Computer Components
Computer Memory
Computer Network
Computer Virus
Number Systems
Shortcut Keys
Terms
- What is a Browser
- Google Chrome
- Mozilla Firefox
- Internet Explorer
- Windows
- Computer Ports
- program
- Printers
- Microphone
- Monitor
- Motherboard
- Incognito Mode
- Mouse
- Memory Card
- CD
- ID
- ISO
- character
- server
- Keyboard
- Remote
- webcam
- Data
- URL
- keypad
- hub
- File
- Bytes
- Exabyte
- Gb
- Kilobyte
- Megabyte
- Petabyte
- Terabyte
- What is HDD
- What is SSD
- Memory vs Storage
- Non-volatile memory
- What is M.2 SSD
- How To Reboot A Computer
- Multi-Level Cell
- NAND Flash Memory
- What is the lock screen
- Block Storage
- Universal Serial Bus
- VRAM
- Cloud Hosting
- CompactFlash card
- What is WAP
- Classification of Memory
- Hardware vs Software
- Uses of Computer
- Uses of Internet
- Abacus
- Best Proxy Servers
- SSL VS. TLS
- Web Console
- GPU
- Difference Between LAN and WAN
- SSD and HDD
- Computer
- Data Migration
- JEDEC
- MLC vs. TLC vs. SLC NAND Flash
- VirtualBox Installation
- Num Lock
- PC
- MAC
- Continuous Data Protection
- Persistent Storage
- What is Bit
- Software Definition
- What is a File System
- When was the first computer invented
- How many generations of the computer
- Minicomputer
- Fourth Generation of Computer
- What is a Username
- What is ALU
Questions
Computer Network
A network set up by connecting two or more computers and other supporting hardware devices through communication channels is called a computer network. It enables computers to communicate with each other and to share commands, data, etc., including the hardware and software resources.
Each computing device in a network is called a node or station. The nodes can be routers, personal computers, and servers. Data transformation is done via the network using rules known as protocols. The protocols are the set of rules which every node of the network should follow for transferring information over the wired or wireless network.
Working of a Computer Network
The nodes (like computers, switches, and modems) are the sources of generating and transmitting data. Then the link (a transmission media) is used to bond among the nodes.
By following the protocols, the nodes will transfer and receive data via connections. computer network architecture defines the design associated among these physical and logical components. It provides the definitions for the network's physical components, functional organization, protocols, and procedures.
Uses of Computer Network:
- It allows you to share resources such as printers, scanners, etc.
- You can share expensive software and database among network users.
- It facilitates communications from one computer to another computer.
- It allows the exchange of data and information among users through a network.
Popular Computer Networks:
- Local Area Network (LAN)
- Metropolitan Area Network (MAN)
- Wide Area Network (WAN)
Local Area Network (LAN):
As the name suggests, the local area network is a computer network that operates in a small area, i.e., it connects computers in a small geographical area like within an office, company, school, or any other organization. So, it exists within a specific area, e.g. home network, office network, school network, etc.
A local area network may be a wired or wireless network or a combination of both. The devices in a LAN are generally connected using an Ethernet cable, which offers an interface to connect multiple devices like router, switches, and computers. For example, using a single router, few Ethernet cables, and computers, you can create a LAN at your home, office, etc. In this network, one computer may act as a server and other computers, which are part of the network, may serve as clients.
Features of LAN
- The network size is small, which consists of only a few kilometres.
- The data transmission rate is high, ranging from 100 Mbps to 1000 Mbps.
- LAN is included in bus, ring, mesh, and star topologies.
- Some network devices connected to the LAN will be limited.
- If more devices are added than prescribed network may fail.
Benefits of LAN:
- It offers a higher operating speed than WAN and MAN.
- It is less expensive and easy to install and maintain.
- It perfectly fulfills the requirement of a specific organization, such as an office, school, etc.
- It can be wired or wireless or a combination of both.
- It is more secure than other networks as it is a small set up that can be easily taken care of.
Primary Functions of LAN:
- Sharing of files: It allows you to share or transfer files from one computer to another computer within the LAN. For example, in a bank, it can be used to send a file with the details of transactions of a customer from the server to clients.
- Sharing of printers: It also allows shared access to a printer, file servers, etc. For example, ten computers that are connected through LAN can use a single printer, file server, fax machine, etc.
- Sharing of Computational capabilities: It allows the clients to access to the computational power of a server, e.g., an application server as some applications which run on clients in a LAN may require higher computational capabilities.
- Mail and message related services: It allows sending and receiving mails between computers of a LAN. You are required to have a mail server for this.
- Database services: It also allows storing and retrieving data with the help of a database server.
Metropolitan Area Network (MAN):
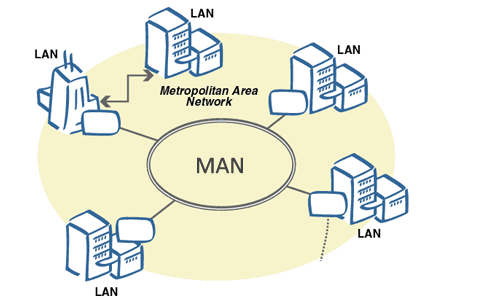
MAN is a high-speed network that spreads over a large geographical area such as a metro city or town. It is set up by connecting the local area networks using routers and local telephone exchange lines. It can be operated by a private company, or it may be a service provided by a company such as a local telephone company.
MAN is ideal for the people of a relatively large area who want to share data or information. It provides fast communication via high-speed carriers or transmission media such as copper, fiber optics, and microwaves. The commonly used protocols for MAN are X.25, Frame Relay, Asynchronous Transfer Mode (ATM), xDSL (Digital Subscriber Line), ISDN (Integrated Services Digital Network), ADSL (Asymmetrical Digital Subscriber Line), and more.
The area covered by MAN is larger than the LAN but smaller than a WAN. Its network ranges from 5 to 50 km. Furthermore, it also provides uplinks for connecting LANs to WANs and the internet. An organization can use a MAN to connect all of its LANs located at its different offices across the city.
Examples of MAN:
- Cable TV Network
- Telephone service provides that provide high-speed DSL lines
- IEEE 802.16 or WiMAX
- Connected fire stations in a city
- Connected branches of a school in a city
Features of MAN
- The size of the MAN is in the range of 5km to 50km.
- The MAN ranges from the campus to the entire city.
- The MAN is maintained and managed by either the user group or the Network provider.
- Users can achieve the sharing of regional resources by using MAN.
- The data transmission rates can be medium to high
Advantages of MAN:
- Less Expensive: It is less expensive to set up a MAN and to connect it to a WAN.
- High Speed: The speed of data transfer is more than WAN.
- Local Emails: It can send local emails fast.
- Access to the Internet: It allows you to share your internet connection, and thus multiple users can have access to high-speed internet.
- Easy to set up: You can easily set up a MAN by connecting multiple LANs.
- High Security: It is more secure than WAN.
Wide Area Network (WAN):
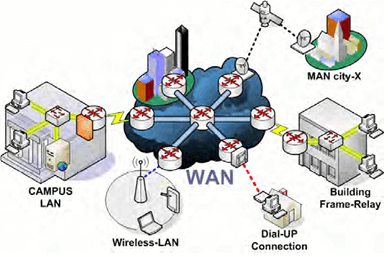
WAN extends over a large geographical area. It is not confined within an office, school, city, or town and is mainly set up by telephone lines, fiber optic, or satellite links. It is mostly used by big organizations like banks and multinational companies to communicate with their branches and customers across the world. Although it is structurally similar to MAN, it is different from MAN in terms of its range, e.g., MAN covers up to 50 Kms, whereas WAM covers distances larger than 50 Km, e.g., 1000km or more.
A WAN works by using TCP/IP protocol in combination with networking devices such as switches, routers, firewalls, and modems. It does not connect individual computers; rather, they are designed to link small networks like LANs and MANs to create a large network. The internet is considered the largest WAN in the world as it connects various LANs and MANs through ISPs.
The computers are connected to the wide area network through public networks, such as telephone systems, leased lines or satellites. The users of a WAN do not own the network as it is a large setup connecting the remote computer systems. However, they are required to subscribe to a service provided by a telecommunication provider to use this network.
Features of WAN
- Has a much larger capacity.
- We can share the regional resources by using WAN.
- They have more bit-rate errors.
- The transmission delay is, and hence they need more communication speed.
Advantages of a WAN:
- Large Network Range: It spans a large geographical area of 2000 km or more, e.g., from one country to another countries.
- Centralized data: It allows your different office branches to use your head office server for retrieving and sharing data. Thus, you don?t need to buy email servers, files server and back up servers, etc.
- Get updated files and data: It provides an ideal platform for companies who need a live server for their employees to exchange updated files within seconds.
- High bandwidth: It offers high bandwidth than a normal broadband connection. Thus, it can increase the productivity of your company by offering uninterrupted data transfer and communication.
- Workload Distribution: It helps distribute your workload to other locations. You can hire employees in different countries and assign them to work from your office.
Examples of WAN:
Internet
US defense department
Stock exchanges network
Railway reservation system
Big Banks' cash dispensers' network
Satellite systems
Visit for: Computer Network Tutorial
Standards for Good Network
Performance
The performance is measured using transmit time and response time. The network quality will be improved if the performance of the network is high.
Transmit time: The time taken to send a message from one device to another device is called as transmit time.
Response time: The time passed from inquiry to response is called as response time.
The total performance of the network depends on many factors, which include several users, Topology used in the network, and software and hardware used.
Reliability
The reliability in a network state whether the data delivery to the authorized and intended users was done correctly. The reliability of a network is one of the important factors for the delivery of data in the layers of the OSI model (Open System Interconnection).
Security
Network security involves the protection of data from unintended users' protection of data from damage and disruption. Security in a network avoids data breaches and data loss.
Network Topology
Topology: It refers to the physical arrangement and representation of all the nodes and components of the network. In general terms, Topology defines the structure of the entire network. The network topology is divided into five types. They are bus topology, star topology, ring topology, mesh topology, and tree topology.
1) Bus Topology:
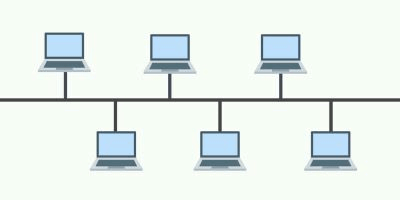
In this arrangement, the nodes (computers) are connected through interface connectors to a single communication line (central cable) that carries the message in both the directions. The central cable to which all the nodes are connected is the backbone of the network. It is called a bus. The signal in this arrangement travels in both directions to all the machines until it finds the recipient machine. It is easy to set up than other topologies as it uses only a single central cable to establish the network.
Advantages:
- Configuration of the network is easy.
- Less costly because a single cable is used to connect all nodes.
- The Bus topology supports a maximum of 10 Mbps speed by using the network's coaxial or twisted pair cables.
Disadvantages
- Due to the multipoint communication model, it is difficult to identify and isolate the faulty terminals.
- The reconfiguration will affect the network and slows down the performance.
- Signal interference is another drawback of the bus topology; if two or more nodes transmit the messages simultaneously, their signals will collide.
- A single node failure also causes the breakdown of the whole network.
2) Ring Topology:
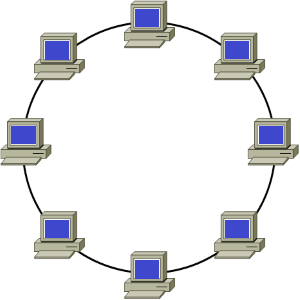
As the name suggests, in a ring topology, the computers are connected in a circular and closed loop. The message in this topology moves only in one direction around the ring from one node to another node and is checked by each node for a matching destination address. So, the data keeps moving until it reaches its destination. All nodes are equal; a client-server relationship does not exist between them. As the nodes are in the form of a ring, if one node fails to transmit the data, the flow of communication is severed.
Advantages:
- The data transfer and Communication are easy due to easy packet movement.
- The installation of the network and reconfiguration is easy.
- The presence of errors in links and faulty nodes can be easily identified and isolated.
- The reliability of the ring topology is more.
Disadvantages:
- As the data transmission is unidirectional, the packet will travel all the nodes to reach the destination.
- One node failure incurs damage to the entire network.
- Reconfiguration (adding new nodes) is easy but gets down the performance of the network.
- The delay is more in data transmission when the network contains more stations.
3) Star Topology:
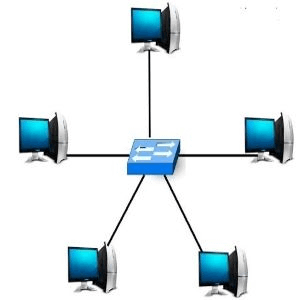
In this topology, all the computers are separately connected to a central node or connection point, which can be a server, a hub, a router, or a switch. This topology offers an advantage that if a cable does not work, only the respective node will suffer, the rest of the nodes will work smoothly. All data or messages that one node sends to another passes through the central hub.
This topology is easy to design and implement as well as it is easy to add additional nodes to the central node. The major drawback of this topology is that it is prone to bottleneck or failure at the central connection point, i.e., failure at the central node will affect the entire communication.
Advantages:
- Easy installation and reconfiguration.
- Less expensive as compared to mess Topology because the star requires less wiring.
- Easy to identify and isolate the faulty networks and links.
- When we add a new node, there is no interruption to other nodes in the network as the node is directly connected to the hub.
- Using star topology, we can achieve a high speed of data transfers.
Disadvantages
- If the hub fails, the whole network will not work.
- The star topology is more expensive than the bus topology because of the hub.
- We use more wire than that of the bus and ring topology.
- Every node completely depends on the hub for making decisions to transmit and process the data packets.
4) Mesh Topology
In a mesh topology, every device is connected to another device in a network using a point-to-point connection. The connection is generally known as a dedicated connection, as the link transports data between two devices. The number of links in a mesh topology is calculated using the formula below.
Military organizations use mesh topology to avoid breaks down in communications.
Many connections = n * (n - 1) /2. Here, "n" represents the number of nodes in a network.
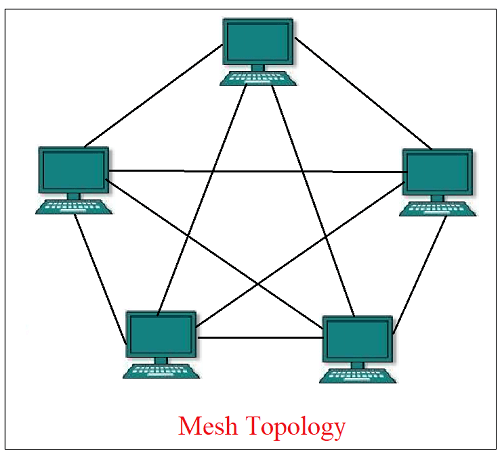
Advantages:
- Easy to transmit data.
- We can send data from many devices simultaneously. Mesh topology will handle much traffic as compared to other topologies.
- If one link is broken or remains faulty, data transfer can occur between nodes using other links. Hence data transmission is uninterrupted and reliable.
- The physical margins will not allow other persons to enter and access the messages.
- Fault detection and isolation are easy.
Disadvantages:
- The cabling used to construct the network is more.
- The installation cost is high compared to other topologies due to more wiring.
- The installation and reconfiguration are tough because of the presence of many links.
5) Tree Topology
Tree topology is the combination of star and bus topologies. The nodes are connected to a hub as in star topology, and all the star-connected nodes are placed in a bus topology. The tree topology is a hybrid connection.
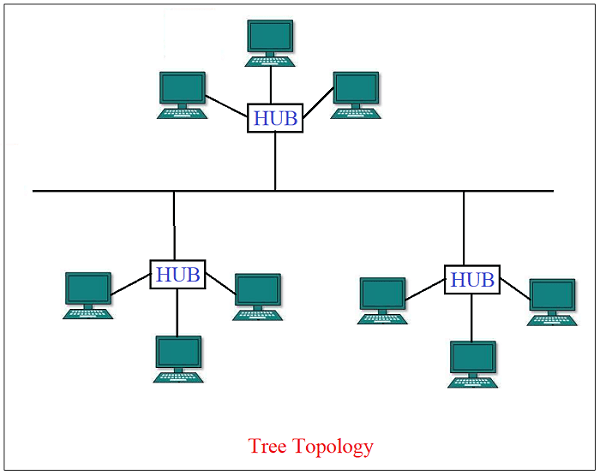
Advantages:
- Network extension is easy.
- The network is broken into smaller star-connected topology units. The nodes connected in a tree topology are easier to maintain.
- Fault detection and correction are easy.
- If one of the stars connected unit of nodes goes faulty, the other segments will not be affected and network can be runed with remaining nodes.
Disadvantages:
- The main disadvantage is that if the bus cable is damaged, the entire topology will not work.
- The management of Topology becomes easier when the number of nodes and star-connected topologies is increased in large numbers.
- The reconfiguration becomes difficult when new nodes are added.
Types of computer network architectures
Computer network architectures are of three types
1) Client-Server architecture
The architecture consists of a system that manages and delivers the services and resources via the network that the client requests. In the client-server architecture, each and every computer or process on the network is considered as a client or server. The servers (like computers) perform various operations to satisfy the client's requests.
The main methodology of client-server architecture is as follows:
- Initially, by using the network-enabled device, the client sends the request.
- Further, the network server acquires, agrees to, and processes the request.
- Lastly, the servers dispatch the reply information to the client.
Examples of client-server architecture include Email servers, Web servers.
2) Peer-to-peer architecture
In the Peer-to-Peer (P2P) architecture, linked computers have the same power and status. There is no central server for processing. Every peer may share some of its resources, like memory and processing power, with the entire computer network. Unlike the client-server architecture, peer-to-peer is a decentralized system in which files will be transferred from one system to another without using a central server.
3) Hybrid Network
The hybrid network architecture includes both client-server architecture and peer-to-peer architecture.


