Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Synchronous Optical Network (SONET)
Synchronous Optical Network, or SONET. A communication protocol called SONET was created by Bellcore and is used to send a lot of data over relatively long distances using optical fibre. Multiple digital data streams are transmitted simultaneously over the optical fibre with SONET.
Key Ideas
- Bellcore developed
- North American usage
- established by ANSI (American National Standards Institute).
- SDH (Synchronous Digital Hierarchy), which is utilised in Europe and Japan, is comparable.
Why is SONET referred to as a synchronised network?
Across the entire network, the timing of signal and equipment transmission is controlled by a single clock (the Primary Reference Clock, or PRC).
SONET Network Constituents
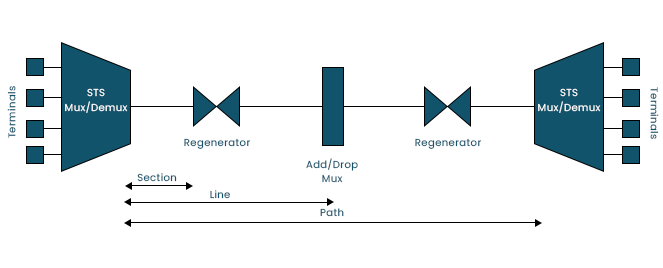
Multiplexer STS:
- performs signal multiplexing.
- optical signal from electrical signal is converted.
Demultiplexer STS:
- performs signal demultiplexing.
- optical signal to electrical signal conversion.
Regenerator:
- It is a repeater that regenerates (increases the strength of) optical signals.
Drop/Add Multiplexer:
- It enables the addition of signals from various sources to a particular path or the removal of a signal.
Why is SONET employed?
An electrical signal is changed into an optical signal by SONET so that it can travel farther.
Connections to SONET
- Section: The portion of the network that connects two nearby devices.
- Line: A section of the network that links two nearby multiplexers.
- Path: The network's end-to-end section.
Layers of SONET:
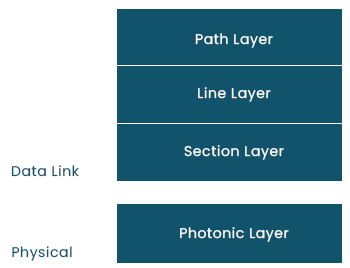
There are four functional layers in SONET:
1. Step Layer:
- It is in charge of transferring signals from their optical source to their optical destination.
- Providing path layer functions is STS Mux/Demux.
2. The Line Layer
- It is in charge of signal transmission across a real line.
- Add/Drop Mux and STS Mux/Demux both offer Line layer functions.
3. Stacking Section:
- It is in charge of signal transmission across a physical region.
- Each network device performs section layer functions.
4. Optical Layer:
- It corresponds to the OSI model's physical layer.
- It includes the optical fibre channel's physical specifications (light is present when 1 and not present when 0).
Benefits of SONET
- transmits information over long distances
- very little electromagnetic interference
- greater data rates
- Broad Bandwidth
SONET's drawbacks include:
- No standard that is compatible.
- SONET mux services are necessary for tributary services.
- Low cost and efficient for few channels.
- The SONET/SDH network management system is inadequate for managing and using the DWDM technique.
- At higher capacities, bandwidth efficiency is a problem.
- There must be more overhead.


