Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
SSH Meaning| SSH Protocol
SSH stands for Secure Shell or Secure Socket Shell. It is a cryptographic network protocol that allows two computers to communicate and share the data over an insecure network such as the internet. It is used to login to a remote server to execute commands and data transfer from one machine to another machine.
The SSH protocol was developed by SSH communication security Ltd to safely communicate with the remote machine.
Secure communication provides a strong password authentication and encrypted communication with a public key over an insecure channel. It is used to replace unprotected remote login protocols such as Telnet, rlogin, rsh, etc., and insecure file transfer protocol FTP.
Its security features are widely used by network administrators for managing systems and applications remotely.
The SSH protocol protects the network from various attacks such as DNS spoofing, IP source routing, and IP spoofing.
A simple example can be understood, such as suppose you want to transfer a package to one of your friends. Without SSH protocol, it can be opened and read by anyone. But if you will send it using SSH protocol, it will be encrypted and secured with the public keys, and only the receiver can open it.
Before SSH:
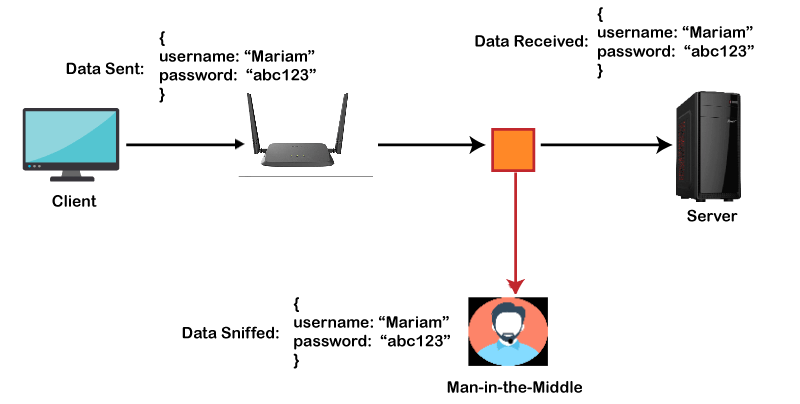
After SSH:
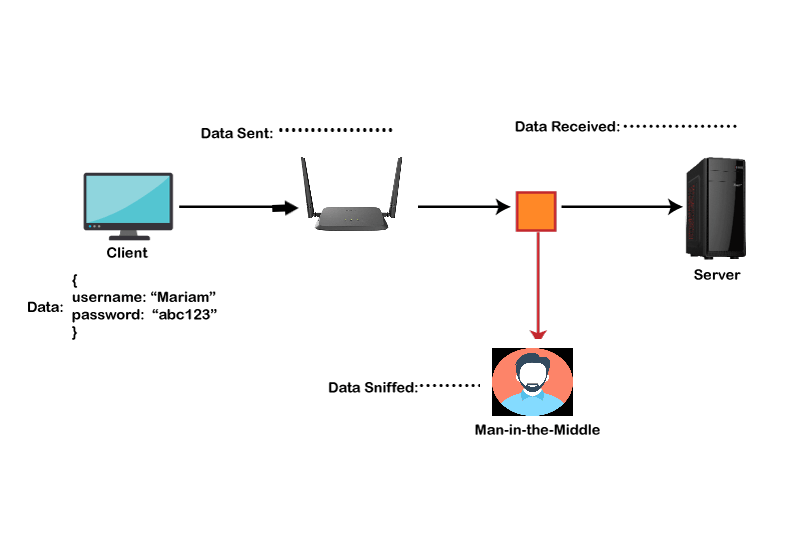
Usages of SSH protocol
The popular usages of SSH protocol are given below:
- It provides secure access to users and automated processes.
- It is an easy and secure way to transfer files from one system to another over an insecure network.
- It also issues remote commands to the users.
- It helps the users to manage the network infrastructure and other critical system components.
- It is used to log in to shell on a remote system (Host), which replaces Telnet and rlogin and is used to execute a single command on the host, which replaces rsh.
- It combines with rsync utility to backup, copy, and mirror files with complete security and efficiency.
- It can be used for forwarding a port.
- By using SSH, we can set up the automatic login to a remote server such as OpenSSH.
- We can securely browse the web through the encrypted proxy connection with the SSH client, supporting the SOCKS protocol.
How does SSH Works?
The SSH protocol works in a client-server model, which means it connects a secure shell client application (End where the session is displayed) with the SSH server (End where session executes).
As discussed above, it was initially developed to replace insecure login protocols such as Telnet, rlogin, and hence it performs the same function.
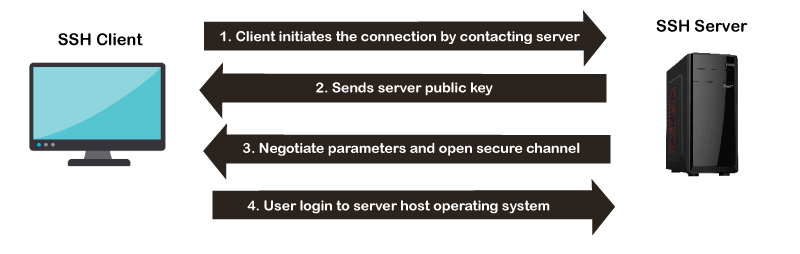
The basic use of SSH is to connect a remote system for a terminal session and to do this, following command is used:
- ssh UserName@SSHserver.test.com
The above command enables the client to connect to the server, named server.test.com, using the ID UserName.
If we are connecting for the first time, it will prompt the remote host's public key fingerprint and ask to connect. The below message will be prompt:
- The authenticity of host 'sample.ssh.com' cannot be established.
- DSA key fingerprint is 01:23:45:67:89:ab:cd:ef:ff:fe:dc:ba:98:76:54:32:10.
- Are you sure you want to continue connecting (yes/no)?
To continue the session, we need to click yes, else no. If we click yes, then the host key will be stored in the known_hosts file of the local system. The key is contained within the hidden file by default, which is /.ssh/known_hosts in the home directory. Once the host key is stored in this hidden file, there is no need for further approval as the host key will automatically authenticate the connection.
History of SSH Protocol
There are 3 versions of SSH, which are given below:
- Version 1.x: The first version of SSH was launched in the year 1995 and designed by Tatu Ylönen, who was the researcher at the Helsinki University of Technology, Finland. It was known as SSH-1. In this version, there were several issues, and hence it got depreciated.
- Version 2.x: The second version is known as SSH-2, the current version of the SSH protocol. In 2006, it was opted as a Standards Track specification by the Internet Engineering Task Force (IETF). This version is not compatible with the SSH-1 protocol. It has better security features compared to SSH-1.
- Version 1.99: Version 1.99 is specified as the proto version of 2.1. It is not the actual version but a way to identify the backward compatibility.
The architecture of SSH Protocol
The SSH architecture is made-up of three well-separated layers. These layers are:
- Transport Layer
- User-authentication layer
- Connection Layer
The SSH protocol architecture is an open architecture; hence it provides great flexibility and enables SSH use for many other purposes instead of only a secure shell. In the architecture, the transport layer is similar to the transport layer security (TLS). The User-authentication layer can be used with the custom authentication methods, and the connection layer allows multiplexing different secondary sessions into a single SSH connection.
Transport Layer
The transport layer is the top layer of the TCP/IP protocol suite. For SSH-2, this layer is responsible for handling initial key exchange, server authentication, set up encryption, compression, and integrity verification. It works as an interface for sending and receiving plaintext packets with sizes up to 32, 768bytes.
User authentication Layer
As its name suggests, the user authentication layer is responsible for handling client authentication and provides various authentication methods. The authentication is done at the client-side; hence when a prompt occurs for a password, it usually for an SSH client rather than a server, and the server responds to these authentications.
This layer includes various methods of authentication; these methods are:
- Password: Password authentication is a straightforward way of authentication. It includes the feature to change the password for easy access. But it is not used by all the applications.
- Public-key: The public-key is a public key-based authentication method, which supports DSA, ECDSA, or RSA keypairs.
- Keyboard-interactive: It is one of the versatile authentication methods. In this, the server sends a prompt to enter information & the client sends it back with keyed-in responses by the user. It is used to provide a one-time password or OTP authentication.
- GSSAPI: In this method, the authentication is performed by external methods such as Kerberos 5 or NTLM, which provide the single sign-on capability to SSH sessions.
Connection Layer
The connection layer defines various channels through which SSH services are provided. It defines the concept of channels, channel requests, and global requests. One SSH connection can host different channels simultaneously and can also transfer data in both directions simultaneously. Channel requests are used in the connection layer to relay out-of-band channel-specific data, for example, the altered size of a terminal window or the exit code of a server-side process. The standard channel types of connection layer are:
- shell: It is used for terminal shells, SFTP, and exec requests.
- direct-tcpip: It is used for the client-to-server forwarded connections.
- forwarded-tcpip: It is used for the server-to-client forwarded connections.
What can be transferred with SSH protocol?
The SSH protocol can transfer the following:
- Data
- Text
- Commands
- Files
The files are transferred using the SFTP(Secure file transfer protocol), the encrypted version of FTP that provides security to prevent any threat.
Difference between SSH and Telnet
- Telnet was the first internet application protocol used to create and maintain a terminal session on a remote host.
- Both SSH and Telnet have the same functionality. Still, the main difference is that SSH protocol is secured with public-key cryptography that authenticates endpoint while setting up a terminal session. On the other hand, no authentication is provided in Telnet for the user's authentication, making it less secure.
- SSH sends the encrypted data, while Telnet sends data in plain text.
- Due to high security, SSH is the preferred protocol for public networks, while due to less security, Telnet is suitable for private networks.
- SSH runs on port no 22 by default, but it can be changed, while Telnet uses port number 23, specifically designed for the Local area network.
SSH Encryption Techniques
To make a secure transmission, SSH uses three different encryption techniques at various points during a transmission. These techniques are:
- Symmetrical Encryption
- Asymmetrical Encryption
- Hashing
Symmetrical Encryption
Only one key can be used in symmetric encryption techniques to encrypt & decrypt messages sent and received from the destination. This technique is also known as shared key encryption because both devices use the same key to encrypt the data they send and decrypt the received data.
This technique encrypts the entire SSH connection to prevent man-in-middle attacks. In this technique, one issue arises at the time of initial key exchange. As per this problem, if a third party is present during the key exchange, they could know the key and read the entire message.
The Key exchange algorithm is used to prevent this problem. With this algorithm, the secret keys can be securely exchanged without an interception.
Asymmetrical encryption is required to implement the key exchange algorithm.
Asymmetrical Encryption
In asymmetrical encryption, two different keys are used for encryption and decryption, private and public keys. The private key is private to the user only and cannot be shared with any other user, whereas the public key is shared publicly. The public key is saved on the SSH server, whereas the private key is saved locally on the SSH client; these two keys form a key pair. The message encrypted with the public key can only decrypt with the corresponding private key.
It is a much secure technique as if a third party gets the public key, and they cannot decrypt the message because they don't know the private key.
The asymmetrical encryption does not encrypt the complete SSH session. Instead, it is mainly used for the key exchange algorithm of symmetric encryption. In this, before establishing a connection, both systems (client and server) generate public-private key pairs temporarily and then share their private keys to generate the shared secret key.
After establishing a secure symmetric connection, the server uses the public key to transmit it to the client for authentication. The client can only decrypt the data if it has the private key, and hence the SSH session establishes.
Hashing
In SSH, one-way hashing is used as the encryption technique, which is another form of cryptography. The hashing technique is different from the above two methods, as it is not meant by decryption. It generates the signature or summary of information. SSH uses HMAC(Hash-based Message authentication) to ensure that messages are reached in complete and unmodified form.
In this technique, each transmitted message must have a MAC, which uses three components: symmetric key, packet sequence number, and message content. These three components form the hash function that generates a string that doesn't have any meaning, and this string is sent to the host. The host also has the same information, so they also generate a hash function, and if the generated hash matches with the received hash, it means the message is not tempered.


