Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Challenge Response Authentication Mechanism (CRAM)
The most popular method for authenticating operations is the Challenge Response Authentication Mechanism (CRAM). They are a collection of protocols in which one side issues a challenge (to be addressed) and the other side is required to respond with the right response (to be verified/checked) in order to be authenticated.
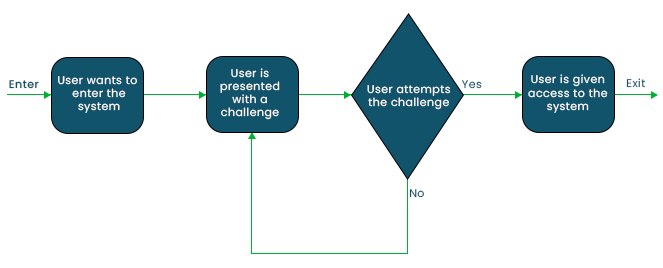
Challenge questions come in two flavours:
- As the name implies, static questions take a static approach to the challenge choice. The user can choose his challenge and confirm his identity. Consider the FORGET PASSWORD function in email services as an illustration. The "security question" that you have saved as part of the account setup is a static challenge. It is not anticipated that the right response to those questions would alter over time.
- Dynamic questions use a dynamic selection and authentication process for the Challenge. The tasks are chosen at random with the assumption that since the user is the genuine one, they will know the correct response.
Methods of CRAM execution -
1. CAPTCHA:
The Fully Automated Public Turing Test to Distinguish Between Computers and People Spam and the automatic creation of new accounts on websites or for email are both stopped by CAPTCHA.
2. Secure Shell, or SSH
SSH is a cryptographic network protocol that enables the secure operation of network services over insecure networks.
3. Password:
The password is transmitted to the server, where it is checked by comparison with the right password.
4. A variation of CRAM called Salted Challenge Response Authentication Mechanism (SCRAM):
To ensure that the password is only used once, the challenge is hashed and salted. Instead than matching the plain text password itself, the server compares the hash against the hash of the correct password. Because the password may only be used once, it cannot be divulged, preventing Man-in-the-Middle and replay attacks.
5. Biometrics:
Every time a user wishes to verify himself, he must provide his unique biometric information (such as a retina scan or fingerprint scan) to the authenticating system for verification.
How to Use Challenge-Response
A challenge-response barrier is a security measure used to keep assets safe from unauthorised users, activities, programmes, and internet of things (IoT) devices. It requires cyber attackers to complete a series of challenges in order to bypass the security barrier and gain access to additional materials. A commercial bank, for example, creates a multifactor authentication (MFA) process using challenge-response authentication. Using multiple CRAMs, this process authenticates a user's identity.
A two-factor authentication (2FA) process might entail entering a password and receiving a code via email. An MFA variant may also ask a personal question, such as "What is your mother's maiden name?" However, account logins aren't the only use of challenge-response authentication.
CRAM Utilise cases
- To distinguish a computer from a person:
The user is shown an image, which is typically difficult to read at first look, and is then requested to input by deciphering the characters in the image. To stop bots from accessing the system, the input is then compared with the actual characters.
- In training Machine Learning models:
An image is cut up and confused before being submitted to the user for some form of human user-verifiable authentication. The input is used to validate user input. The user's response and the answer provided by the ML model are compared. The "task" is to choose the correct parts from the jumbled-up image. in Google CAPTCHA authentication frequently observed.
- For the purpose of login (authentication):
The proper password, which is already saved on the server you are attempting to access, is compared (directly or indirectly) with the one you entered to see if they match.
Typical CRAM attacks include:
- Eavesdropping
- Phishing Attacks
- Pharming Attacks
- Man-In-The-Middle Attacks
- DNS Cache Poisoning Attacks
- Trojans Attacks
- Man-In-The-Phone Attacks
- Browser Poisoning Attacks
- Dictionary Attacks
- Brute-Force Attacks
- zero-knowledge password proof
- Reusable password attacks
Limitations -
One fundamental issue with passwords is that they are used repeatedly. When a password is received by the server, the server cannot determine whether or not the password is being entered by the real user.
Newer CRAMs also use cryptography to match the hash of the passwords rather than the plain passwords.
Some cryptographic CRAM examples -
- SCRAM is an abbreviation for Salted Challenge Response Authentication Mechanism.
- CRAM-MD5


