Tutorial
Physical Layer
Data Link layer
Network Layer
Routing Algorithm
Transport Layer
Application Layer
Network Security
Misc
- Router
- OSI vs TCP/IP
- TCP vs UDP
- Transmission Control Protocol
- TCP port
- IPv4 vs IPv6
- ARP Packet Format
- ARP Table
- Working of ARP
- FTP Client
- FTP Commands
- FTP Server
- I2C Protocol
- Sliding Window Protocol
- SPI Protocol
- IP
- ARP Commands
- ARP
- Address Resolution Protocol
- ARP and its types
- TCP Retransmission
- CAN protocol
- HTTP Status Codes
- HTTP vs HTTPS
- RIP Protocol
- UDP Protocol
- ICMP Protocol
- MQTT protocol
- OSPF Protocol
- Stop and Wait Protocol
- IMAP Protocol
- POP Protocol
- CIFS
- DAS
- DIMM
- iSCSI
- NAS (Network Attached Storage)
- NFS
- NVMe
- SAN
- Border Gateway Protocol
- Go-Back-N ARQ
- RJ Cable
- Difference between Connection-Oriented and Connectionless Service
- CDMA vs. GSM
- What is MAC Address
- Modem vs. Router
- Switch Vs. Router
- USB 2.0 vs 3.0
- Difference between CSMA CA and CSMA CD
- Multiple access protocol- ALOHA, CSMA, CSMA/CA and CSMA/CD
- URI vs URL
- IMAP vs. POP3
- SSH Meaning| SSH Protocol
- UTP vs STP
- Status Code 400
- MIME Protocol
- IP address
- proxy server
- How to set up and use a proxy server
- network security
- WWW is based on which model
- Proxy Server List
- Fundamentals of Computer Networking
- IP Address Format and Table
- Bus topology and Ring topology
- Bus topology and Star topology
- Circuit Switching and Packet switching?
- Difference between star and ring topology
- Difference between Router and Bridge
- TCP Connection Termination
- Image Steganography
- Network Neutrality
- Onion Routing
- Adaptive security appliance (ASA) features
- Relabel-to-front Algorithm
- Types of Server Virtualization in Computer Network
- Access Lists (ACL)
- What is a proxy server and how does it work
- Digital Subscriber Line (DSL)
- Operating system based Virtualization
- Context based Access Control (CBAC)
- Cristian's Algorithm
- Service Set Identifier (SSID)
- Voice over Internet Protocol (VoIP)
- Challenge Response Authentication Mechanism (CRAM)
- Extended Access List
- Li-fi vs. Wi-fi
- Reflexive Access List
- Synchronous Optical Network (SONET)
- Wifi protected access (WPA)
- Wifi Protected Setup (WPS)
- Standard Access List
- Time Access List
- What is 3D Internet
- 4G Mobile Communication Technology
- Types of Wireless Transmission Media
- Best Computer Networking Courses
- Data Representation
- Network Criteria
- Classful vs Classless addressing
- Difference between BOOTP and RARP in Computer Networking
- What is AGP (Accelerated Graphics Port)
- Advantages and Disadvantages of Satellite Communication
- External IP Address
- Asynchronous Transfer Mode (ATM)
- Types of Authentication Protocols
- What is a CISCO Packet Tracer
- BOOTP work
- Subnetting in Computer Networks
- Mesh Topology Advantages and Disadvantages
- Ring Topology Advantages and Disadvantages
- Star Topology Advantages and Disadvantages
- Tree Topology Advantages and Disadvantages
- Zigbee Technology-The smart home protocol
- Network Layer in OSI Model
- Physical Layer in OSI Model
- Data Link Layer in OSI Model
- Internet explorer shortcut keys
- Network Layer Security | SSL Protocols
- Presentation Layer in OSI Model
- Session Layer in OSI Model
- SUBNET MASK
- Transport Layer Security | Secure Socket Layer (SSL) and SSL Architecture
- Functions, Advantages and Disadvantages of Network Layer
- Protocols in Noiseless and Noisy Channel
- Advantages and Disadvantages of Mesh Topology
- Cloud Networking - Managing and Optimizing Cloud-Based Networks
- Collision Domain and Broadcast Domain
- Count to Infinity Problem in Distance Vector Routing
- Difference Between Go-Back-N and Selective Repeat Protocol
- Difference between Stop and Wait, GoBackN, and Selective Repeat
- Network Function Virtualization (NFV): transforming Network Architecture with Virtualized Functions
- Network-Layer Security | IPSec Modes
- Next - Prev Network-Layer Security | IPSec Protocols and Services
- Ping vs Traceroute
- Software Defined Networking (SDN): Benefits and Challenges of Network Virtualization
- Software Defined Networking (SDN) vs. Network Function Virtualization (NFV)
- Virtual Circuits vs Datagram Networks
- BlueSmack Attack in Wireless Networks
- Bluesnarfing Attack in Wireless Networks
- Direct Sequence Spread Spectrum
- Warchalking in Wireless Networks
- WEP (Wired Equivalent Privacy)
- Wireless security encryption
- Wireless Security in an Enterprise
- Quantum Networking
- Network Automation
- Difference between MSS and MTU
- What is MTU
- Mesh Networks: A decentralized and Self-Organizing Approach to Networking
- What is Autonomous System
- What is MSS
- Cyber security & Software security
- Information security & Network security.
- Security Engineer & Security Architect
- Protection Methods for Network Security
- Trusted Systems in Network Security
- What are Authentication Tokens in Network security
- Cookies in Network Security
- Intruders in Network Security
- Network Security Toolkit (NST) in virtual box
- Pivoting-Moving Inside a Network
- Security Environment in Computer Networks
- Voice Biometric technique in Network Security
- Advantages and Disadvantages of Conventional Testing
- Difference between Kerberos and LDAP
- Cyber security and Information Security
- GraphQL Attacks and Security
- Application Layer in OSI Model
- Applications of Remote Sensing
- Seven Layers of IT Security
- What is Ad Hoc TCP
- What is Server Name Indication(SNI)
Network Automation
Introduction to Network Automation
Network automation refers to the use of technology to automate and streamline the management and operation of computer networks. In traditional network management, network administrators would have to manually configure network devices such as routers, switches, and firewalls. This process was time-consuming, error-prone, and required a lot of manual effort.
With network automation, however, these tasks can be automated using tools and software. This allows for faster deployment times, increased reliability, and improved efficiency. Network automation can also reduce the risk of human error, minimize downtime, and enable IT teams to focus on more strategic initiatives.
As technology continues to evolve, the need for network automation is becoming increasingly critical. In today's digital age, organizations deal with larger and more complex networks, requiring more advanced management techniques. By implementing network automation, businesses can stay ahead of the curve and remain competitive in their respective industries.
The Benefits of Network Automation
Network automation provides several benefits for organizations. Some of these benefits include:
- Improved Efficiency: By automating routine network management tasks, network administrators can focus on more strategic initiatives. This can lead to more efficient use of time and resources, resulting in increased productivity and reduced costs.
- Faster Deployment Times: Network automation allows for more rapid deployment times, as new devices can be easily added to the network and configured automatically. This can help organizations respond to changing business needs more quickly.
- Increased Reliability: Network automation reduces the risk of human error, which can lead to network downtime and other issues. By automating network tasks, organizations can improve the reliability and stability of their networks.
- Enhanced Security: Network automation can improve security by automating tasks such as software updates, patch management, and access control. This can reduce the risk of security breaches and other cyber-attacks.
- Consistency: With network automation, network configurations can be applied consistently across all devices in the network. This ensures that the network is always in a known and predictable state.
- Scalability: Network automation can help organizations scale their networks more easily, as automation tools can be used to deploy and manage large numbers of devices.
Network automation can help organizations operate more efficiently and effectively while reducing the risk of downtime, errors, and security breaches.
Types of Network Automation
There are several types of network automation, each of which serves a specific purpose. These types include:
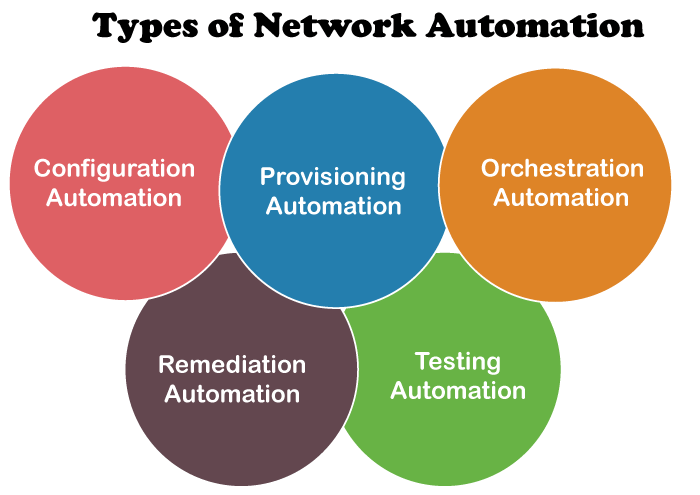
- Configuration Automation: Configuration automation refers to the automation of configuration changes to network devices such as routers, switches, and firewalls. Configuration automation tools can automatically deploy, configure, and manage network devices, saving time and reducing the risk of errors.
- Provisioning Automation: Provisioning automation involves the automation of the process of adding new devices to a network. With provisioning automation, new devices can be quickly and easily added to the network, with all necessary configurations and settings applied automatically.
- Orchestration Automation: Orchestration automation involves the automation of complex workflows that involve multiple devices and systems. With orchestration automation, complex network tasks such as deploying an application across multiple servers can be automated, streamlining the process and reducing the risk of errors.
- Remediation Automation: Remediation automation involves the automatic detection and resolution of network issues. With remediation automation, network issues can be identified and resolved automatically, reducing the risk of downtime and other issues.
- Testing Automation: Testing automation involves the automation of network testing and validation. With testing automation, network administrators can quickly and easily test new configurations and changes to the network, ensuring that they are working as intended.
The different types of network automation can help organizations streamline their network operations and improve efficiency while reducing the risk of errors and downtime.
How Network Automation Works
Network automation involves using technology to automate network tasks previously performed manually by network administrators. The automation process can be broken down into several steps:
- Gathering Information: The first step in network automation is to gather information about the network devices and their configurations. This information is typically collected using network discovery tools or network management systems.
- Creating Scripts or Templates: Once the necessary information has been collected, network administrators can create scripts or templates that define the desired configuration of the network devices.
- Deploying the Automation Tool: The automation tool, such as Ansible or Puppet, is then deployed to the network devices. This tool is responsible for applying the configuration changes defined in the scripts or templates.
- Monitoring the Network: After the automation tool has been deployed, network administrators can monitor the network to ensure that the configuration changes have been applied correctly and that the network is functioning as intended.
- Troubleshooting and Remediation: If any issues are identified during the monitoring process, the automation tool can automatically detect and remediate the issues.
In essence, network automation works by using software to automate network device configuration, management, and monitoring. By automating these tasks, organizations can reduce the risk of human error, improve network efficiency, and enhance network security.
Use Cases of Network Automation
Network automation has a wide range of use cases, as it can be used to automate a variety of network tasks. Some of the most common use cases of network automation include:
- Configuration Management: Network automation can manage and automate network device configurations such as routers, switches, and firewalls. This can help ensure that network configurations are consistent across all devices and reduce the risk of errors.
- Provisioning: Network automation can be used to automate the provisioning of new network devices, such as routers and switches. This can help organizations deploy new devices more quickly and efficiently.
- Network Monitoring and Troubleshooting: Network automation can be used to automate the monitoring and troubleshooting of network devices. This can help organizations detect and resolve issues more quickly and reduce the risk of downtime.
- Security Management: Network automation can be used to automate security tasks such as patch management, access control, and software updates. This can help organizations improve network security and reduce the risk of security breaches.
- Compliance Management: Network automation can be used to automate compliance tasks such as regulatory reporting and audit preparation. This can help organizations ensure that they are meeting all regulatory requirements.
- Network Optimization: Network automation can be used to optimize network performance by automating tasks such as load balancing, traffic shaping, and bandwidth management.
Overall, the use cases for network automation are diverse and can help organizations improve network efficiency, reliability, and security. By automating routine network tasks, network administrators can focus on more strategic initiatives, enabling organizations to stay competitive in their respective industries.
Best Practices for Network Automation
Here are some best practices for network automation:
- Start Small: Begin with automating a single network task or process before scaling up to more complex tasks. This will help you identify any issues and fine-tune your automation process.
- Define Your Goals: Clearly define your automation goals and objectives, and ensure that they align with your overall business objectives. This will help you stay focused on your goal with network automation.
- Standardize Network Configurations: Ensure all network devices are configured using standardized templates and scripts to reduce the risk of errors and ensure consistency.
- Use Version Control: Use version control systems to manage your network automation scripts and templates. This will help you keep track of changes and revert to previous versions if necessary.
- Test Thoroughly: Before deploying any automation changes to your network, thoroughly test them in a non-production environment to ensure that they work as intended and do not have any unintended consequences.
- Monitor Network Performance: Continuously monitor network performance after deploying automation changes to ensure they do not negatively impact network performance.
- Invest in Training: Invest in training for your network administrators to ensure that they have the necessary skills to manage and maintain the automated network.
- Regularly Review and Update Your Automation Processes: Regularly review and update your automation processes to ensure that they align with your business objectives and meet your needs.
Following these best practices can help you achieve successful network automation and ensure that it delivers the desired benefits for your organization.
Challenges of Network Automation
Network automation offers many benefits, but it also presents some challenges. Here are some of the common challenges of network automation:
- Complexity: Network automation requires a deep understanding of network protocols, operating systems, and software tools. This can be challenging for network administrators who may not have the necessary expertise or experience.
- Integration: Integrating different network automation tools with existing network infrastructure can be challenging. It can require significant time and effort to ensure that all tools work together seamlessly.
- Security: Network automation can introduce security risks if not properly implemented. Automated scripts can potentially be used to perform malicious activities such as network reconnaissance or data exfiltration.
- Maintenance: Automated scripts and templates must be maintained to ensure they continue to work correctly. Maintenance can be time-consuming and requires regular updates to keep up with changes in the network environment.
- Cost: Network automation can require significant software and infrastructure investment. This can be a barrier for some organizations, especially small and medium-sized businesses.
- Resistance to Change: Some network administrators may be resistant to network automation due to concerns about job security or a lack of understanding of the benefits of automation.
Network automation can be challenging, but these challenges can be mitigated by proper planning, training, and implementation. By carefully considering the benefits and challenges of network automation, organizations can determine whether automation is right for their network environment and take steps to implement it effectively.
Future of Network Automation
The future of network automation looks promising, with the continued growth of new technologies and the increasing demand for faster and more efficient network operations. Here are some key trends and developments that are shaping the future of network automation:
- Artificial Intelligence and Machine Learning: Advances in AI and machine learning are enabling network automation tools to become more intelligent and adaptive, allowing them to respond to network issues in real-time.
- Intent-Based Networking: Intent-based networking (IBN) is a new approach to network automation that uses machine learning and natural language processing to understand the intent behind network operations. IBN aims to simplify network operations and make it easier for network administrators to manage complex networks.
- Cloud-Based Network Automation: Cloud-based network automation tools are becoming more popular, offering greater scalability, flexibility, and cost savings. Cloud-based tools also enable network administrators to automate tasks across multiple network environments.
- Software-Defined Networking (SDN): SDN is a network architecture that separates the network control plane from the data plane, allowing for greater programmability and automation. SDN is becoming more widespread, enabling network administrators to manage networks more efficiently and automate network tasks.
- DevOps Integration: DevOps practices are being integrated into network automation, allowing for greater collaboration between development and operations teams. This integration is helping organizations to streamline network operations and improve overall efficiency.
The future of network automation is bright, with new technologies and developments enabling network administrators to automate more tasks and operate networks more efficiently. As network automation becomes more widespread, it will become increasingly important for network administrators to develop the necessary skills and expertise to manage and maintain automated networks.
CONCLUSION
One may conclude that network automation is a rapidly evolving field that offers numerous benefits to organizations. By automating routine network tasks and processes, organizations can improve network efficiency, reduce errors, and free up network administrators to focus on higher-value tasks. There are many types of network automation tools and technologies available, including scripts, APIs, orchestration, and SDN. However, network automation also presents several challenges, such as complexity, integration, security, maintenance, cost, and resistance to change. To successfully implement network automation, organizations need to carefully plan and prepare for the transition, invest in training and development, and follow best practices such as starting small, defining goals, standardizing configurations, testing thoroughly, monitoring performance, and regularly reviewing and updating automation processes. Looking to the future, network automation will continue to be a critical area of focus for organizations as they seek to improve network operations and respond to changing business needs.


