Computer Components
Computer Memory
Computer Network
Computer Virus
Number Systems
Shortcut Keys
Terms
- What is a Browser
- Google Chrome
- Mozilla Firefox
- Internet Explorer
- Windows
- Computer Ports
- program
- Printers
- Microphone
- Monitor
- Motherboard
- Incognito Mode
- Mouse
- Memory Card
- CD
- ID
- ISO
- character
- server
- Keyboard
- Remote
- webcam
- Data
- URL
- keypad
- hub
- File
- Bytes
- Exabyte
- Gb
- Kilobyte
- Megabyte
- Petabyte
- Terabyte
- What is HDD
- What is SSD
- Memory vs Storage
- Non-volatile memory
- What is M.2 SSD
- How To Reboot A Computer
- Multi-Level Cell
- NAND Flash Memory
- What is the lock screen
- Block Storage
- Universal Serial Bus
- VRAM
- Cloud Hosting
- CompactFlash card
- What is WAP
- Classification of Memory
- Hardware vs Software
- Uses of Computer
- Uses of Internet
- Abacus
- Best Proxy Servers
- SSL VS. TLS
- Web Console
- GPU
- Difference Between LAN and WAN
- SSD and HDD
- Computer
- Data Migration
- JEDEC
- MLC vs. TLC vs. SLC NAND Flash
- VirtualBox Installation
- Num Lock
- PC
- MAC
- Continuous Data Protection
- Persistent Storage
- What is Bit
- Software Definition
- What is a File System
- When was the first computer invented
- How many generations of the computer
- Minicomputer
- Fourth Generation of Computer
- What is a Username
- What is ALU
Questions
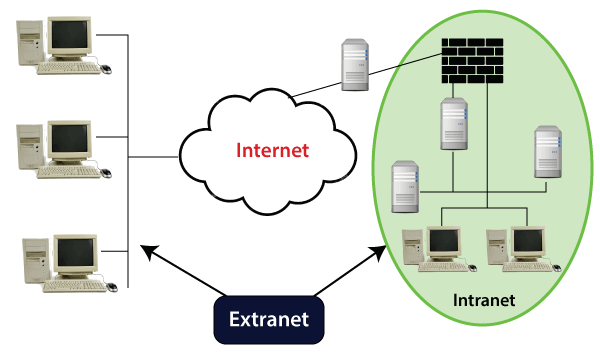
Extranet
Extranet is a part of an organization's intranet. It is a communication network that is based on internet protocols (TCP/IP). It provides controlled access to firm's intranet to its trading partners, customers, and other businesses. So, it is a private network that securely shares internal information and operations of a firm with authorized people outside the firm without giving access to the company's entire network. The users are required to have IDs, passwords, and other authentication mechanisms to access this network.
Some of the benefits of extranet:
- It acts as a single interface between the company and its trading partners.
- It automates the firm's processes like automatically places an order with suppliers when inventory drops.
- It improves customer service by providing customers a platform to resolve their queries and complaints.
- It enables the firm to share information with trading partners without engaging in paper-based publishing processes.
- It streamlines business processes that are repetitive in nature, such as ordering from a vendor on a regular basis.
How is Extranet Established?
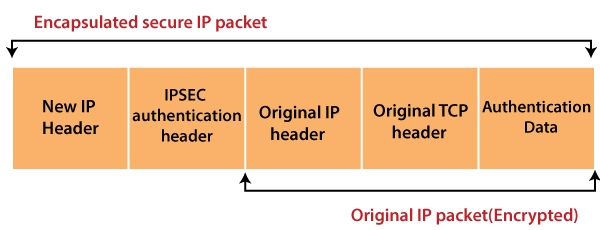
It is set up in the form of a Virtual Private Network as it is prone to security threats due to the use of the internet to connect outsiders to an organization's intranet. VPN can assure you a safe network in a public network such as the internet. The transmission control protocol (TCP) and internet protocol (IP) are used for the data transfer.
VPN assures secure transactions based on Internet Protocol Security Architecture (IPSEC) protocol as it provides an extra security layer to TCP/IP protocol, which is used for data transfer in the extranet. In this layer, the IP packet is encapsulated to form a new IP packet, as shown below:
Furthermore, to provide more security to Intranet, the following two measures are also taken by an organization:
- Firewall: It prevents unauthorized users from accessing the extranet.
- Passwords: It also prevents unauthorized users, including the company's employees from accessing the data stored on its server.
Limitations of Extranet:
- Hosting: If you host extranet pages on your own server, it requires a high bandwidth internet connection, which is may be very expensive.
- Security: You need extra firewall security if you host it on your own server. It increases the workload and makes security mechanism very complex.
- Dependency: It is dependent on the internet as outsiders cannot access information without using the internet.
- Less Interaction: It reduces the face to face interaction between customers, business partners, vendors, etc., which results in poor relationship building.
Difference between Intranet and Extranet:
| Intranet | Extranet |
|---|---|
| It is a private network, which cannot be accessed externally. | It may not be called a private network, as it can be assessed externally. It provides limited access to authorized outside-users such as vendors, partners, etc. |
| It connects the employees of the company. | It connects the company's employees with partners. |
| It is an independent network, not a part or extension of any other network. | It is an additional part of company's Intranet. |
| Communication takes place only within the organization that owns the network. | External users such as suppliers, customers, and partners are allowed to be a part of intranet to get information, updates, about the organization. |


