Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Voice over Internet Protocol (VoIP)
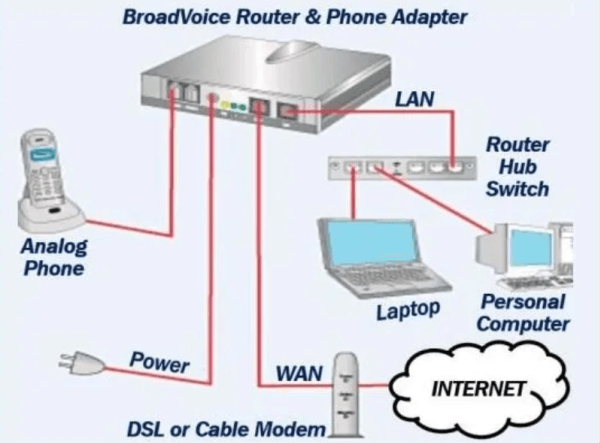
Voice over Internet Protocol (VoIP) is a technology that allows you to make voice calls using a broadband Internet connection rather than an analogue (traditional) phone line. Some VoIP services allow you to call multiple people at the same time, while others may allow you to call anyone. They can have or not have a phone number, which includes local, long-distance, mobile, and international numbers. Some VoIP services require you to use your computer or a special VoIP phone, whereas others allow you to use a regular phone connected to a VoIP adapter.
How VoIP / Internet Voice Works -
VoIP services that travel over the Internet convert voice into a digital signal. When a regular phone number is dialled, the signal is converted to a regular telephone signal, i.e. an analogue signal, before reaching its destination. VoIP allows you to make a call directly from a computer equipped with a VoIP phone or from a traditional phone connected to a special adapter. Wireless hot spots in places like airports, hospitals, and cafes allow you to connect to the Internet and use VoIP services wirelessly.
Required Equipment -
A high-speed Internet connection, such as a cable modem or high-speed services such as a local area network, is required. It is necessary to have a computer, adaptor, or specialised phone. Some VoIP services are only available through your computer or a special VoIP phone. Other services enable you to use a traditional phone in conjunction with a VoIP adapter. Some software and an inexpensive microphone are required if you use your computer. VoIP phones connect to your broadband connection and function similarly to traditional phones. If you use a VoIP adapter on your phone, you can dial as usual, and the service provider may also provide a dial tone.
VoIP vs. Landline Phones: Calling Requirements
Your landline phones are plugged into a phone jack when using an analogue phone system. Calls are placed over the public switched telephone network, and sound is transmitted via electrical pulses sent through copper wires.
If your company still uses landlines, you probably have a Private Branch Exchange (PBX) system installed on-site. You don't need multiple phone lines when using a PBX because your phone provider will set up an internal phone network that effectively connects your employees on a shared phone system.
When using a VoIP phone system, call information is transmitted online. You can make phone calls using your current internet connection. It is not necessary for your employees to be calling from a landline phone plugged into an electrical outlet and connected to trenched and laid wires in order to make and receive phone calls; they can do so from anywhere they have access to the internet.
Additionally, internet-based phone systems are more dependable. Voice data is sent more quickly during calls because it uses the internet. Long-distance calls also don't come with any concerns about call quality issues or additional costs. Additionally, since your provider is in charge of managing and maintaining the hardware, software, and network, you won't need internal IT resources to make sure your phone system runs smoothly.
desktop VoIP phones
VoIP phones are built to transmit calls using IP technologies. Despite having all the same features as a business phone, such as conference calling, do not disturb, and call waiting, they are wireless phones that don't require an outlet connection like a landline phone would.
If they perform remote work, your employees can use these phones both at the office and at home. They require no lengthy setup procedures, so you can use them right away.
Calling Headsets
A headset is an additional piece of VoIP equipment that is optional. Employees can converse comfortably without holding up a phone or using their computer's audio if they have a headset.
Do VoIP Calls Require a Special Modem or Router?
No, you don't need to buy a new modem or router for your company. You can make and receive calls from your device once your VoIP application has been downloaded there. However, if the internet connection for your company isn't strong enough, you might want to think about upgrading to make sure you have enough bandwidth.
Can Your Regular Phone Make VoIP Calls?
You can continue to use your current on-site business phone system while taking advantage of the flexibility, call quality, and cost savings provided by internet-based calls with SIP Trunking. Businesses that use SIP Trunking to update their phone system can reduce costs by up to 50%.
Calls are routed using this technology over the internet rather than traditional copper wires. You won't need to deal with a conventional phone company as a result. You won't require any additional hardware if your phone system is SIP Trunking compatible. If your phone system is more than ten years old, you might require a VoIP Gateway, a special gadget that converts analogue and digital calls into VoIP calls.
Benefits of VoIP -
- Some VoIP services provide features and services that are not available with a traditional phone or are only available for a fee.
- It is possible to avoid paying for both a broadband connection and a traditional phone line.
- A smoother connection than an analogue signal is possible.
VoIP Disadvantages -
- Some VoIP services do not function during power outages, and the service provider may or may not provide backup power.
- Not all VoIP services connect to emergency services directly via emergency service numbers.
- VoIP service providers may or may not provide directory assistance.


