Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Advantages and Disadvantages of Mesh Topology
Mesh Topology
Topology describes the orientation of the nodes in the network. Mesh topology is also a type of physical network topology. In this topology, all the nodes of the network are interlinked with each other. The connections between these nodes are established randomly. These nodes can be desktops, laptops, switches, hubs, or any other device that can be connected to the network.
The primary advantage of using mesh topology is that even when a node fails, the network does not fail. It means that other nodes can effectively perform communication using the network. This network topology is quite expensive to set up. Moreover, the network nodes have no hierarchy, interdependency, or uniform pattern. It is a complex network and comparatively more difficult to establish than the other alternatives available.
All the nodes in the mesh topology can send their signals into the network. Each node is also responsible for relaying the signals from other nodes. Wireless and wired networks support this topology, mostly used for wireless nodes. It is because the cables are quite expensive. Each node is connected to every other node, which means there is a point-to-point connection between each node in the mesh topology of the network.
Given below is an illustration of the mesh topology in the network.
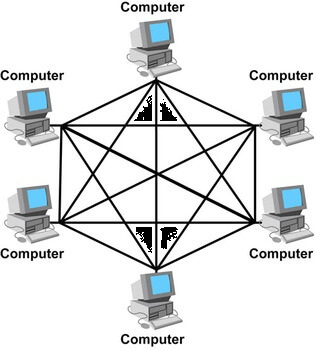
Features of Mesh Topology
In this topology, all nodes act as the router in the network. This means each node determines the route to which the data transmission will occur. This is determined based on the available connection in the nodes.
If there is a break in the network cable, the data traffic passing through the particular cable is redistributed among the nodes. It ensures that the network is always available for all the nodes in the network.
This topology offers redundancy in the network.It is a type of network topology that offers redundant links across the network, but it is rarely used due to the work involved in having a network and the high cost, as the network components are directly connected to every other component.
Types of Mesh Topology
Depending upon the connection of different nodes in the network. The mesh topology can be distinguished between full and partial mesh topologies. Both these types of mesh topology are described below:
- Full Mesh Topology: In this mesh topology, all the nodes in the network are connected with all the other nodes in the network. Every node in this network will have n-1 connections, where n is the number of nodes. Thus, the total number of connections in the network is n(n-1). The network is usually used as a reserve for the network backbone. This provides a lot of redundancy in the network. Redundancy means several paths are available for the data to reach from a sender to a receiver. However, this topology can be quite expensive to implement. The cost of implementation is overlooked because it enables the user to use the network when a node fails. The traffic load is distributed again to other nodes in such a situation.
- Partial Mesh Topology: In this topology, all the nodes do not have a separate connection with other nodes. Only a few nodes are connected with every remaining node in the network. This means it is not necessary to connect all the devices. This reduces the codes for establishing the network. This network usually implements the peripheral network through which they work with a full mesh backbone. Though it is less redundant than the full mesh network, it provides some level of redundancy in the network.
Working on Mesh Topology
There are two principles based on which the mesh topology is implemented. These principles are as follows:
Routing
Flooding
Routing
This function determines the path of the data packet. The routing principle is implemented before transmitting the data packet in the network. The data packets are sent through a prearranged path consisting of several nodes. The data packet is sent through these nodes to reach the destination node. In order to successfully transmit the data, all the intermediary nodes and all the intermediate nodes should be active during transmission. They should be connected to the previous and next nodes in the transmission path.
Flooding
The other principle to implementing the mesh topology is known as flooding. In flooding, the data is transmitted to every active node in the network. If the data packet is addressed to the node, then the destination node will accept the packet, but if it is not addressed to the node, it is passed to the next node in the network path.
Protocols Implemented in Mesh Topology
The protocols necessary to implement the mesh topology are present in the three layers of the OSI model. These protocols define the standards required to communicate between two nodes. The protocols can be defined as the set of rules that must be implemented to facilitate communication between devices.
The three protocols used to implement mesh topology are as follows:
Proactive Protocol
Hybrid Protocol
Reactive Protocol
Each of the protocols mentioned above plays a crucial role in implementing the network through its features and increases the performance and scalability of the network.
- Proactive Protocol:The function of this protocol is to provide self-monitoring for the nodes in the network. It is done by taking feedback from the nodes in the network. If a node fails in the network, it is responsible for initiating the path rerouting and avoiding the particular node. This protocol improves the performance of the network as it maximizes the uptime of the network. It recovers the network after failure and provides robust performance. When implemented in a dynamic environment then, this protocol uses more resources and there is a possibility of collision. But when implemented in the static environment, the protocols work ideally. It is because the path of the network is not usually altered in a static environment. Therefore, the user should ensure the protocol is implemented in a suitable environment for optimal performance.
- Hybrid Protocol: this protocol provides the best option depending on the environment and communication requirements. This protocol uses reactive methods along with the features of the proactive protocol. This can reduce the cost of network operations by implementing the hybrid protocol.
- Reactive Protocol: This protocol decides the network path for the data packets sent from the source to the destination node. This operation is performed at the time when the node request for data transmission in the network. The function of this protocol includes ensuring that the path selected is the most optimal. It scans the entire network of nodes to find all the possible paths to transfer the data packets from one node to another. Since this protocol is more scalable than other protocols used to implement mesh topology, it is more suited for implementation in a dynamic environment.
Advantages and Disadvantages of Mesh Topology
Mesh topology is established by interconnecting the devices in the network. If any connection between the nodes fails, then the traffic in the connection is redistributed to ensure that the data is transmitted to the destined nodes. This is the best way to implement the primary connections of the network as it eliminates the concerns regarding any node or connection failure. Wireless connections implemented these days are an example of mesh topology.
Advantages of Mesh Topology
There are several benefits of establishing a network in a mesh topology. Some of these advantages are as follows:
- Handle a High Level of Data Traffic: this topology does not have a hierarchy. This means that if any node in the network tries to connect with another node, it can directly benefit from the routing ability of the node. This is possible because there is no hierarchy in the mesh topology.
- Node or Connection Failure Does Not Affect the Network: Mesh topology is more resistant to network failure than any other topology. The data packets are transmitted to all the nodes in the network. Each node has its routing table and translates the information mentioned in the data packet. The nodes are interconnected with all the other nodes in the network. There is redundancy in the network. Therefore even when a node or connection between two nodes fails or malfunctions, the traffic of the particular node or connection is redistributed in the network.
- Consistent Data Transfer: since there are several paths connecting two nodes in the network. In a mesh topology, the primary requirement is to connect a node with all other nodes in the network. The network constructs several paths two connect two nodes in the network. Therefore the overall data transmitted over the network is always consistent in the network. If there is more traffic in a particular path, the data can be redirected to other paths in the network. Even when some nodes in the network malfunction, the network can choose another pathway to transmit the data.
- Easy To Add New Nodes In the Network: Adding new devices to the network is easy. Mesh topology allows the user to add new devices to the network without disturbing the existing network. This means when the user introduces a new node to the network, the data currently being transmitted is not disrupted. Moreover, since all the nodes are connected, removing a node also does not affect or disrupt the flow of the existing network.
- Easily Scalable: No additional equipment is required to connect nodes in the mesh topology. Each node acts as the router in the network by developing its routing table. The nodes transmit the data to all the connecting nodes to determine the possible pathways to other nodes in the network. This allows the user to change the network size easily. The user can add not only new nodes but also add new technology in the network. The addition can be made without affecting the current speed of operation.
- Easy to Implement Mesh Topology: Implementing the mesh topology in the network is easy without any trouble. The user is only required to connect the nodes with the gateway in the network so that the data packets can be transmitted through the remaining network for it to implement the mesh topology. It allows the network to self-optimize by selecting the nest pathway to transmit the data between nodes.
- Difficult to Take Down the Whole Network: Since there is no primary component in the network and each node acts as the router, it is almost impossible to bring down the whole network. There is no central equipment, and it has several redundant connections. Therefore, making it difficult to take down the entire network. It is only possible when there is a global disaster if all the nodes are attacked.
- No Central Component is Required: The user does not need to include a central component to transmit or receive the data in the network. This is beneficial as the user does not have to invest in expensive central equipment. The network does not require additional room. Moreover, it provides an individual-based secure method of data transmission in the network. The user can also remain anonymous during transmission. Since there are the private connection between each node. It eliminated the requirement for additional firewalls and software that provide security in the network.
- Flexibility:In Mesh Topology, a partial shortfall option provides great flexibility. Therefore the user is not required to complete all the connections for each node in the network; that is, the user can implement partial mesh topology. The partial mesh topology saves the cost of cables and provides enhanced communication benefits.
- Handle Large Volume of Data: Mesh topology can manage a large volume of data transmitted in the network. It is more efficient than all traditional systems as it can connect multiple nodes in the network. Multiple paths connecting different nodes in the network allow the user to transmit the data simultaneously between different nodes.
Disadvantages of Mesh Topology
There are several advantages of using mesh topology to establish a network, but there are limitations to using this topology. Some of the disadvantages of mesh topology are as follows:
- High Cost to Set up:The cost of setting up Mesh topology is higher than alternative topologies because it requires cables and other equipment that are quite expensive. In order to implement the mesh topology in the network, it is necessary to ensure that there is suitable hardware, cabling, and network bandwidth, making it suitable for data transmission.
- Takes Time to Setup and Perform Maintenance: The user must establish multiple connections for each node in the network. Though adding new nodes in an already established network is simple, the initial step to set up a network is complex and expensive.
- High Possibility of Redundant Connections:Since multiple connections exist between each node of the network, there is a high possibility of unnecessary, redundant connections in the network. Some of these connections may not be used in the network until an existing connection fails.
- More Load on Each Node:There is no central equipment to manage the data transmission path within different nodes. The nodes are required to act as the router in the networks. The nodes must create their routing table, adding more responsibility to the node. It increases the complexity of the system.
- Latency Issues:These issues are generally faced by low-power mesh topology. There is not enough processing power to handle the data simultaneously transmitted by the different nodes in the network promptly.


