the source to the destination without any intermediate processing. In this scenario, the channel is assumed to be noise-free, which means that the data transmitted remains intact and does not get corrupted. In a noiseless channel, a simple protocol could consist of a straightforward method for transmitting data, such as sending one bit at a time, with no error correction or flow control mechanisms in place. This type of protocol is ideal for a noiseless channel as the lack of noise ensures that the data transmitted is received accurately, making the implementation of additional measures unnecessary.
The simplest protocol does not have any mechanisms for controlling the flow of data or detecting and correcting errors, as it is only used in noise-free channels. The protocol assumes that the receiver is always ready to process any data frames sent by the sender immediately. This type of protocol, which only allows data to flow from the sender to the receiver, is known as a one-way protocol. Since this protocol is unidirectional, there is no need for an acknowledgment or confirmation of receipt. Furthermore, because there is no data loss during transmission, there is no need to resend or retransmit the data.
In order to create the simplest protocol, the following presumptions have been made:
- There is no noise whatsoever in the broadcast channel (a channel with no duplications, lost frames, or corrupted frames).
- The assumption is that the transmission route is perfect, with no instances of data loss, duplication, or corruption.
- There is no system for controlling errors and flow.
- The sender's and receiver's end have an endless amount of buffer space for the frames.
Points to Remember:
- The processing time for this technique is quite brief. So, it may be disregarded.
- Each party is constantly prepared to send and receive data.
- Without giving the recipient any thought, the sender delivers a series of data frames.
- No data loss occurs, hence neither an ACK nor a NACK is sent.
- The data is transferred to the following layer right away by the DLL at the receiving end after the frame header has been deleted.
In the absence of an ACK or NACK, the sender must wait a pre-determined time before transmitting the message. To solve this issue, a different protocol known as the Sliding Window Protocol is used. The sliding window protocol is a data connection layer protocol that allows for the sequential and reliable transmission of data frames. This protocol allows the sender to transmit multiple frames at once by utilizing sequence numbers. The sequence numbers are assigned to each data frame by the sender to ensure proper ordering in the event that a frame needs to be retransmitted. This also enables the receiver to detect lost or damaged packets.
Note - An ACK (acknowledgment) is sent to the sender by the receiver after it has received the frame. The ACK informs the sender whether the recipient successfully received a specific frame. Go-Back-N ARQ and Selective Repeat ARQ are the two different kinds of sliding window techniques.
Flow Diagram in Simplest Protocol:
A data flow diagram (DFD) is a graphical representation of the flow of data in a system. In the context of the simplest protocol, a DFD can illustrate the movement of data between the sender and the receiver. The DFD would show how the sender sends the data frames to the receiver, how the receiver processes the data, and what happens if any errors occur during the transfer. It could also show the absence of flow control and error control mechanisms, which are typically included in more complex protocols. The DFD can help to clarify the basic functioning of the simplest protocol, making it easier to understand and implement.
An illustration of a Stop-and-wait protocol-based exchange is shown in this figure. It's still simple to understand. Following the transmission of a frame, the sender awaits the receiver's answer. Send the following frame after waiting for the acknowledgment, or ACK, from the receiving end. Keep in mind that every time there are two frames, the sender is involved in four events and the receivers are involved in two events.
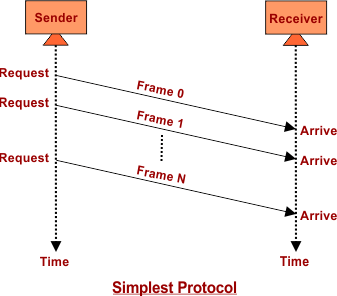
2. STOP-AND-WAIT Protocol - Stop and wait is a protocol that is used for reliable data transmission in a noiseless channel. In this protocol, the sender sends a single packet at a time and waits for an acknowledgment (ACK) from the receiver before sending the next packet. This way, the sender can ensure that each packet is received by the receiver and has been successfully processed. If the sender does not receive an ACK within a certain time frame, the packet is considered lost and must be retransmitted.
The stop and wait protocol is simple and efficient, but it has one major drawback. Because only one packet can be transmitted at a time, the overall data transmission rate is relatively slow. To overcome this limitation, the sliding window protocol was developed. In the sliding window protocol, multiple packets can be transmitted at the same time, allowing for faster data transmission. Despite this limitation, the stop and wait protocol is still widely used in many applications due to its simplicity and reliability.
- The flow of data frames at the receiver side may become too fast for it to be processed, causing the need for temporary storage.
- However, the limited storage space of the receiver may result in the loss or discarding of frames, or even denial of service.
- To prevent this, the sender must slow down their rate of transmission, which is achieved through the use of ACK messages from the receiver.
- The sender sends a single frame and waits for confirmation from the receiver before sending the next one, adding flow control to the previous protocol.
- The communication remains unidirectional for data frames, but ACK frames flow in the opposite direction.
Flow Diagram
The flow diagram of the Stop-and-wait protocol in a noiseless channel involves the following steps:
- The sender transmits a data frame to the receiver.
- The sender waits for an acknowledgment (ACK) from the receiver.
- The receiver processes the received data frame.
- The receiver sends an ACK to the sender to confirm receipt of the data frame.
- The sender continues to transmit the next data frame, repeating the process from step i.
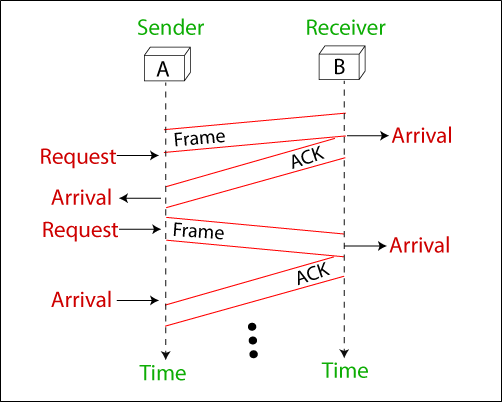
In this protocol, the sender sends one frame at a time and stops until it receives an ACK from the receiver. This prevents the receiver from becoming overwhelmed with incoming frames and ensures reliable data transmission. Additionally, the ACK frames are used for flow control, allowing the sender to adjust the transmission rate based on the receiver's processing capacity.
CONCLUSION:
The main difference between the two protocols is that the Simplest Protocol has no flow control and error control mechanisms, while the Stop-and-Wait Protocol employs a flow control mechanism through the use of ACK frames.
In the Simplest Protocol, the recipient is always expected to be ready to receive any frames sent by the sender, so no acknowledgment is needed. In the Stop-and-Wait Protocol, the sender must wait for an acknowledgment from the receiver before sending the next frame.
Another difference between the two protocols is that the Simplest Protocol is unidirectional, while the Stop-and-Wait Protocol is bi-directional. In the Simplest Protocol, data frames can only move in one direction, from sender to receiver, while in the Stop-and-Wait Protocol, both data frames and ACK frames can travel in both directions.
In conclusion, the Simplest Protocol is a basic and straightforward protocol suitable for noiseless channels, while the Stop-and-Wait Protocol adds additional reliability through flow control mechanisms and is more suitable for noisy channels.
Noisy Channel protocols
A Noisy Channel Protocol is a type of communication protocol that is used in communication systems where the transmission channel may introduce errors into the transmitted data. This type of protocol is designed to deal with errors in the communication channel and ensure that the data being transmitted is received accurately at the receiver end. The main objective of Noisy Channel Protocols is to minimize the error rate in the transmitted data by using techniques such as error detection and correction, flow control, and retransmission of lost or corrupted data frames. Some examples of Noisy Channel Protocols include the Stop-and-Wait Protocol, the Sliding Window Protocol, and the Automatic Repeat Request (ARQ) Protocol.
1. STOP-AND-WAIT ARQ Protocol - The Stop and Wait protocol is a protocol used for reliable data transmission over a noisy channel. In this protocol, the sender only sends one frame at a time and waits for an acknowledgment (ACK) from the receiver before sending the next frame. This helps to ensure that the receiver receives the data correctly and eliminates the need for retransmission in the case of errors caused by the noisy channel. The sender continuously monitors the channel for errors, and if an error is detected, it waits for the next ACK before resending the frame. This protocol adds error control to the basic unidirectional communication of data frames and ACK frames in the opposite direction.
Flow Diagram
A data flow diagram in the Stop-and-Wait protocol in a noisy channel can be used to describe the flow of data between the sender and the receiver. This diagram generally includes the following components:
- Sender: The sender sends data frames one at a time, and waits for a response (ACK or NACK) from the receiver before sending the next data frame.
- Receiver: The receiver receives the data frames and processes them. If the frame is received correctly, the receiver sends an ACK signal to the sender. If the frame is not received correctly, the receiver sends a NACK signal to the sender.
- Noisy Channel: The noisy channel is the medium through which the data frames are transmitted from the sender to the receiver. The channel can add noise to the data frames, resulting in errors and corruption of the data.
- Error Detection: The receiver uses error detection techniques such as checksums to detect errors in the received data frames.
- Error Correction: If an error is detected, the receiver sends a NACK signal to the sender, requesting a retransmission of the frame.
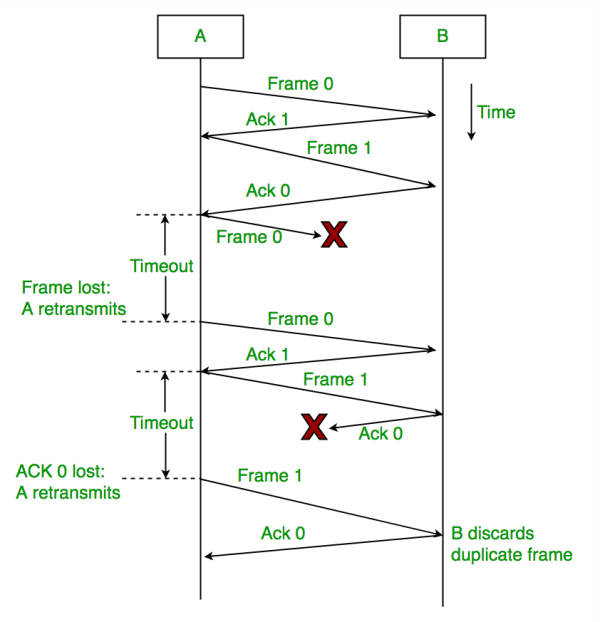
In this protocol, the sender only sends one data frame at a time and waits for a response from the receiver before sending the next frame. This ensures that the receiver has enough time to process each frame before receiving the next one. The Stop-and-Wait protocol is reliable, but has low throughput compared to other protocols.
2. GO-BACK-N ARQ Protocol - The Go-Back-N Automatic Repeat Request (ARQ) protocol is a type of error-control protocol used in data communication to ensure reliable delivery of data over a noisy channel. In a noisy channel, the probability of errors in the received packets is high, and hence, there is a need for a mechanism to detect and correct these errors.
The Go-Back-N ARQ protocol is a type of sliding window protocol where the sender transmits a window of packets to the receiver, and the receiver sends back an acknowledgment (ACK) to the sender indicating successful receipt of the packets. In case the sender does not receive an ACK within a specified timeout period, it retransmits the entire window of packets.
Flow Diagram
The flow diagram that illustrates the operation of the Go-Back-N ARQ protocol in a noisy channel:
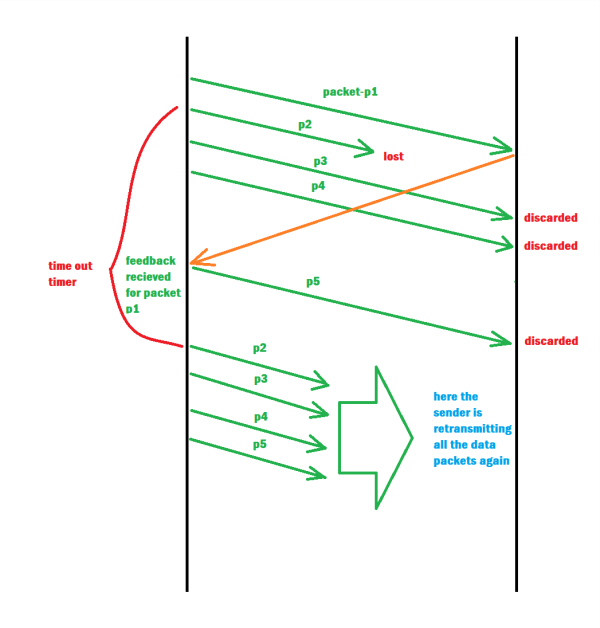
Sender Side:
- The sender transmits a window of packets to the receiver, starting with sequence number i and ending with sequence number i + N - 1, where N is the window size.
- The sender sets a timer for each packet in the window.
- The sender waits for an acknowledgment (ACK) from the receiver.
Receiver Side:
- The receiver receives the packets and checks for errors.
- If a packet is received correctly, the receiver sends an ACK back to the sender with the sequence number of the next expected packet.
- If a packet is received with errors, the receiver discards the packet and sends a negative acknowledgment (NAK) to the sender with the sequence number of the next expected packet.
Sender Side (in case of no ACK received):
- If the sender does not receive an ACK before the timer for a packet expires, the sender retransmits the entire window of packets starting with the packet whose timer expired.
- The sender resets the timer for each packet in the window.
- The sender waits for an ACK from the receiver.
Sender Side (in case of NAK received):
- If the sender receives a NAK from the receiver, the sender retransmits only the packets that were not correctly received by the receiver.
- The sender resets the timer for each packet that was retransmitted.
- The sender waits for an ACK from the receiver.
The above steps are repeated until all packets have been successfully received by the receiver. The Go-Back-N ARQ protocol provides a reliable mechanism for transmitting data over a noisy channel while minimizing the number of retransmissions required.
3. SELECTIVE REPEAT ARQ Protocol - The Selective Repeat ARQ protocol is a type of error-control protocol used in data communication to ensure reliable delivery of data over a noisy channel. Unlike the Go-Back-N ARQ protocol which retransmits the entire window of packets, the Selective Repeat ARQ protocol retransmits only the packets that were not correctly received.
In the Selective Repeat ARQ protocol, the sender transmits a window of packets to the receiver, and the receiver sends back an acknowledgment (ACK) to the sender indicating successful receipt of the packets. If the receiver detects an error in a packet, it sends a negative acknowledgment (NAK) to the sender requesting retransmission of that packet.
In the Selective Repeat ARQ protocol, the sender maintains a timer for each packet in the window. If the sender does not receive an ACK for a packet before its timer expires, the sender retransmits only that packet.
At the receiver side, if a packet is received correctly, the receiver sends back an ACK with the sequence number of the next expected packet. However, if a packet is received with errors, the receiver discards the packet and sends back a NAK with the sequence number of the packet that needs to be retransmitted.
Unlike Go-Back-N ARQ, in Selective Repeat ARQ, the receiver buffer is maintained for all packets that are not in sequence. When a packet with a sequence number different from the expected sequence number arrives at the receiver, it is buffered, and the receiver sends an ACK for the last in-order packet it has received.
If a packet with a sequence number that the receiver has already buffered arrives, it is discarded, and the receiver sends an ACK for the last in-order packet it has received.
In summary, the Selective Repeat ARQ protocol provides a reliable mechanism for transmitting data over a noisy channel while minimizing the number of retransmissions required. It retransmits only the packets that were not correctly received and buffers packets that arrive out of order to reduce the number of retransmissions required.
Flow Diagram
The flow diagram that illustrates the operation of the Selective Repeat ARQ protocol in a noisy channel:
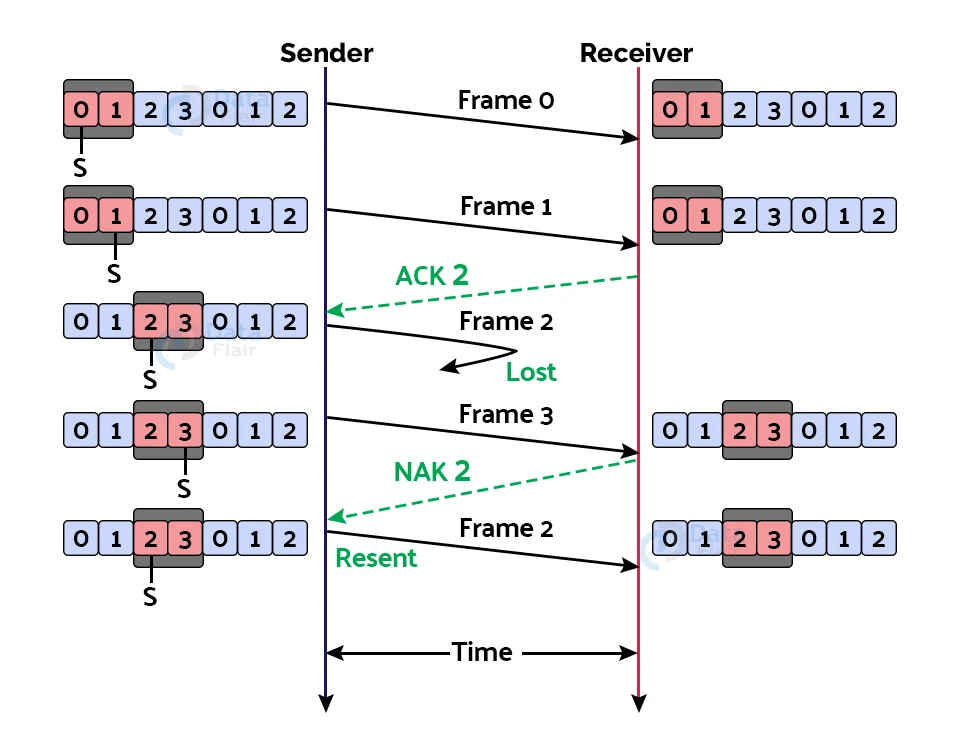
Sender Side:
- The sender transmits a window of packets to the receiver, starting with sequence number i and ending with sequence number i + N - 1, where N is the window size.
- The sender sets a timer for each packet in the window.
- The sender waits for an acknowledgment (ACK) from the receiver.
Receiver Side:
- The receiver receives the packets and checks for errors.
- If a packet is received correctly and is in order, the receiver sends an ACK back to the sender with the sequence number of the next expected packet.
- If a packet is received with errors or is out of order, the receiver discards the packet and sends a negative acknowledgment (NAK) to the sender with the sequence number of the packet that needs to be retransmitted.
- The receiver buffers out-of-order packets and sends an ACK for the last in-order packet it has received.
Sender Side (in case of no ACK received):
- If the sender does not receive an ACK before the timer for a packet expires, the sender retransmits only that packet.
- The sender resets the timer for the retransmitted packet.
- The sender waits for an ACK from the receiver.
Sender Side (in case of NAK received):
- If the sender receives a NAK from the receiver, the sender retransmits only the packets that were not correctly received.
- The sender resets the timer for each packet that was retransmitted.
- The sender waits for an ACK from the receiver.
The above steps are repeated until all packets have been successfully received by the receiver. The Selective Repeat ARQ protocol provides a reliable mechanism for transmitting data over a noisy channel while minimizing the number of retransmissions required. It retransmits only the packets that were not correctly received, and buffers out-of-order packets to reduce the number of retransmissions required.
CONCLUSION:
A. Stop-and-Wait ARQ:
- The simplest of the three protocols.
- The sender transmits one packet at a time and waits for an acknowledgment (ACK) from the receiver before sending the next packet.
- If the ACK is not received within a certain time, the sender retransmits the packet.
- Suitable for channels with low error rates, low data rates, and short transmission distances.
B. Go-Back-N ARQ:
- The sender transmits a window of packets to the receiver.
- If the receiver detects an error in a packet, it sends a negative acknowledgment (NAK) to the sender requesting retransmission of that packet, as well as all subsequent packets in the window.
- The sender retransmits the entire window of packets that were not correctly received.
- Suitable for channels with moderate to high error rates and moderate data rates.
C. Selective Repeat ARQ:
- The sender transmits a window of packets to the receiver.
- If the receiver detects an error in a packet, it sends a NAK to the sender requesting retransmission of that packet only.
- The sender retransmits only the packets that were not correctly received.
- The receiver buffers out-of-order packets to reduce the number of retransmissions required.
- Suitable for channels with moderate to high error rates, high data rates, and long transmission distances.
In summary, Stop-and-Wait ARQ is the simplest and most reliable protocol but not suitable for high data rates. Go-Back-N ARQ is suitable for channels with moderate to high error rates, and Selective Repeat ARQ is suitable for high data rates and long transmission distances. The choice of protocol depends on the characteristics of the communication channel and the requirements of the application.


