Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Functions, Advantages and Disadvantages of Network Layer
Network Layer
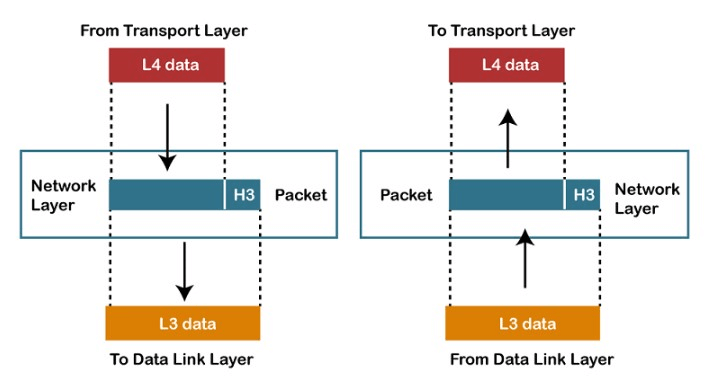
- The network layer is the computer network component that enables the node to transfer the data packets using the connection between different nodes and devices.
- The transmission of data between different devices is performed in the form of packets through different logical network paths. The network layer is the third layer of the seven-layer open system interconnection model. It provides paths to transfer the data packets in the network. The network layer also arranges and manages the possible routes for data transmission.
- The primary functions of the network layer include setting up a logical connection between the nodes, forwarding the data and routing and reporting errors during the delivery of data packets. The network layer can either support connection-oriented or connectionless networks. It cannot facilitate both types of the network simultaneously.
- The network layer is also regarded as the backbone of the OSI Model. It assigns the destination and source IP address to each data segment. It arranges all the possible paths to transfer the data in the network and then chooses the best logical path to transfer the data between the different nodes.
- The network layer act upon the requests of the layer above it. The layer above it is the transport layer. Then it generates requests forwarded to the model's lower layer, that is, the data link layer. The data regarding the source and the destination host is attached to the data frame in the data link layer. But it is the work of the network layer to interconnect several networks and determine the route for data transmission.
- It only creates the logical image of the possible communication routes, and then the best route is implemented in the physical medium. Several hardware equipments is used at this layer. These devices include routers, modems, bridges, switches and several firewalls.
- The network layer is available in all routers and hosting systems. The router's responsibility is to check the header fields of all the data packets transmitted from the source node to the destination node. The source node implements networking software at the network layer that adds the header to each data packet to be delivered. It sends and reads the data packet to ensure that the receiving node in the network properly manages it.
Functions Performed by the Network Layer
The network layer performs several functions to facilitate data transmission in a network. Some of the functions performed are as follows:
- Routing:It is the process to determine the most effective route for data transmission in the network. When a data packet arrives at the router's input link, it determines the ideal route for data transmission in the network. It determines the path that will be used to transfer the packet further in the network.
- Logical Addressing:There are two types of addressing performed in the network: logical addressing and physical addressing. The data link layer performs the physical addressing, while the network layer does the logical addressing in the OSI model. Logical addressing is also used to distinguish between the source and destination system. The network layer adds a header to the packet, which includes the logical addresses of both the sender and the receiver.
- Internetworking:This is the most important function performed by the network layer of the OSI model. It establishes the logical connection between nodes in the same or different networks.
- Fragmentation:It is the conversion of data packets into the smallest individual data units capable of being transmitted in the network.
Services offered by Network Layer
- Guaranteed delivery: this service ensures that the data packet transferred from a node reaches the final destination node in the network.
- Guaranteed delivery with bounded delay:This service ensures that the data packet sent from the source reaches the destination node within a specific delay bound. The host determines this bound in the network.
- In-Order packets:The data is divided into packets before being transmitted to the network. This service ensures that the sequence of data packets before and after the transmission is the same. Thus, the data packets must be combined sequentially.
- Guaranteed max jitter:This service guarantees that the time between two continuous transmissions is equal to the time the receiver takes to receive the two successive transmitted packets. This ensures that there is no congestion in the network.
- Security services:This layer is most vulnerable as it is directly linked to the internet. It also provides additional security measures to ensure system security in the network. This layer implements a session key between the source and destination nodes. The network layer performs the encryption on the payloads of the datagrams at the source side before transmitting them into the network. The decryption is performed at the destination end. The destination host decrypts the payload. Thus, ensuring the data integrity in the source authentication services is maintained in the network.
Issues with the design of the Network layer
- There are certain challenges that both the developer and the user need to pay attention to if they want to design the network layer and ensure that the network layer performs all the required functions. Some of the issues associated with the design of the network layer are as follows:
- Routing Packets is the primary design decision concerned with the network layer. This is essential as it determines how the packets will be transferred from one node to another in the network.
- The routes for transmitting the data in the nodes can either be static tables or dynamic tables. The routes can be predefined or modified at regular intervals.
- At any moment, if there are too many packets in the transit or the network, they will disrupt the flow of data in the network. This may create bottlenecks in the network.
- The quality of the network transmission is determined by various factors associated with the network layer, such as delays, jitter and transmission times.
- The data packets may encounter several problems while transmitting the packets from one network to another. It may be possible that the two networks have different addressing schemes than the other.
- Different protocols are required to facilitate communication between the two networks.
Advantages of Network Layer
- There are several merits to implementing the network layer in the OSI model. Some of the advantages of using a network layer are mentioned below:
- The network layer performs packetization on the data. This makes it easier to transmit the data packets in the network. This service also ensures that the packet reaches the destination node by eliminating the single points of failure during transmission.
- The router is equipment that is used in the network layer. It is responsible for creating collisions and broadcasting the domains in the network layer to reduce the traffic in the network.
- The forwarding method is implemented to transmit the data packets among the different nodes in the network.
Disadvantages of Network Layer
- Some demerits and issues cannot be addressed in the network layer. These demerits are as follows.
- The network layer design does not provide any mechanism for flow control.
- There may be instances when the network is congested because of too many datagrams in transition in the network. This may create additional burdens on the routers of the networks. If the datagrams are too many, the router may lose certain data packets in certain cases. This may lead to the loss of important information during transmission.
- Since the data packets are fragmented before being transmitted, it is impossible to implement indirect control at the network layer. This layer also lacks efficient error control mechanisms.
Protocols and their functions in Network Layer
There are several protocols implemented in the network layer of the OSI model. These protocols are responsible for establishing a connection between nodes and networks and performing encryption and checking at the network layer. Some of these network protocols are as follows:
- IP
- IPsec
- ICMP
- IGMP
- ARP
Internet Protocol (IP)
The IP defines the structures of the data packets that are responsible for encapsulating the data depending upon the IP addresses mentioned in the headers before delivering the data packets. It also defines the method of addressing the datagram. This method is useful as it helps identify the datagram's source and destination.
Given below are some examples of the Network layer protocols. These protocols are implemented to determine the routes of data transmission, ensure secure communication between nodes in the same or different networks, translate the networks and implement redundancy.
ARP
ARP stands for Address Resolution Protocol. This protocol assigns an IP address to the MAC address of the device. The MAC address is a unique address that can be used to uniquely identify a device. A device must have a MAC address to use a local area network. But the MAC address can be easily altered. Thus, an IP address is used instead of the MAC address on the internet. The IP address of a device cannot be changed.
For instance, if the NIC placed on a specific device fails, then the device's MAC address will be modified, but the device's IP address will remain the same. The address resolution protocol can be used to find the device's MAC address.
For example, if the NIC on a particular machine fails, the MAC address changes, but the IP address does not change. ARP is used to find the MAC address of the node when an internet address is known.
Note: MAC address: The MAC address is used to identify the actual device.
An IP address is used to locate a device on the network.
IGMP
IGMP is an acronym used for Internet Group Message Protocol. The internet protocol provides support for two types of communication. These are as follows:
Unicast Communication
Multicast Communication
In unicast communication, there is one sender and a single receiving node. This is a one-to-one communication, but in multicast communication, there is only one sender and numerous receiving nodes. This is a one-to-many type of communication. This protocol is implemented and used by the network's routers and hosts to support multicast communication. They use this protocol to identify the hosts available in the local network and are the members of the group. It is a component of the IP layer and has a fixed-size message. The message sent by using this protocol is encapsulated within an IP datagram.
Open Shortest Path First (OSPF)
OSPF is a link-state routing protocol. This protocol was specifically designed for IP addresses. This algorithm is based on another algorithm known as the shortest path first. The routers and the nodes in the system that are enclosed within an area maintain the same link-state database that defines the area's topology.
Routing Information Protocol (RIP)
This distance vector routing protocol computes the hop count as the metric to compute the routing distance. The hop count represents the number of routers between the source and destination nodes. The path with the east hop count is considered the best part between the network's source and destination node. It prevents routing loops by reducing the hops allowed in a path between the source and destination.
Network Address Translation (NAT)
The principle behind NAT protocol is enabling multiple devices to access the internet using a single public address. If the device requires to access the internet, then it requires a public IP address that can be used to identify the device on the internet. To make it possible, this protocol translates the private IP addresses of the devices to the required public IP address.
Internet Protocol Security (IPsec)
IPsec consists of two terms IP, which is an acronym for Internet Protocol, and sec stands for security. It is a combination of several protocols implemented at the network layer to establish encrypted connections between different nodes in the network. It ensures the security of the data transmitted in public networks. These protocols are used to establish virtual public networks (VPNs). They perform encryption on the IP packets. This uses authentication and data encryption to access the data packets in the network.
Hot Standby Router Protocol (HSRP)
It is a proprietary protocol developed by CISCO that provides redundancy for a local subset. When this protocol is implemented, one or several routers in the network acts as a virtual router. This protocol enables the user to configure two or more routers as standby routers. There is only a single router acting as the active router in the network. The rest routers only function when the active router malfunctions.
All routers placed in the same HSRP group have the same MAC and IP address. This address acts as a default gateway for the local network.
Virtual Router Redundancy Protocol (VRRP)
Redundancy means the additional links that can be used to access the network nodes. It is an open standard protocol that provides redundancy in the network. The number of routers in a group acts as virtual logical routers. These routers act as the default gateway for all the local hosts in the network. If one router fails to perform its function properly or shuts down, another router from the group is assigned the responsibility of forwarding the data traffic in the network.
The network layer infrastructure is vulnerable to cyber attacks as this layer is directly linked to the internet. The most common protocols implemented at the OSI model's network layer are Internet Protocol (IP). This layer is the most vulnerable to malicious attacks.
The attackers may launch Distributed Denial of Service attacks to create an unnecessary burden on the physical network interfaces such as routers. This may create several issues with data transmission between the networks.
Although this comparison can be misleading, the OSI network layer is often referenced as the equivalent of the Internet layer of the TCP/IP model. However, there are several differences between the two, and the TCP/IP Internet layer only has a limited amount of the functions covered by the OSI network layer.
Forwarding & Routing
The network layer in the OSI model uses the router to forward the data packets in the network. Each router in the network has its forwarding table. The router checks the packets header field to forward the data packet further into the network. The header field value is used to index in the forwarding table.
The value stored in the forwarding table associated with the field of the header value determines the outgoing interface link of the router to which the packet will be forwarded in the network.
For example: if the router has a field value of 0111 approaches at a router, then the router will use the header value to determine the index in the forwarding table. The output link interface is 2. then the router will transmit the data packet to interface 2. the routing algorithm will determine the values used as the index in the forwarding table. This table can either be centralized, which is used by all the routers in the network or decentralized, that is, each router in the network will create a forwarding table of its own.


