Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Network Layer Security | SSL Protocols
Four Secured Socket Layer (SSL) Protocols
Without demonstrating how SSL completes its tasks, we have only talked about the concept of SSL in the previous section. <Please add the link to the previous file of SSL and SSL Architecture> According to the diagram below, SSL defines four protocols over two layers:
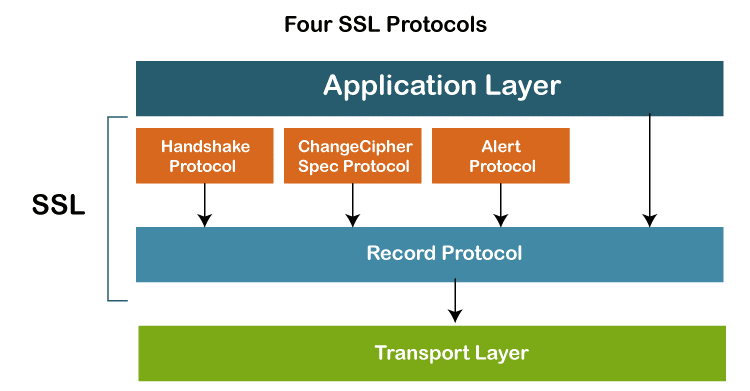
The transport mechanism is the Record Protocol. Along with the information from the application layer, it also contains messages from three more protocols. The payload of the transport layer, which is often TCP, is a message from the Record Protocol. The Record Protocol's security parameters are provided via the Handshake Protocol. It creates a cypher set, offers keys, and specifies security parameters. Additionally, if necessary, it authenticates both the client and the server. The ChangeCipherSpec Protocol is used to announce when cryptographic secrets are ready. Anomalies are reported via the Alert Protocol. In this part, we'll briefly go through all four protocols.
Handshake Protocol
The Handshake Protocol employs messages to exchange data for constructing the cryptographic secrets as well as to negotiate the cypher suite, and authenticate the server to the client and the client to the server as necessary. The four phases of the handshake are depicted in the following figure.
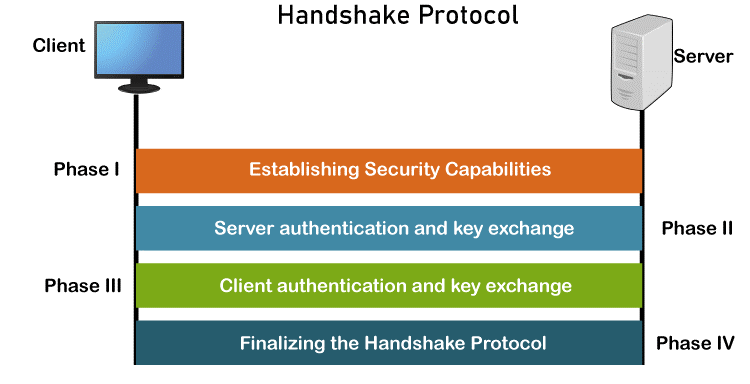
First Phase - Establishing Security Capabilities
The client and server disclose their security capabilities in Phase I and pick the ones that work best for them both. A session ID is created during this stage, and the cypher suite is decided upon. The parties select a specific compression technique. In order to create a master secret, as we have seen before, two random integers are finally chosen, one by the client and one by the server. Following Phase I, both the client and the server are aware of the SSL version, the cryptographic techniques, the compression technique, and the two random integers used to generate the key.
Second Phase - Server Authentication and Key Exchange
Authentication for the server takes place in Phase II, if necessary. In addition to requesting certificates from the client, the server has the option of sending its certificate and public key. When Phase II is complete, the client and server have been authenticated, and if necessary, the client has access to the server's public key.
Third Phase - Client Authentication and Key Exchange
Phase III is used to verify the client's identity. After Phase III, the client and server can verify each other and share the pre-master secret.
Fourth Phase - Finalizing and Finishing
In Phase IV, the client and server exchange messages to finalize the Handshake Protocol and alter the cypher parameters.
ChangeCipherSpec Protocol
As we've seen, the Handshake Protocol allows for the gradual formation of cryptographic secrets as well as the negotiation of the cypher suite. When are these parameters or secrets available for usage by the two parties, then? SSL requires that these parameters or secrets cannot be used by the parties until they have exchanged or received a specific message, the ChangeCipherSpec message, which is done so during the Handshake Protocol and is specified in the ChangeCipherSpec Protocol. The reason is that the problem goes beyond simple message sending and receiving. Two states, not one, are required for the sender and the receiver. The parameters and secrets are tracked by one state, the pending state. The active state, which is the other state, contains the parameters and secrets that the Record Protocol uses to sign, validate, or encrypt and decode messages. Additionally, read (inbound) and write (outbound) data are stored in each state separately.
Alert Protocol
SSL reports problems and strange conditions using the Alert Protocol. It just makes use of one message to describe the issue and its severity (warning or fatal).
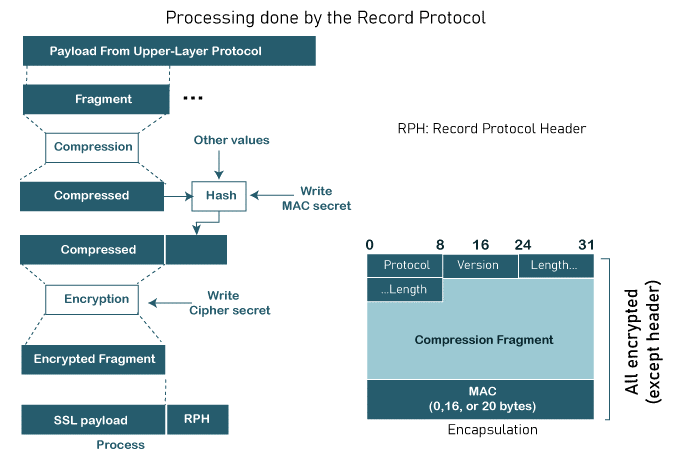
Record Protocol
Messages from the top layer are transmitted through the Record Protocol (Handshake Protocol, ChangeCipherSpec Protocol, Alert Protocol, or application layer). The message is split into pieces and, if desired, compressed; the compressed message is then added to by adding a MAC with the agreed-upon hashing algorithm. Utilizing the agreed-upon encryption procedure, the compressed fragment and MAC are both encrypted. The encrypted communication is then supplemented with the SSL header. This process at the sender is shown in the given Figure. The recipient reverses the process.