Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Quantum Networking
Introduction to Quantum Networking
Quantum networking is a rapidly growing field of research and development that seeks to combine the principles of quantum mechanics and information theory to enable secure and efficient communication between quantum devices. Traditional classical networks transmit the information as binary digits (bits) that are either a 0 or 1. In contrast, quantum networks use quantum bits (qubits), which can exist in multiple states simultaneously, creating more complex communication protocols that are inherently resistant to eavesdropping.
The key advantage of quantum networking is the ability to transmit information in a fundamentally secure way due to the principles of quantum mechanics. For example, quantum key distribution (QKD) protocols can be used to establish a secret key between two parties, allowing them to communicate with complete privacy. Even if an eavesdropper attempts to intercept the communication, the act of measurement changes the state of the qubits. It can be detected, alerting the legitimate parties to the presence of the eavesdropper.
Quantum networking has a wide range of potential applications, including secure communication, distributed quantum computing, and quantum internet services. For example, quantum networks could enable secure communication between financial institutions or government agencies or facilitate the creation of distributed quantum computing platforms that allow multiple parties to work together on complex computational problems.
Despite its many potential advantages, quantum networking is still in the early stages of development and faces many technical and practical challenges. For example, creating and manipulating qubits is a difficult and delicate process that requires precise control over the environment in which the qubits are located. Additionally, the development of practical quantum network architectures and protocols remains an active area of research.
Quantum networking represents a fascinating and rapidly growing field with enormous potential to revolutionize the way we communicate and process information in the future.
Advantages of Quantum Networking
Quantum networking has several potential advantages over classical networks, including:
- Security: Quantum networking enables inherently secure communication through the use of quantum encryption protocols such as quantum key distribution (QKD). The laws of quantum mechanics prevent any unauthorized party from accessing or altering the quantum information being transmitted, making quantum networks virtually impenetrable to eavesdropping and hacking.
- Speed: Quantum computing and communication are much faster than classical computing and communication in certain applications. For example, quantum networks can be used to factor large numbers exponentially faster than classical computers, which is useful for breaking encryption schemes. Additionally, quantum teleportation allows for instantaneous transmission of quantum information over any distance.
- Distance: Quantum networking has the potential to overcome the limitations of distance imposed on classical communication due to signal attenuation and noise. Quantum networks can be used to transmit information over long distances using quantum repeaters, which amplify and regenerate quantum signals as they travel.
- Sensing and measurement: Quantum networking can be used to improve sensing and measurement capabilities beyond what is possible with classical systems. For example, quantum sensors can be used to detect and measure minute changes in temperature, magnetic fields, and other physical parameters with extreme precision.
- Distributed computing: Quantum networking can facilitate the creation of distributed quantum computing platforms that allow multiple parties to work together on complex computational problems. This can enable new scientific discoveries and technological breakthroughs in areas such as drug discovery, materials science, and cryptography.
These are just a few of the potential advantages of quantum networking, and as the technology continues to develop, new applications and benefits are likely to emerge.
Limitations of Quantum Networking
While quantum networking has many potential advantages, there are also several challenges and limitations that need to be addressed, including:
- Technical complexity: Quantum networking is a technically complex field that requires precise control over the environment in which quantum devices operate. Creating and manipulating qubits is a difficult and delicate process that requires advanced equipment and expertise.
- Fragility: Quantum systems are fragile and susceptible to noise and environmental fluctuations. Any disturbances or errors in the system can cause the qubits to decohere, leading to errors in transmitting or processing quantum information.
- Limited scalability: Current quantum networking technologies are limited in terms of scalability. Creating large-scale quantum networks that can transmit and process large amounts of quantum information over long distances is challenging.
- High cost: Quantum networking technologies are currently expensive to develop, operate, and maintain. This makes it difficult to implement large-scale quantum networks, particularly in resource-constrained settings.
- Limited practical applications: While there are many potential applications of quantum networking, many of them are still theoretical or require further development. This makes it challenging to justify the investment required to develop quantum networking technologies.
While quantum networking has the potential to revolutionize the way we communicate and process information, there are several challenges and limitations that need to be addressed before the technology can be widely adopted. Researchers are working to address these challenges and improve the performance and scalability of quantum networks. Still, it will likely be several years before quantum networking technologies become practical and affordable enough to be widely adopted.
Quantum Networking Architecture
Quantum networking architectures are the physical implementations of quantum networks that enable the transmission and processing of quantum information. There are several different architectures that have been proposed or implemented for quantum networking, including:
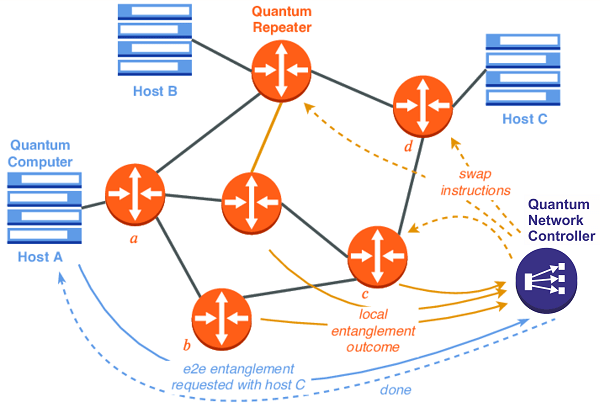
- Point-to-point quantum links: These are the simplest type of quantum network, consisting of two or more devices that are directly connected by a quantum channel. Point-to-point links can be used for tasks such as quantum key distribution and quantum teleportation.
- Quantum repeater networks: Quantum repeaters are devices that amplify and regenerate quantum signals as they travel long distances, enabling quantum communication to extend beyond the limits of direct point-to-point links. Quantum repeaters can be used to create a network of interconnected quantum devices.
- Quantum memories: Quantum memories are devices that can store and retrieve quantum information for later use. They are an essential component of many quantum network architectures, enabling the storage and processing of quantum information.
- Entanglement swapping networks: Entanglement swapping is a process by which two separate pairs of entangled particles can be used to create a new entangled pair. Entanglement swapping networks enable the creation of complex entangled states across multiple quantum devices.
- Hybrid classical-quantum networks: Hybrid networks combine classical and quantum devices to enable the transmission and processing of both classical and quantum information. They can be used to bridge the gap between existing classical networks and emerging quantum networks.
These are just a few of the quantum networking architectures that have been proposed or implemented. Each architecture has its own advantages and limitations, and researchers are continually developing new approaches to improve the performance and scalability of quantum networks.
Quantum Network Applications
Quantum networking has the potential to enable many new applications and technologies, including:
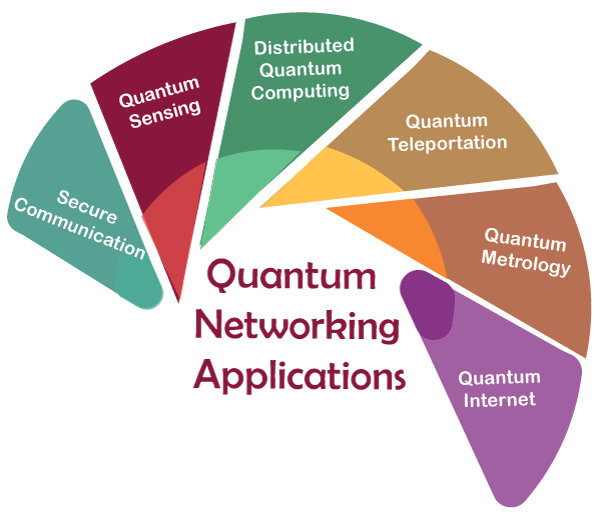
- Secure Communication: Quantum networking enables inherently secure communication through the use of quantum encryption protocols such as quantum key distribution (QKD). This can be used to secure sensitive communication channels, such as those used in banking, government, and military settings.
- Quantum Sensing: Quantum sensors can be used to detect and measure physical parameters such as temperature, magnetic fields, and gravity with extremely high precision. Quantum networks can be used to distribute and coordinate these sensors over large distances, enabling new applications in fields such as geology, seismology, and environmental monitoring.
- Distributed Quantum Computing: Quantum networks can be used to create distributed quantum computing platforms that allow multiple parties to work together on complex computational problems. This can enable new scientific discoveries and technological breakthroughs in areas such as drug discovery, materials science, and cryptography.
- Quantum Teleportation: Quantum teleportation enables the instantaneous transfer of quantum information over any distance. This can be used for applications such as secure communication, remote sensing, and distributed computing.
- Quantum Metrology: Quantum metrology uses quantum systems to improve the precision of measurements beyond what is possible with classical systems. This can be used in applications such as timekeeping, navigation, and GPS.
- Quantum Internet: A quantum internet is a hypothetical future network that uses quantum technologies to enable new applications such as secure communication, distributed quantum computing, and quantum sensing. It is envisioned as a global network of interconnected quantum devices and networks that enables the seamless transmission and processing of quantum information.
These are just a few examples of the potential applications of quantum networking, and as the technology continues to develop, new applications and benefits are likely to emerge.


