COA Tutorial
Basic CO and Design
Computer Instructions
Digital Logic Circuits
Map Simplification
Combinational Circuits
Flip - Flops
Digital Components
Register Transfer
Micro-Operations
Memory Organization
COA_Misc
- Booth's Multiplication Algorithm
- Branch Instruction in Computer Organization
- Data Representation in Computer Organization
- ALU and Data Path in Computer Organization
- External memory in Computer Organization
- Structured Computer Organization
- Types of Register in Computer Organization
- Secondary Storage Devices in Computer Organization
- Types of Operands in Computer Organization
- Serial Communication in Computer organization
- Addressing Sequencing in Computer Organization
- Simplified Instructional Computer (SIC)
- Arithmetic Instructions in AVR microcontroller
- Conventional Computing VS Quantum Computing
- Instruction set used in Simplified Instructional Computer
- Branch Instruction in AVR microcontroller
- Conditional Branch instruction in AVR Microcontroller
- Data transfer instruction in AVR microcontroller
- Difference between Memory-based and Register-based addressing modes
- Difference between 1's complement Representation and 2's complement Representation
- CALL Instructions and Stack in AVR Microcontroller
- Difference between Call and Jump Instructions
- Overflow in Arithmetic Addition in Binary number System
- Horizontal Micro-programmed Vs. Vertical Micro-programmed Control Unit
- Hardwired Vs. Micro-programmed Control Unit
- Non-Restoring Division Algorithm for Unsigned Integer
- Restoring Division Algorithm for Unsigned Integer
- Debugging a Machine-level Program
- Dependencies and Data Hazard in pipeline in Computer Organization
- Execution, Stages and Throughput in Pipeline
- Types of Pipeline Delay and Stalling
- Timing Diagram of MOV Instruction
- Advantages and Disadvantages of Flash Memory
- Importance/Need of negative feedback in amplifiers
- Anti-Aliasing - Computer Graphics
- Bus Arbitration in Computer Organization
- Convert a number from Base 2 (Binary) to Base 6
- Cache Coherence
- EHCI
- Cache Memory and Virtual Memory
- Electrical Potential and Potential Difference
- RAM and Cache
- SIM and RIM instructions in 8085 processor
- Clusters in Computer Organization
- Data Types and Addressing Modes of 80386/80386DX Microprocessor
Cache Coherence
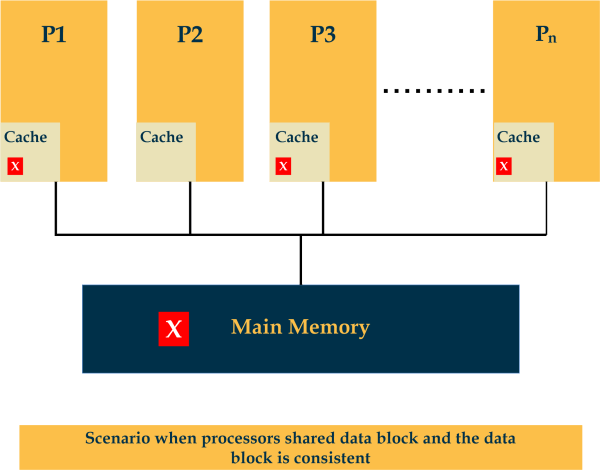
The cache coherence protocol is discussed in this article as a solution to the multicache inconsistency issues.
Cache Coherence
A cache coherence issue results from the concurrent operation of several processors and the possibility that various caches may hold different versions of the identical memory block. The practice of cache coherence makes sure that alterations in the contents of associated operands are quickly transmitted across the system.
The cache coherence problem is the issue that arises when several copies of the same data are kept at various levels of memory.
Cache coherence has three different levels:
- Each writing operation seems to happen instantly.
- Each operand's value changes are seen in every processor in precisely the same order.
- Non-coherent behavior results from many processors interpreting the same action in various ways.
Methods to resolve Cache Coherence
The two methods listed below can be used to resolve the cache coherence issue:
Hello Java Program for Beginners
- Write Through
- Write Back
Write Through
The easiest and most popular method is to write through. Every memory write operation updates the main memory. If the word is present in the cache memory at the requested address, the cache memory is also updated simultaneously with the main memory.
The benefit of this approach is that the RAM and cache always hold the same information. In systems with direct memory access transfer, this quality is crucial. It makes sure the information in the main memory is up-to-date at all times so that a device interacting over DNA can access the most recent information.
Advantage - It provides the highest level of consistency.
Disadvantage - It requires a greater number of memory access.
Write Back
Only the catch location is changed during a write operation in this approach. When the word is withdrawn from the cache, the place is flagged, so it is replicated in the main memory. The right-back approach was developed because words may be updated numerous times while they are in the cache. However, as long as they are still there, it doesn't matter whether the copy that is stored in the main memory is outdated because requests for words are fulfilled from the cache.
An accurate copy must only be transferred back to the main memory when the word is separated from the cache. According to the analytical findings, between 10% and 30% of all memory references in a normal program are written into memory.
Advantage - A very small number of memory accesses and write operations.
Disadvantage - Inconsistency may occur in this approach.
The important terms related to the data or information stored in the cache as well as in the main memory are as follows:
- Modified - The modified term signifies that the data stored in the cache and main memory are different. This means the data in the cache has been modified, and the changes need to be reflected in the main memory.
- Exclusive - The exclusive term signifies that the data is clean, i.e., the cache and the main memory hold identical data.
- Shared - Shared refers to the fact that the cache value contains the most current data copy, which is then shared across the whole cache as well as main memory.
- Owned - The owned term indicates that the block is currently held by the cache and that it has acquired ownership of it, i.e., complete privileges to that specific block.
- Invalid - When a cache block is marked as invalid, it means that it needs to be fetched from another cache or main memory.
Below is a list of the different Cache Coherence Protocols used in multiprocessor systems:
- MSI protocol (Modified, Shared, Invalid)
- MOSI protocol (Modified, Owned, Shared, Invalid)
- MESI protocol (Modified, Exclusive, Shared, Invalid)
- MOESI protocol (Modified, Owned, Exclusive, Shared, Invalid)
These protocols are discussed below:
1. MSI Protocol
This is a fundamental cache coherence mechanism that is utilized in multiprocessor systems. A cache may be in any state indicated by the protocol name's letters. Therefore, for MSI, each block may be in one of the following states:
- Modified - In other words, the data in the cache is incompatible with the main memory, and this status denotes that the block has been updated in the cache. Therefore, when the data from the cache block is removed and is in the Modified (M) state, the cache is responsible for writing the block to the main memory.
- Shared - At least one cache has at least one copy of this block, which has not been updated. The cache might be removed without writing the data to the backup store.
- Invalid - If this block is going to be stored in this cache, it must be obtained from RAM or from a different cache because it is invalid.
2. MOSI Protocol
It has one extra state than the MSI protocol, which is discussed below:
Owned - It is used to signify the ownership of the current processor to this block and will respond to inquiries if another processor wants this block.
3. MESI Protocol
The protocol for cache coherence that is utilized the most is this one. Each cache line bears a status indicating one of the following:
- Modified - As mentioned above, this term signifies that the data stored in the cache and main memory are different. This means the data in the cache has been modified, and the changes need to be reflected in the main memory.
- Exclusive - The exclusive term signifies that the data is clean, i.e., the cache and the main memory hold identical data.
- Shared - This signifies that other caches on the computer may also hold this cache line.
- Invalid - This indicates that this cache line is marked as invalid by the word "invalid."
4. MOESI Protocol
This protocol provides comprehensive cache coherence, covering all potential states that are frequently utilized in other protocols. There are one of the following statuses for each cache line:
- Modified - While the copy in main memory is inaccurate and no other processors are holding copies, a cache line in this condition contains the most recent, accurate copy of the data.
- Owned - The most current, accurate copy of the data is stored in a cache line in this state. In that other processors can store copies of the most recent, accurate data comparable to the shared state; unlike the shared state, copies in main memory can be inaccurate. One processor can only own the data at a time, and the remaining processor can have the data in the shared state.
- Exclusive - The most current, accurate copy of the data is stored on a cache line in this state. Since no other storage location has a copy of the data, the ram copy is also the most recent and accurate copy.
- Shared - The most current, accurate copy of the data is stored on a cache line in this condition. Additional system processors may also store data copies in the shared state. If no other processor has ownership of the data, the copy in primary memory also represents the most recent and accurate version of the data.
- Invalid - In this situation, a cache line doesn't contain a reliable copy of the data. Still, valid data can be found in primary memory or another processor's cache.
Types of Coherence:
There exist three varieties of coherence referred to the coherency mechanisms, which are listed below:
- Directory Based - A directory-based system keeps the coherence amongst caches by storing shared data in a single directory. In order to load an entry from primary memory into its cache, the processor must request permission through the directory, which serves as a filter. The directory either upgrades or devalues the other caches that contain that record when a record is modified.
- Snooping - Individual caches watch address lines during the snooping process to look for accesses to memory locations that they have cached. A write invalidate protocol is what it is known as. When a write activity is seen to a memory address for which a cache maintains a copy, the cache controller invalidates its own copy of the snooped memory location.
- Snarfing - A cache controller uses this approach to try and update its own copy of a memory location when a second master alters a place in the main memory by keeping an eye on both the address and the contents. The cache controller updates its own copy of the underlying memory location with the new data when a write action is detected to a place of which a cache holds a copy.


