Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Physical Layer in OSI Model
The OSI model is the abbreviation for Open Systems Interconnection Model. It defines the transmission of data from one system to another in a computer network. For example, in the most elemental form, two systems are joined to each other using Local Area Network (LAN) cables and share data with the help of a Network Interface Card (NIC) that allows communication over a network, but if one system is based on Microsoft Windows, and the other is based on macOS, so how would these computers communicate with each other. To successfully communicate between systems of distinct architectures, the International Organization for Standardization (ISO) presented the 7-layered OSI model in 1984.
The individual layer of the OSI model is a package of protocols. This article will comprehend the physical layer of the OSI model.
The physical layer is the first and lowest layer from the bottom of the 7-layered OSI model and delivers security to hardware. This layer is in charge of data transmission over the physical medium. It is the most complex layer in the OSI model.
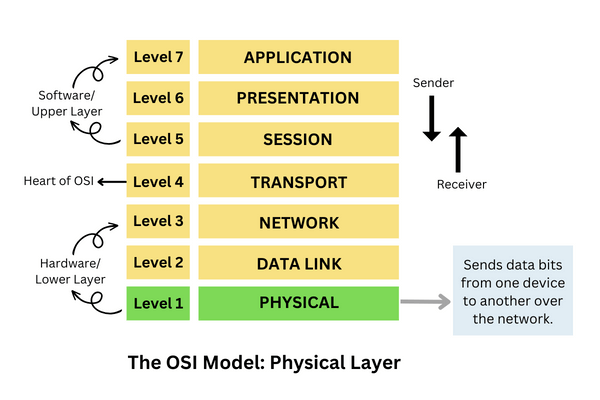
The physical layer converts the data frame received from the data link layer into bits, i.e., in terms of ones and zeros. It maintains the data quality by implementing the required protocols on different network modes and maintaining the bit rate through data transfer using a wired or wireless medium.
Attributes of the physical layer:
The physical layer has several attributes that are implemented in the OSI model:
1. Signals: The data is first converted to a signal for efficient data transmission. There are two kinds of signals:
- Analog Signals: These signals are continuous waveforms in nature and are represented by continuous electromagnetic waves for the transmission of data.
- Digital Signals: These signals are discrete in nature and represent network pulses and digital data from the upper layers.
2. Transmission media: Data is carried from source to destination with the help of transmission media. There are two sorts of transmission media:
- Wired Media: The connection is established with the help of cables. For example, fiber optic cables, coaxial cables, and twisted pair cables.
- Wireless Media: The connection is established using a wireless communication network. For example, Wi-Fi, Bluetooth, etc.
3. Data Flow: It describes the rate of data flow and the transmission time frame. The factors affecting the data flow are as follows:
- Encoding: Encoding data for transmission on the channel.
- Error-Rate: Receiving erroneous data due to noise in transmission.
- Bandwidth: The rate of transmission of data in the channel.
4. Transmission mode: It describes the direction of the data flow. Data can be transmitted in three sorts of transmission modes as follows:
- Simplex mode: This mode of communication is a one-way communication where a device can only send data. Examples are a mouse, keyboard, etc.
- Half-duplex mode: This mode of communication supports one-way communication, i.e., either data can be transmitted or received. An example is a walkie-talkie.
- Full-duplex mode: This mode of communication supports two-way communication, i.e., the device can send and receive data at the same time. An example is cellular communication.
5. Noise in transmission: Transmitted data can get corrupted or damaged during data transmission due to many reasons. Some of the reasons are mentioned below:
- Attenuation: It is a gradual deterioration of the network signal on the communication channel.
- Dispersion: In the case of Dispersion, the data is dispersed and overlapped during transmission, which leads to the loss of the original data.
- Data Delay: The transmitted data reaches the destination system outside the specified frame time.
The physical layer performs various functions and services:
- It transfers data bit by bit or symbol by symbol.
- It performs bit synchronization, which means that only one bit needs to be transferred from one system to another at a time. There should be no overlapping of bits during transmission. Bit synchronization can be achieved by providing a clock.
- Bit rate control defines how many bits per second can be transmitted, i.e., the number of bits sent per second.
- The physical layer is responsible for knowing the arrangements made between devices in networks called physical topologies, such as mesh, ring, bus, and star.
- The transmission mode in which data is transmitted, and there are three modes of transmitting data: full-duplex, half-duplex, and simplex.
- It is responsible for point-to-multipoint, point-to-point, or multipoint line configurations.
- It is responsible for flow control and start-stop signaling in asynchronous serial communication.
- Signal processing of physical signals such as training sequence, pulse shaping, equalization filtering, and others.
- It provides bit-interleaving and another channel coding.
- It is responsible for serial or parallel communication.
- It provides a standardized interface for physical transmission media, including electrical specifications for transmission line signal levels, mechanical specifications for electrical cables and connectors, radio interfaces, and wireless IR communication links, IR specifications.
- The physical layer is responsible for modulation, which means the conversion of information into radio waves by adding the data to an optical nerve signal or electrical signal.
- This layer is responsible for circuit switching.
- This layer is concerned with auto-negotiation. Signals are mainly of two sorts, digital signals & analog signals. The physical layer decides which signal will be used to transfer the data from one point to another.
- It also avoids collisions between data flowing in the network due to the irretrievability of data packets.
- It is responsible for the translation of data received from the data link layer for further transmission.
Physical Topology:
Physical topology refers to the specification or structure of the connections of the network between the devices where the transmission will happen. There are four types of topologies, which are as follows:
Star Topology:
Star topology is a sort of network topology in which each node or device in the network is individually joined to a central node, which can be a switch or a hub. This topology looks like a star, due to which this topology is called star topology.
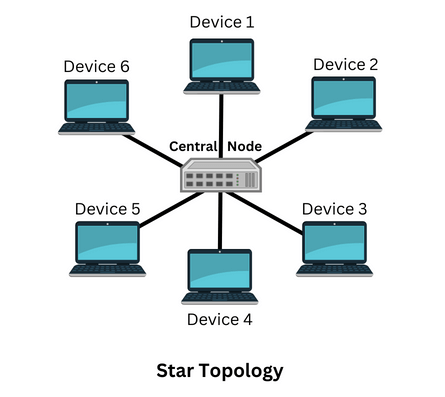
Hub does not provide route data, but it transmits data to other devices connected to it. The advantage of this topology is that if one cable fails, the device connected to that cable is affected, and not the others.
Bus Topology:
Bus topology comprises a single communication line or cable that is connected to each node. The backbone of this network is the central cable, and each node can communicate with other devices through the central cable.
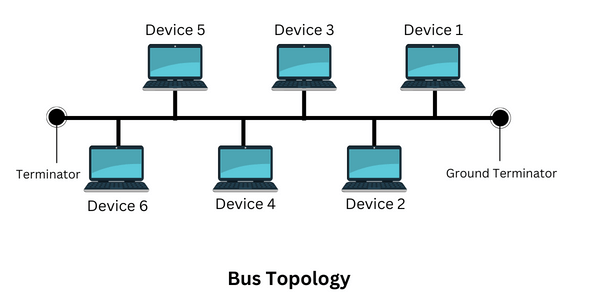
The signal goes from the ground terminator to the other terminator of the wire. The terminator stops the signal once it reaches the end of the wire to avoid signal bounce. Each computer communicates independently with other computers in what is called a peer-to-peer network. Each computer has a unique address, so if a message is to be sent to a specific computer, the device can communicate directly with that computer.
The advantage of bus topology is that collapse in one device will not affect other devices. The bus topology is not expensive to build because it uses a single wire and works well for small networks.
Ring Topology:
In a ring topology, the devices are connected in the form of a ring so that each device has two neighbors for communication. Data moves around the ring in one direction.
As you can see below, all four devices are connected to each other in the form of a ring. Each device has two neighbors. Node 2 and Node 4 are neighbors of Node 1; similarly, Node 1 and Node 3 are neighbors of Node 2, and so on.
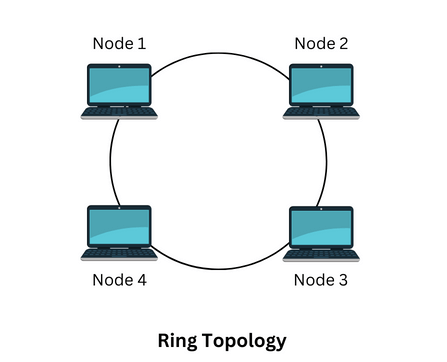
The advantage of ring topology is that if you want to add another device to the ring, you will need an additional cable to do so. Similarly, you can remove a device and join the wires.
Mesh Topology:
In a mesh topology, each system is directly joined to every other system. The advantage of mesh topology is that there will be no traffic issues as each device has a dedicated communication line. If one system is not functioning, it will not affect other devices. It provides more security or privacy.
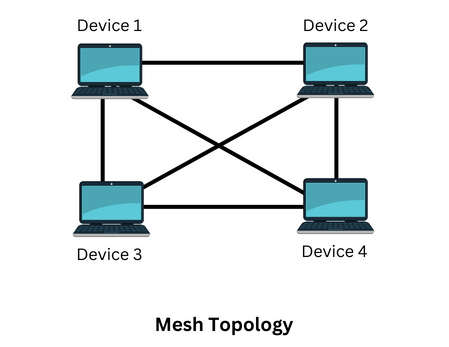
The drawback of mesh topology is that it is expensive and more complex than other topologies.
Importance of the physical layer:
- Without proper data conversion at the physical level, the network cannot function.
- The physical layer is responsible for maintaining communication between the hardware and the network mode.
- It handles the data flow rate of the data to be transmitted along with the timeframe of the transmitted data.
Conclusion:
- You studied the physical layer in OSI model in this article. The physical layer provides the hardware needed to transmit and receive bits over a network link.
- You have studied the attributes of the physical layer, such as types of signals used for data transmission, wired and wireless media of transmission, rate of data flow, and noise in transmission.
- You have read about the various functions and responsibilities of the physical layer.
- You have studied physical topologies such as star topology, bus topology, ring topology, and mesh topology.
- Finally, you have gained knowledge about the importance of the physical layer in the OSI model.


