Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
What is Network Function Virtualization?
Network functions virtualization (NFV) is an approach to network architecture that involves replacing dedicated network hardware devices with software-based virtualized network functions (VNFs) that run on standard servers, storage, and switches.
In traditional networking, specialized hardware devices such as routers, firewalls, and load balancers are used to perform specific network functions. With NFV, these functions are virtualized and can be run as software on commodity hardware, leading to greater flexibility, scalability, and cost-effectiveness.
NFV enables network operators to quickly and easily deploy and scale network functions as needed, without the need for physical hardware installation or maintenance. By virtualizing network functions, operators can also reduce their capital and operational expenditures, and increase their network agility, flexibility, and scalability.
NFV is often used in conjunction with software-defined networking (SDN), another approach to network architecture that separates the control plane and data plane of the network, allowing for centralized network management and orchestration. Together, NFV and SDN enable network operators to build more agile and efficient networks that can adapt to changing business and user requirements.
History of Network Function Virtualization (NFV)
The concept of network functions virtualization (NFV) emerged in 2012, when a group of leading telecommunications service providers, including AT&T, Deutsche Telekom, and NTT Docomo, formed the NFV Industry Specification Group (ISG) under the auspices of the European Telecommunications Standards Institute (ETSI).
The goal of the NFV ISG was to develop a framework for virtualizing network functions and deploying them on industry-standard servers, storage, and switches, with the aim of improving network agility, flexibility, and cost-effectiveness. The NFV ISG released its first set of specifications in 2013, defining the requirements and architecture for virtualized network functions.
Since then, NFV has gained widespread adoption across the telecommunications industry, with many service providers and vendors developing and deploying NFV solutions. In 2015, the ETSI released a second set of NFV specifications, expanding on the original framework and addressing topics such as security, management and orchestration, and network slicing.
Today, NFV is considered a key enabler of the emerging 5G network architecture, providing a flexible and efficient way to deploy and manage the wide range of network functions and services needed to support the diverse use cases and applications of 5G.
In addition to the ETSI NFV ISG, other industry groups and organizations have developed standards and best practices for NFV, including the Open Network Automation Platform (ONAP), the Open Platform for NFV (OPNFV), and the Linux Foundation Networking (LFN) project, among others.
How does network functions virtualization work?
Network functions virtualization (NFV) works by virtualizing network functions that were traditionally performed by specialized hardware devices, such as routers, switches, firewalls, and load balancers. These network functions are abstracted from their underlying hardware and implemented as software-based virtual network functions (VNFs) that run on standard servers, storage, and switches.
NFV is typically implemented using a virtualization layer that allows multiple VNFs to run on the same physical infrastructure. This virtualization layer provides isolation between the VNFs, enabling them to run independently of each other, and also provides resource management and allocation, ensuring that each VNF gets the resources it needs to operate effectively.
Components of NVF architecture:
The NFV architecture typically includes the following components:
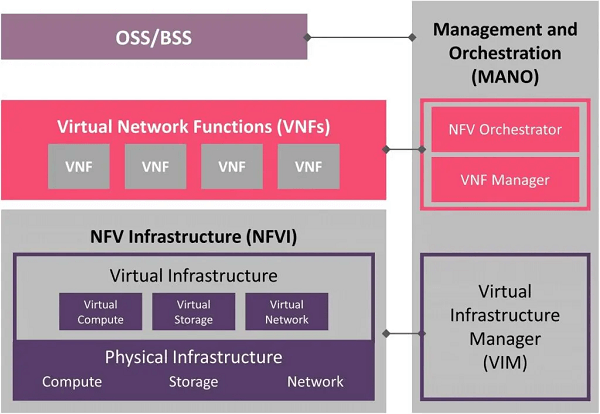
- Virtualization layer: This layer provides the virtualization environment that enables multiple VNFs to run on the same physical infrastructure. It includes a hypervisor or container-based virtualization platform that provides isolation, resource allocation, and management for the VNFs.
- Virtual network functions (VNFs): These are the software-based network functions that perform specific network tasks, such as routing, switching, firewalling, load balancing, and encryption. The VNFs are typically deployed as virtual machines or containers and run on the virtualization layer.
- NFV infrastructure (NFVI): This is the physical infrastructure that provides the computing, storage, and networking resources needed to support the VNFs. The NFVI can be located in the data centre, at the network edge, or in the cloud.
- Management and orchestration (MANO): This component provides the management and orchestration functions needed to deploy, monitor, and manage the VNFs running on the NFVI. It includes functions such as service orchestration, resource allocation, fault management, and performance management.
Overall, NFV enables organizations to deploy network functions more quickly and cost-effectively while also providing greater flexibility, scalability, and agility. By virtualizing network functions, operators can create a more dynamic and efficient network architecture that can adapt to changing business and user requirements.
Benefits of Network Function Virtualization:
There are several benefits to using Network Function Virtualization (NFV) in modern network architectures. Here are a few key reasons why organizations may choose to adopt NFV:
- Cost savings: NFV can help organizations reduce costs by replacing dedicated hardware devices with software-based virtualized network functions running on commodity hardware. This can help to reduce capital expenditures and operational costs associated with purchasing, deploying, and maintaining specialized hardware.
- Agility and flexibility: NFV enables network operators to quickly and easily deploy and scale network functions as needed, without the need for physical hardware installation or maintenance. This can help to reduce the time to market for new services and applications, and improve the agility and flexibility of the network.
- Scalability: NFV can help to improve network scalability by enabling organizations to scale up or down the capacity of virtualized network functions as needed, based on changing traffic patterns and demand.
- Enhanced network security: NFV can help to improve network security by enabling the deployment of virtualized network functions that can detect and mitigate security threats, such as firewalls, intrusion detection systems, and encryption services.
- Service innovation: NFV can enable organizations to innovate and introduce new network services and applications more quickly and easily since the virtualized network functions can be easily deployed and scaled as needed.
Overall, NFV provides a flexible, scalable, and cost-effective approach to network architecture, allowing organizations to build more agile, efficient, and innovative networks that can adapt to changing business and user requirements.
Risk of Network Function Virtualization
While there are many benefits to network functions virtualization (NFV), organizations should consider some risks and challenges before implementing NFV. Here are a few potential risks of NFV:
- Complexity: NFV can add complexity to network architecture, as it involves deploying and managing multiple virtualized network functions on a shared physical infrastructure. This can make troubleshooting issues more challenging and ensure overall network performance.
- Security: NFV introduces new security risks, as virtualized network functions may be vulnerable to attacks that exploit vulnerabilities in the virtualization software or the underlying hardware infrastructure. Proper security measures must be put in place to mitigate these risks.
- Integration with legacy systems: Integrating NFV with existing legacy systems and network architectures can be challenging and may require additional investment in new hardware and software to enable compatibility.
- Performance and reliability: The performance and reliability of NFV may be impacted by the virtualization layer and the underlying hardware infrastructure. Organizations must ensure that they have the right resources in place to support the VNFs and to deliver the desired performance and reliability.
- Vendor lock-in: Organizations that adopt NFV may become locked into a particular vendor or technology, which can limit their flexibility and ability to switch vendors or technologies in the future.
Overall, while NFV can offer significant benefits in terms of cost savings, agility, and flexibility, organizations should carefully consider the potential risks and challenges before implementing this technology in their networks. They should also ensure that they have the right expertise, tools, and processes in place to successfully deploy, manage, and secure their NFV environments.


