Computer Components
Computer Memory
Computer Network
Computer Virus
Number Systems
Shortcut Keys
Terms
- What is a Browser
- Google Chrome
- Mozilla Firefox
- Internet Explorer
- Windows
- Computer Ports
- program
- Printers
- Microphone
- Monitor
- Motherboard
- Incognito Mode
- Mouse
- Memory Card
- CD
- ID
- ISO
- character
- server
- Keyboard
- Remote
- webcam
- Data
- URL
- keypad
- hub
- File
- Bytes
- Exabyte
- Gb
- Kilobyte
- Megabyte
- Petabyte
- Terabyte
- What is HDD
- What is SSD
- Memory vs Storage
- Non-volatile memory
- What is M.2 SSD
- How To Reboot A Computer
- Multi-Level Cell
- NAND Flash Memory
- What is the lock screen
- Block Storage
- Universal Serial Bus
- VRAM
- Cloud Hosting
- CompactFlash card
- What is WAP
- Classification of Memory
- Hardware vs Software
- Uses of Computer
- Uses of Internet
- Abacus
- Best Proxy Servers
- SSL VS. TLS
- Web Console
- GPU
- Difference Between LAN and WAN
- SSD and HDD
- Computer
- Data Migration
- JEDEC
- MLC vs. TLC vs. SLC NAND Flash
- VirtualBox Installation
- Num Lock
- PC
- MAC
- Continuous Data Protection
- Persistent Storage
- What is Bit
- Software Definition
- What is a File System
- When was the first computer invented
- How many generations of the computer
- Minicomputer
- Fourth Generation of Computer
- What is a Username
- What is ALU
Questions
Cloud Hosting
The method of outsourcing an enterprise's processing and storage capabilities to a service provider that provides its networking services in a utility model is cloud hosting.
The cloud vendor supervised the setup, cloud storage, protection and management, while customers will configure hardware and applications and scale servers online. Computing and storage services are dispersed in a cloud computing configuration through hundreds of virtual machines according to the load balance I / O demand.
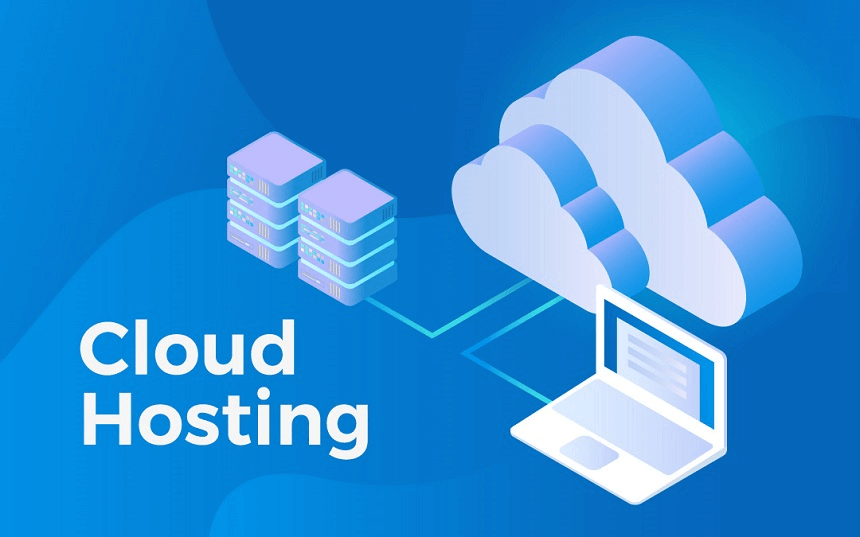
A cheaper alternative to the conventional dedicated server model that allows enterprises to develop and maintain their own data centers is the cloud storage model. Servers with dedicated hardware and virtual infrastructure exist on-premises throughout the conventional model, which can be an expensive operational cost for organizations.
Cloud hosting benefits
Cloud infrastructure provides companies with substantial financial and operating benefits, so they don't have to invest a lot in the actual direct cost of capital associated with data center acquisition and maintenance. IT also has the potential to scale more quickly, using only the services they need and paying for them. Moreover, long-term data storage becomes a more streamlined process, avoiding the expensive storage of discs and tape systems.
Data security advantages such as fast performance and disaster recovery are gained by utilizing cloud hosting services. Many companies use a hybrid model that combines on-site processing and storage capabilities with computation and storage in a cloud service framework.
Flexible and more cost-efficient scalability in developing apps, websites and other resources is one of the key advantages of using cloud computing services. As consumers are able to scale as needed, they are only paid for the facilities they use and do not pay for any unused facility. This payment system makes the cloud hosting a comparatively inexpensive storage process.
Although there are many advantages, it has some limitations also. Cloud protection challenges have attracted more interest as the pace of cloud adoption has increased. With data escaping the business data center, companies run the risk of fraud and degradation of intellectual property, violations of enforcement, lack of control into rogue workers' activities, and confidentiality breaches.
High supply, recovery point objective and recovery time objective (RTO) are additional factors to consider.
Top vendors/providers
As a technology model, cloud computing systems have fuelled a growth in the infrastructure under which a third-party vendor, usually with a pay-per-use system, provides a customer with the hardware, applications, servers, storage and networking facilities.
Amazon Web Services, the Google Cloud Portal, IBM Cloud and Microsoft Azure are common providers who offer cloud hosting. AWS, which provides comprehensive storage facilities and more areas and zones than most cloud vendors, is the leading competitor in the market. In recent years, Azure and Google have gained momentum.
AWS, along with Amazon Easy Storage Solution and Amazon Glacier for servers, provides the Elastic Compute Cloud to handle computing resources. For the enterprise, Google has the Google Compute Engine and Google Cloud Storage. Azure Virtual Machines and Azure Virtual Machine Scale Sets are supported by Microsoft Azure, and blob, log, and queue data are included in its data. A common cloud service is Microsoft Office 365.


